So, what's the big deal when comparing WPA2 Enterprise vs WPA2 Personal? Let's get right to it. It really boils down to one simple thing: are you using a single shared key or giving everyone their own individual login? With WPA2 Personal, everybody on the Wi-Fi uses the same password. On the other hand, WPA2 Enterprise is like a VIP list, giving each person their own unique credentials. Think of it as having one master key for your entire office versus giving every employee their own personalized keycard.
Choosing Your Wi-Fi Security Protocol
When you're setting up a wireless network, the security protocol you pick is your first and most important line of defense. The choice between WPA2 Enterprise and WPA2 Personal dictates exactly how users and their devices get access, which is a critical decision for any organization—from a busy corporate headquarters to a local coffee shop. This choice directly shapes how you’ll handle security challenges like Bring Your Own Device (BYOD) policies, a common sight in today's Education, Retail, and BYOD Corporate sectors.
WPA2 Personal is everywhere, mostly because it's so incredibly simple to set up. It is, by a huge margin, the most common Wi-Fi security method in the world, with roughly 99% of WPA2 deployments being the "Personal" version. This is all down to its easy, single pre-shared key (PSK) setup. You can discover more insights about global Wi–Fi security trends to see just how dominant it is.
But that simplicity comes with a cost, especially in a business setting. A single shared key creates some serious risks. WPA2 Enterprise, on the other hand, was built specifically for these scenarios. It works with an authentication server to make sure every connection is verified with individual credentials, giving you the kind of detailed control that is essential in Education, Retail, and corporate settings, especially when using professional gear from folks like Cisco and Meraki.
Let's break down the fundamentals with a quick comparison.
WPA2 Personal vs Enterprise At a Glance
The table below offers a friendly snapshot of the core differences between the two protocols, from how they handle authentication to where they fit best.
| Feature | WPA2 Personal | WPA2 Enterprise |
|---|---|---|
| Authentication Method | Pre-Shared Key (PSK) – one password for all users | 802.1X/EAP – unique credentials for each user |
| Security Level | Lower – vulnerable if the shared key is compromised | Higher – individual credentials, centralized control |
| User Management | Difficult – changing the PSK requires updating all devices | Easy – add/remove users from a central directory |
