Hey there! If you're managing a network, especially with the awesome gear from Cisco Meraki, you know that keeping an eye on every device that connects is a huge deal. It’s not just about being tidy—it's super important for security and making sure everything runs smoothly. Think of MAC address tracking as giving each phone, laptop, and tablet its own unique, digital name tag.
Why Tracking MAC Addresses is Still a Big Deal for Your WiFi
Ever found yourself in charge of a WiFi network at a busy school, a buzzing retail shop, or a corporate office juggling a Bring-Your-Own-Device (BYOD) policy? If so, you totally get it. You need to know exactly what’s happening on your network. This is where tracking MAC addresses becomes your new best friend, turning what sounds like a geeky chore into a brilliant way to see what's going on and keep your network safe.
It's really the foundation for a great wireless experience. This simple practice is what makes everything from a smooth Captive Portal login to more advanced Authentication Solutions like Individual Pre-Shared Keys (IPSK) possible.
From a Simple ID to Serious Security
Every MAC address has something called an Organizational Unique Identifier (OUI), which tells you who made the device. This might not sound like a big deal, but it has real-world security implications. A clever attacker could use this info to figure out what kind of devices are on your network and look for known weaknesses. This is exactly why just tracking MAC addresses isn't quite enough; you need to team it up with stronger security measures.
The Cisco Meraki dashboard is a dream for this, giving you a crystal-clear, all-in-one view of every connected device.
This "single pane of glass" view lets IT admins see everything at a glance, which makes jobs like fixing a slow connection or making sure security rules are followed way, way easier.
Here’s a pro tip: by integrating a solution like EasyPSK, you can give each device's MAC address its own unique, easy-to-cancel password. This takes your security to a whole new level, leaving that old-school single shared password in the dust. It gives you the kind of detailed control you really need for today's complex networks. To see how this fits into the bigger picture of modern security, you can learn more about how https://splashaccess.com/what-is-wpa-3/ is changing the game.
How Different Sectors Win with MAC Address Tracking
Let's get practical. Here’s a quick peek at how different industries are using MAC address tracking with their Cisco Meraki setups.
| Sector | Primary Benefit | Real-World Scenario |
|---|---|---|
| Education | Controlled Access | Making sure only registered student and staff devices can get on the campus WiFi, keeping unauthorized users out. |
| Retail | Anonymized Analytics | Understanding customer foot traffic by tracking unique devices over time to improve store layout and know when to schedule more staff. |
| BYOD Corporate | Security & Accountability | Guaranteeing every personal device is accounted for and follows security policies before it gets access to the company network. |
| Hospitality | Seamless User Experience | Letting guests reconnect to the hotel WiFi automatically on their next visit without having to type in their details all over again. |
As you can see, the uses are super practical and bring real value, from beefing up security in a school to making a customer's day in a hotel. It's a foundational tool with a ton of benefits.
Getting Your Meraki Dashboard Set for Success
Before you jump into fancy authentication solutions, you've got to get your house in order. That journey starts right inside your Cisco Meraki dashboard. A few key tweaks here are what will make effective MAC address tracking a reality. This isn’t just a techy to-do list; it’s about creating a custom network experience for your users, whether they're students on a campus, shoppers in a Retail store, or employees in a BYOD Corporate environment.