| Best For | Homes, small offices, simple guest networks | Medium to large businesses, schools, public venues |
| Infrastructure | Simple – just an access point | Complex – requires a RADIUS authentication server |
As you can see, the decision isn't just about security; it's about scalability, management, and control. WPA2 Personal is great for simplicity, but WPA2 Enterprise is built for professional, centrally managed environments.
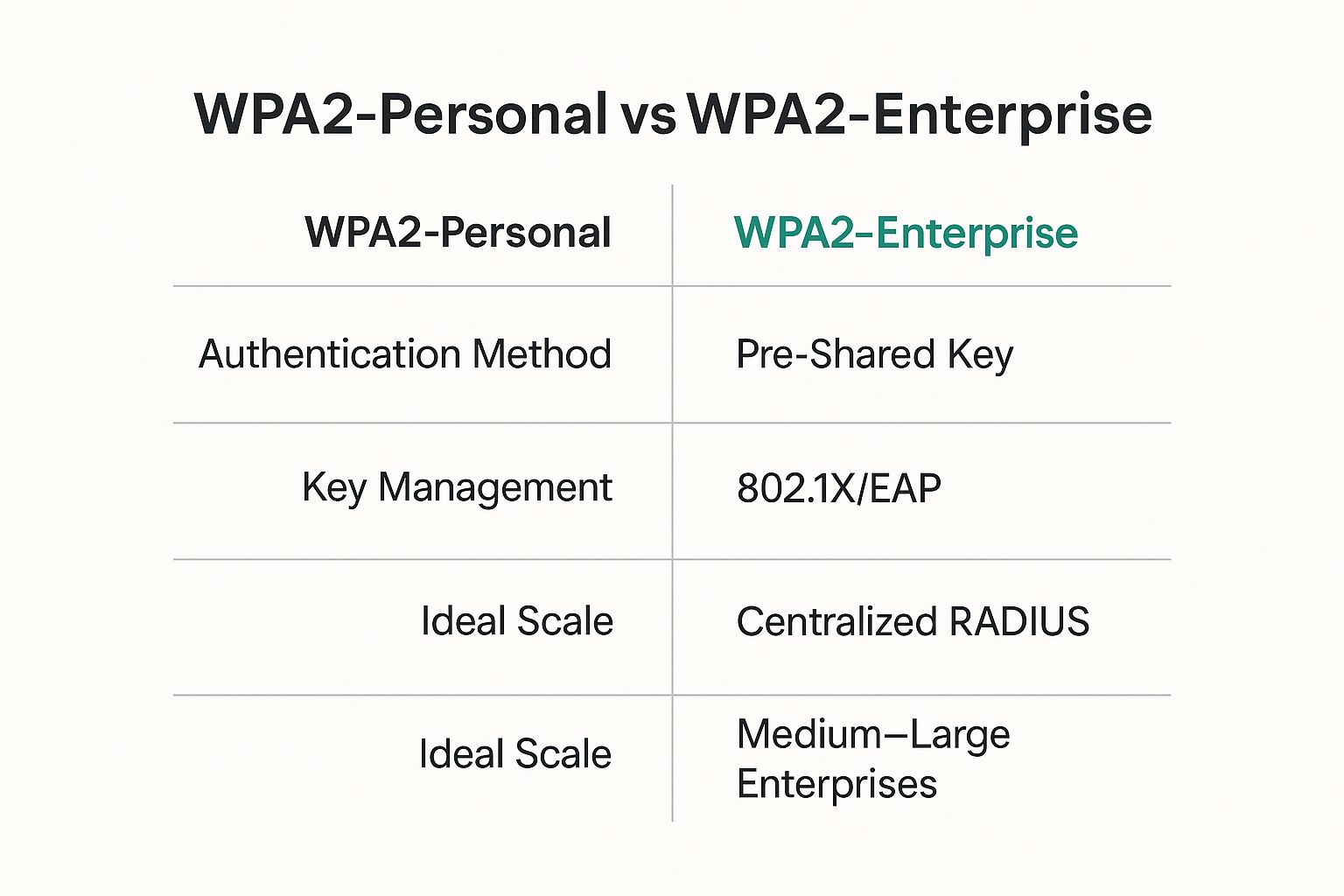
The infographic above drives this point home. Personal mode is for small-scale, simple use cases. Enterprise mode is for secure, centralized management in bigger, more complex environments. This difference is especially important when you’re using professional-grade hardware from vendors like Cisco or Meraki. WPA2 Enterprise is what unlocks their more advanced features, letting you manage everything from Captive Portals to sophisticated Authentication Solutions like IPSK and EasyPSK.
The Simplicity and Risks of WPA2 Personal
Let’s talk about the Wi-Fi security you’re probably most familiar with: WPA2 Personal. It's the standard for most homes and small businesses, and its biggest selling point is sheer simplicity. You set a password, share it, and people can get online in seconds. For a home network or a small office with just a few trusted people, this works just fine.

This method is also known as WPA2-PSK, which stands for Pre-Shared Key. Everyone uses the same key to unlock the network. But that simplicity is exactly what makes it a massive headache for larger organizations, especially in sectors like Education, Retail, or any corporate environment that supports BYOD (Bring Your Own Device).
The Shared Password Problem
In a business setting, that single shared password quickly turns into a major liability. What happens when an employee leaves? They still have the key to your entire wireless network. Your only real option is to change the password for everyone.
This creates a logistical nightmare. Every single device—laptops, printers, tablets, even specialized equipment—has to be reconfigured. It’s not just a pain; it’s a gaping security hole that often stays open way too long. The longer that old password remains active, the higher the risk of a breach.
Critical Security Weaknesses in Business
Relying on one password for everyone introduces some serious vulnerabilities that are simply unacceptable for any organization that handles sensitive data.
- No Individual Accountability: With everyone using the same credentials, there’s no way to track who is doing what on your network. If a security incident happens, figuring out who was responsible is next to impossible.
- Widespread Compromise: If that single password gets leaked or cracked—maybe from a phishing attack or someone writing it down—your entire network is wide open. One compromised key gives an attacker access to shared files, internal servers, and customer information.
- Difficult Offboarding: As we covered, revoking access for a former employee is a huge hassle. That delay gives a disgruntled ex-employee a perfect window to cause some real damage.
- Poor Scalability: As your organization grows, trying to manage one password across dozens or hundreds of devices becomes completely untenable. It just doesn't scale.
A single shared key means a single point of failure. In a business environment, especially those in Retail or Education, this model doesn't just fail to scale—it actively invites security breaches by eliminating individual user control.
For businesses that have invested in professional-grade hardware from vendors like Cisco or Meraki, using WPA2 Personal is like putting a cheap padlock on a bank vault. You're completely ignoring the advanced security capabilities you paid for. While it’s the default for home use, the fundamental difference in the wpa2 enterprise vs wpa2 personal debate is that the former was built from the ground up for secure, scalable business networks. For a deeper look into these differences, you can review our complete guide on WPA2 Personal vs Enterprise security.
Why WPA2 Enterprise Is the Go-To for Business
When security is non-negotiable, WPA2 Enterprise is the definitive standard for businesses. It was built from the ground up for environments where a simple shared password just won't cut it—think corporate headquarters, sprawling retail locations, or university campuses. This protocol completely overhauls the way a network grants access.

Unlike its 'Personal' sibling, WPA2 Enterprise throws the whole idea of a shared password out the window. Instead, it’s all about individual accountability. Every single user connects with their own unique credentials, which is the fundamental difference in the wpa2 enterprise vs wpa2 personal debate.
This individual authentication isn't just handled by the access point. It relies on a separate, dedicated authentication server, most commonly a RADIUS (Remote Authentication Dial-In User Service) server. When you try to connect, the access point doesn't make the decision; it passes your credentials over to the RADIUS server, which checks them against a central user database before giving the green light.
The Power of Individual Authentication
This approach gives you a level of control and security that a single shared password could never dream of. Just think about a common headache: an employee leaves the company. On a WPA2 Personal network, you have to change the Wi-Fi password and tell everyone the new one. With WPA2 Enterprise, an admin simply disables that one user's account. Their access is gone, instantly, without disrupting a single other person.
The ability to revoke access for a single user without impacting the entire network is a game-changing security feature. It transforms network management from a reactive chore into a proactive security strategy.
This is exactly why WPA2 Enterprise is so crucial for modern businesses. If you're managing a BYOD (Bring Your Own Device) policy, it’s the only way to ensure only authorized employees on approved devices can get online. This granular control is the bedrock of a secure and manageable wireless network. Our guide on enterprise Wi-Fi access points digs deeper into how the right hardware supports these advanced security models.
Built for Scalable and Secure Environments
WPA2 Enterprise is designed for serious control. By using the 802.1X authentication protocol, it forces every connection attempt to be individually verified by that backend RADIUS server. This server often ties directly into corporate directories like Microsoft's Active Directory, giving you sophisticated, policy-based access control.
This system truly comes alive in environments with hardware from vendors like Cisco or Meraki, which are built to handle these powerful capabilities. The benefits are immediate and substantial:
- Enhanced Security: Unique credentials for every user mean no more risks from leaked or stolen shared passwords.
- Centralized Management: Admins can manage all user access from a single dashboard, making onboarding and offboarding a breeze.
- Detailed Auditing: Every connection attempt is logged. This gives you a clear audit trail to monitor network activity and spot potential security issues before they become problems.
- Scalability: The architecture scales effortlessly from a few dozen users to thousands across multiple sites, making it perfect for growing businesses in Education and Retail.
In the end, WPA2 Enterprise delivers the robust framework needed to lock down a modern network. It turns your Wi-Fi from a potential vulnerability into a controlled, managed, and secure business asset.
Taming Wi-Fi Security with Modern Authentication
WPA2 Enterprise sets a high bar for security, but let's be real—setting up and managing a traditional RADIUS server can be a headache. Thankfully, you don't have to be a network wizard anymore. Modern Authentication Solutions have stepped in to make enterprise-grade Wi-Fi security simpler and more accessible for everyone.