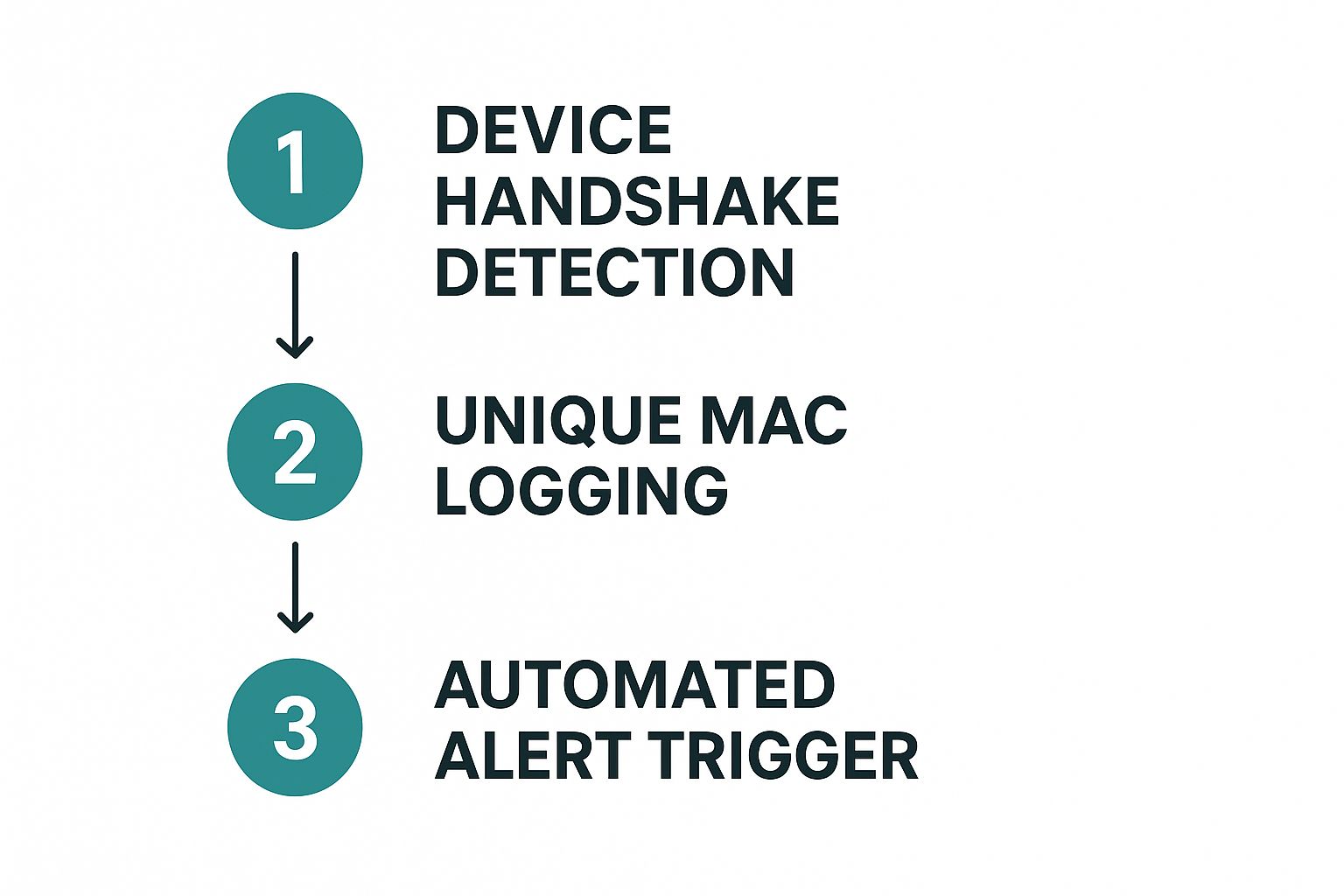
The very first thing your users will meet is your Splash Page, often called a Captive Portal. Think of it as your network’s digital welcome mat. Setting one up is a must because it’s the exact moment you grab the device's MAC address before letting it onto the network. To make this happen, you'll need to tweak the "Association requirements" on your SSID to make sure every device gets sent to this portal first.
Setting Up Your Digital Front Door
Pop over to your Meraki dashboard and head to the "Wireless" section, then "Access control" for the SSID you're working with. This is where you'll find the options to turn on a click-through or a sign-on splash page. This is the cornerstone of the whole setup.
While you're in there, you can also tell the dashboard to send logs to an external syslog server. This step is super important if you want to keep connection data for more detailed analysis down the road.
Setting this up lets you push all your event logs to a separate, dedicated server. It’s a must-do for anyone who's serious about advanced tracking and reporting that goes beyond what the standard Meraki dashboard offers. Once that first handshake happens at the portal, the rest is smooth sailing: the device connects, its unique MAC is logged, and any rules you’ve created can be applied automatically.
Getting these initial settings right is what opens the door for powerful authentication systems like IPSK or EasyPSK, which we'll chat about next.
Taking Authentication to the Next Level with a Captive Portal
While Cisco Meraki has some fantastic built-in tools, you can seriously supercharge your network by adding a specialized captive portal. We're not just talking about passively tracking MAC addresses anymore; this is about building an active strategy that gives you way more control and insight.