These tools are the missing link between the powerful security of the protocol and its day-to-day management. They take the best parts of WPA2 Enterprise—individual user credentials and centralized control—and wrap them in a package that's far easier to manage, especially on popular platforms from Cisco and Meraki.
The Smart Simplicity of IPSK and EasyPSK
What if you could give every single user or device its own unique password for the Wi-Fi network? And what if you could do it without wrestling with individual certificates or complicated onboarding? That’s exactly what IPSK (Individual Pre-Shared Key), also known as EasyPSK, delivers. It’s a clever blend of a simple password with serious enterprise-level security.
Here’s how it works: instead of one password shared by everyone, a management platform generates a unique key for each authorized device or user automatically. This is a huge win for BYOD policies, especially in corporate offices and across the Education sector. If an employee loses their phone or a student leaves the school, you just revoke their specific key. The device is instantly blocked from the network, and nobody else is affected.
IPSK really gives you the best of both worlds. You get the individual accountability and quick-and-easy access revocation of WPA2 Enterprise, but you get to skip the backend complexity. It's an ideal solution for any organization that needs strong, scalable security without a dedicated IT army to manage it.
More Than Just a Welcome Screen: The Role of Captive Portals
When most people hear Captive Portal, they think of the login page at a hotel or coffee shop. But in a secure network, their role is so much bigger. A well-implemented captive portal acts as a secure front door for your network, managing how both employees and guests get online.
For an employee bringing their own device (BYOD), the captive portal is the first checkpoint. It can prompt them to log in with their company credentials, accept an acceptable use policy, and even kick off the process of automatically assigning them an IPSK. For guests in a Retail store, it's the perfect chance to get them connected securely while also offering promotions or gathering marketing insights. If you're exploring this for your business, our guide on how to set up guest Wi-Fi is a great place to start.
When you bring it all together, pairing WPA2 Enterprise with modern Authentication Solutions like IPSK and a smart captive portal strategy creates a Wi-Fi environment that is secure, easy for people to use, and incredibly simple to manage.
WPA2 in the Real World: Where the Rubber Meets the Road
Knowing the technical differences between WPA2 Enterprise and WPA2 Personal is a good start, but seeing them in action is what really makes the choice obvious. The best security protocol isn't just theory; it’s about solving real problems in specific environments. Let's walk through a few common situations where the difference is night and day.

The Education Sector: Taming Campus-Wide Connectivity
Picture a university campus. You have thousands of students, professors, and staff all clamoring for Wi-Fi. Trying to manage this with WPA2 Personal would be an absolute disaster. A single shared password would get passed around instantly, and you'd have no way to kick off graduated students or former employees without changing the password for everyone.
This is exactly where WPA2 Enterprise, running on solid hardware from providers like Cisco or Meraki, becomes indispensable. Every single user gets their own login, usually tied to their existing university account. This gives the IT team incredible control:
- Grant specific access levels: Students can be on one network, while faculty get access to a more secure one with sensitive resources.
- Revoke access instantly: When a student graduates or an employee leaves, their access is cut off with a single click. No more mass password changes.
- Handle BYOD securely: The network can safely manage thousands of personal laptops and smartphones connecting every day without compromising security.
Retail Environments: Protecting Transactions and Guests
For any retail store, network security is everything. You've got Point-of-Sale (POS) systems handling credit card data, often on the same network that offers guest Wi-Fi. Using one shared password for both is just asking for a data breach and won't get you anywhere near compliance standards.
WPA2 Enterprise is critical here because it allows for strict network segmentation. Your POS terminals, inventory scanners, and employee devices connect to a heavily secured network using individual credentials. At the same time, you can offer a separate guest network through a Captive Portal, keeping public traffic completely isolated from your core business operations.
In Retail, you're juggling two critical tasks: protecting customer data at all costs and giving shoppers a great experience. WPA2 Enterprise is the only way to do both, by building a wall between secure operational traffic and public access.
Corporate Offices: Solving the BYOD Headache
The modern office is built on BYOD (Bring Your Own Device). Employees need to connect their personal phones, tablets, and laptops to the company Wi-Fi. Relying on a shared password for this is an administrative nightmare and a massive security hole.
With WPA2 Enterprise, you can use powerful Authentication Solutions like IPSK or EasyPSK. This lets IT issue a unique, private key for each employee's device, giving them secure access without the hassle of managing complex certificates. If an employee leaves, you just revoke their keys, and the network is secured immediately. To learn more about these methods, our overview of different security keys for Wi-Fi breaks it down further.
These real-world examples make it clear. For any organization in the Education, Retail, or Corporate world, WPA2 Enterprise isn't just a "nice-to-have." It's a fundamental requirement for building a secure, scalable, and manageable wireless network.
Does Enterprise Security Hurt Wi-Fi Performance?
A common question I hear when discussing WPA2 Enterprise vs. WPA2 Personal is whether the beefed-up security slows things down. It’s a fair question, especially for busy environments like Retail stores or university campuses. Thankfully, the answer is a resounding no—it's a myth.
The speed of your Wi-Fi connection isn't determined by the authentication method. Once a device is connected, both WPA2 Enterprise and Personal use the very same AES encryption to secure the data flying through the air. Performance experts have confirmed that there's no real-world difference in throughput between the two. Your Wi-Fi will feel just as quick either way. For a deeper dive into the technicals, check out this discussion on WPA2 encryption performance.
The only place you'll find a difference is during the initial connection—the "handshake" where a device first joins the network. WPA2 Enterprise adds a quick check-in with a RADIUS server to validate the user's unique credentials.
The Millisecond Handshake
So, how long does this extra step take? On a properly configured network using hardware from vendors like Cisco or Meraki, we're talking about milliseconds. It happens so fast that no human would ever notice the difference.
You simply won't see lag or buffering because you opted for a more secure network. Whether it's an employee connecting their personal device in a BYOD setup or a visitor logging in through a Captive Portal, the experience is instant. This tiny, one-time authentication overhead is an incredibly small price to pay for the huge security upgrade you get.
The idea that WPA2 Enterprise slows down your Wi-Fi is a persistent myth. The reality is that the initial authentication is a one-time, millisecond event that has no impact on the user's ongoing browsing, streaming, or download speeds.
At the end of the day, you can deploy enterprise-level security without compromising on the fast Wi-Fi experience everyone expects. Modern tools like IPSK and EasyPSK make this process even smoother, delivering secure connections that are faster and simpler than ever.
Common Questions About WPA2 Security
Choosing between WPA2 Enterprise and WPA2 Personal often brings up a few key questions. Let's tackle some of the most common ones I hear from people trying to secure their networks.
Can I Use WPA2 Enterprise at Home?
You technically can, but it's like using a sledgehammer to crack a nut. WPA2 Enterprise relies on a RADIUS server for authentication, which adds a layer of complexity that's simply not needed for the average home.
For home networks, a strong, unique passphrase on WPA2 Personal is more than sufficient. Stick with Personal mode—it's simpler and provides robust security for your family's devices.
Is WPA3 Making WPA2 Obsolete?
WPA3 is definitely the future of Wi-Fi security, offering some serious upgrades over WPA2 in both its "Personal" and "Enterprise" versions. That said, WPA2 isn't going away overnight.
It's still the most widely used protocol across the vast majority of devices out there today. For anyone managing a network right now, a solid understanding of WPA2 is absolutely essential.
Does WPA2 Enterprise Require a Dedicated Physical Server?
Not anymore, thankfully. In the past, you needed a dedicated, on-premise server to run RADIUS, which was a major hurdle for many organizations.
Today, cloud-based RADIUS services have changed the game. Solutions from providers like Cisco Meraki handle all the backend complexity for you, making WPA2 Enterprise a practical choice even for businesses without a large IT department. To really lock things down, it's also important to understand what multi-factor authentication is and how it adds a critical layer of defense to user logins.
Ready to deploy enterprise-grade Wi-Fi without the headache? At Splash Access, we specialize in making powerful network security simple and effective for your users. Explore our solutions at https://www.splashaccess.com.