The best way to think about a Captive Portal is as a smart gateway to your network. It’s the first thing users see, making it the perfect spot to automate MAC address capture right when they log in. You can show them your terms and conditions, offer different ways to connect, and smoothly collect their device's MAC address behind the scenes.
Customizing Access for Your World
One size never fits all, especially when it comes to WiFi access. A good captive portal lets you create Authentication Solutions that actually make sense for your specific space.
I've seen this work wonders in a few key areas:
- Education: In schools and universities, security is everything. This is where an IPSK (Individual Pre-Shared Key) or EasyPSK system is a total game-changer. Each student gets a unique key for their devices, which ties their MAC address directly to who they are. This means rock-solid security and clear accountability.
- Retail: For a coffee shop or a retail store, you want a smooth, easy experience for your guests. Offering a simple one-click form or social media login is a great way to capture guest data for marketing while making it incredibly simple for shoppers to get online.
- BYOD Corporate: When you're managing a BYOD Corporate network, it's a constant balancing act between making things easy and keeping things secure. A captive portal can connect with your company's existing user directories to check employee credentials before letting a personal device onto the network, making sure every single connection is authorized.
This kind of flexibility is what separates a good network from a great one. You get to build a secure, branded, and easy-to-use experience that’s perfectly tailored for your audience. If you're keen to explore this further, we have a complete guide on how to elevate your Cisco Meraki network with SplashAccess for captive portals and authentication.
Expert Insight: Automating your MAC address tracking is more than just a time-saver. It's a key part of keeping your network healthy and secure. When a problem pops up, an admin can use their MAC address list to instantly find a misbehaving device that's slowing things down or even isolate a threat like ransomware.
On top of that, having a detailed log of which device was where and when is a lifesaver for compliance. It plays a massive role in spotting and stopping security incidents by linking specific hardware directly to network activity.
Putting Your Tracked Data into Action
Alright, so you’ve set up your Cisco Meraki network and you're successfully tracking MAC addresses. That's a fantastic first step! But just collecting data isn't the final goal—the real magic happens when you turn those raw numbers into an awesome security and operational tool.
This isn’t just about having a list of addresses; it’s about making your network truly work for you. Using a device's unique ID for an audit trail has been a core part of network management for ages. For example, experienced network admins have relied on packet captures for years, linking MAC addresses to web traffic to create a solid history for deep security investigations and troubleshooting. If you're interested in the techy side, you can discover more insights on how MAC addresses provide a reliable audit trail.
From Data Points to Real-World Wins
Let's get practical. How does tracking MAC addresses actually help you day-to-day? It all comes down to what you need, whether you're running a school, a retail store, or a corporate office.
Here’s where this data becomes genuinely priceless:
- Education Sector: Imagine a security incident happens on campus. With a log of every MAC address that connected to your WiFi, you can find the exact device involved in seconds. This lets your IT team cut it off from the network before any more trouble can start.
- Retail Environments: In a store, this data gives you incredible, anonymous insights into what your customers are doing. You can track foot traffic, see how many visitors are new versus returning, and understand how long people hang out in certain areas. This is pure gold for optimizing your store layout and staffing.
- BYOD Corporate Networks: For any office with a Bring-Your-Own-Device policy, troubleshooting can be a real pain. When an employee complains about a bad connection, IT can use the device's MAC address to find it instantly on the Meraki dashboard and start figuring out the problem without all the usual guesswork.
Taking Active Control of Your Network
This isn't just about passively watching what happens. With the reporting features from a platform like Splash Access, you can see all this activity visually, set up security alerts for unusual behavior, and even kick a specific device off the network with a single click.
If a student's laptop is lost or a corporate phone gets stolen, you can immediately add its MAC address to a blocklist. That device is now completely barred from ever connecting to your network again—a simple, powerful, and instant security win. This is a must-have feature for any organization.
At the end of the day, you're turning a simple list of hardware addresses into a dynamic, smart tool. It’s the foundation for building a smarter, more secure WiFi experience for everyone. If you're just starting out, it's also worth brushing up on the basics of a solid wireless setup—feel free to check out our guide on how to set up guest WiFi for some foundational tips.
Navigating Privacy and MAC Randomization
Let's be real: while tracking MAC addresses is a powerful tool in a Cisco Meraki setup, it comes with genuine privacy considerations. You can't just hoover up data without a plan. Modern devices now use MAC randomization to protect user privacy, which, from an admin's point of view, can throw a bit of a wrench in the works. But don't worry, it’s a challenge you can definitely handle.
This is where your Captive Portal steps up to do more than just open the door to the internet. It becomes your platform for being open and honest. It's so important to have a crystal-clear privacy policy that explains what data you're collecting and how you're using it. Being upfront builds trust, which is priceless whether you're running a network for a school in the Education sector, a Retail space, or a BYOD Corporate environment.
Getting Around MAC Randomization
So, what do you do when a device keeps changing its MAC address? The trick is to stop focusing on the hardware and start authenticating the person. By putting stronger Authentication Solutions in place, you can give each user a consistent digital identity that sticks around, no matter what their device's MAC address is today.
Solutions like IPSK or EasyPSK are fantastic for this. A user connects with a unique pre-shared key, and that key is tied directly to them, not just to a temporary MAC address. It’s a simple way to keep a consistent and secure handle on who's who. For places that need even more detailed control, setting up a Cisco Meraki RADIUS server with group policy support can give you that deep, granular management you're looking for.
The goal here is simple: establish a reliable, user-based identity that lasts. A randomized MAC address is only a problem if it's the only thing you're tracking. Once you require a login through a portal or a unique key, you create a much more stable and secure way to identify who is on your network.
As the digital world keeps changing, staying in the loop on topics like the shift towards first-party data and privacy is key. It gives you the bigger picture and helps you make smarter decisions when dealing with MAC randomization.
Finally, don't forget about your data retention policy. Figure out exactly how long you need to store MAC address logs for your operations or security, and then stick to that schedule. This shows you respect user privacy by not holding onto data forever, all while keeping your network locked down tight.
Common Questions About MAC Address Tracking
When you're diving into MAC address tracking in a Cisco Meraki environment, a few practical questions always pop up. It doesn't matter if you're managing a campus network for Education, a busy storefront in Retail, or a BYOD Corporate setup—the main challenges are often pretty similar. Let's walk through some of the most common ones I hear from my fellow network admins.
Can I Block a Device Using Its MAC Address?
Yes, you sure can! This is one of the most direct security controls you have at your fingertips. You can easily create blocklists based on a device's unique MAC address, either right in the Meraki dashboard or through a more advanced Captive Portal solution like Splash Access.
Think about a real-world situation: a student's tablet is stolen, or an employee misplaces their phone. You can immediately add that device's MAC to a deny list. The moment you do, it's totally cut off from your WiFi network. It’s a simple, fast, and incredibly effective way to protect your network.
How Does MAC Tracking Work with Guest WiFi?
Guest WiFi is a perfect example of where MAC tracking really shines, especially in a Retail setting. When a shopper connects to your network through a Captive Portal, the system logs their device’s MAC address during that initial digital handshake.
This gives you a powerful, privacy-friendly way to get great analytics. You can see things like:
- New vs. returning visitors
- Peak traffic hours
- Average time spent in the store
You get a clear picture of customer behavior and foot traffic, all without needing to collect any personal data. It’s a win-win: customers get free WiFi, and you get valuable business insights.
The real security upgrade comes when you layer on your Authentication Solutions. A standard WPA2-PSK password means everyone uses the same key—a huge security risk! But if you implement an IPSK or EasyPSK system, every single user gets their own unique key. This is a total game-changer because you can tie each MAC address to a specific key, giving you the power to grant or revoke access on a per-device basis.
What About Firewalls and Security?
People often ask me how MAC tracking fits into their bigger security strategy. The two work together like a dream. By identifying and logging every device that connects, you're essentially feeding your security systems the exact data they need to be effective.
Knowing exactly which devices are on your network at any given moment is a fundamental piece of the security puzzle. If you want to dig a bit deeper into network defenses, it’s worth understanding what a stateful firewall is and how it works with device tracking to build a much stronger, more resilient security setup.
Ready to take control of your network? Splash Access provides advanced captive portal and authentication solutions for Cisco Meraki, making MAC address tracking simple and powerful. Get started today at https://www.splashaccess.com.