Hey there! A solid network security policy template is your secret weapon for protecting your digital world, but let's be real—it's how you use it that counts. Think of it less like a stuffy, formal document and more like a friendly rulebook for how your organization handles everything from guest Wi-Fi to employee device connections. It’s all about creating a clear, secure game plan before a crisis forces your hand.
Why a Modern Network Security Policy Is a Must-Have
Let's be honest—"winging it" with network security is a surefire way to land in hot water. In today's hyper-connected world, a robust network security policy isn't just a technical doc for the IT department; it's a vital business asset. It acts as a clear roadmap that protects your sensitive data, ensures you can keep the lights on, and helps you build a brand that people trust.
The stakes have never been higher. Cybercrime has ballooned into a massive industry, with global losses projected to rocket from $6 trillion in 2024 to an eye-watering $10.5 trillion by 2025. A huge part of this is the explosion in sophisticated zero-day attacks, which leaped from an average of 21 per year to 66 in just a single year recently.
Beyond the Basics: A Policy Built for Real-World Scenarios
A truly effective policy moves past generic rules and gets into the nitty-gritty of how people actually interact with your Wi-Fi and network every day. This is where the right tools, like those from awesome providers such as Cisco Meraki, become total game-changers, giving you the power to actually enforce the rules you've written down.
To make this practical, your policy needs to define how you'll handle different types of access. Just think about these common situations:
- Retail Shops: How do you offer free Wi-Fi to shoppers without putting your point-of-sale systems at risk? Your policy can mandate a separate, isolated guest network using a Captive Portal.
- Education Campuses: Schools have to juggle access for students, faculty, and guests, all of whom need different permissions. The policy should spell out the rules for content filtering and access levels, often enforced with modern Authentication Solutions.
- Corporate BYOD: When an employee connects their personal laptop or phone, how do you keep company data from walking out the door? A clear Bring-Your-Own-Device (BYOD) section is essential for secure onboarding, often managed with solutions like EasyPSK.
Core Components of a Network Security Policy
Every effective network security policy is built on a few essential pillars. This table breaks down those core components, giving you a quick reference for the key areas you absolutely need to address.
| Policy Component | Objective and Scope | Example Application |
|---|---|---|
| Acceptable Use Policy (AUP) | Defines how employees and guests can use the network. Sets clear boundaries on prohibited activities. | Prohibiting the use of peer-to-peer file-sharing applications on the corporate network to reduce malware risk. |
| Access Control Policy | Specifies who can access which network resources and under what conditions. Implements the principle of least privilege. | Restricting the finance team's access to only financial servers and applications, blocking access to developer environments. |
| Guest Network Access | Outlines rules for non-employee access, ensuring guest traffic is isolated from the internal corporate network. | Requiring all guest Wi-Fi users to agree to terms and conditions via a Captive Portal before being granted internet-only access. |
| BYOD Policy | Governs the use of personal devices to access company resources, including security requirements for those devices. | Mandating that any personal smartphone accessing company email must have a passcode and up-to-date security software installed. |
| Incident Response Plan | Details the step-by-step process for identifying, containing, and recovering from a security breach. | If a ransomware attack is detected, the plan dictates immediately isolating the infected machine from the network to prevent spread. |
By addressing each of these areas, you create a comprehensive framework that leaves little room for ambiguity and provides a strong defensive posture.
The Power of Smart Authentication
It’s time to move past that single Wi-Fi password scribbled on a whiteboard in the breakroom. Modern authentication methods like IPSK (Identity Pre-Shared Key)—often called EasyPSK—are fundamental to a strong, enforceable policy. Instead of one password for everyone, each user or device gets its own unique key.
This simple shift is a security game-changer. If an employee leaves or a device is compromised, you can revoke its specific access in an instant without disrupting hundreds of other users. It’s a straightforward concept that dramatically improves your security.
Ultimately, that network security policy template is just your starting point. The real value emerges when you adapt it to your unique environment—be it Corporate, Education, or Retail—and integrate it with powerful network management tools like Cisco Meraki. For smaller organizations just getting started, focusing on these fundamentals is crucial. You can dive deeper into this topic by exploring our guide on network security for small businesses. This foundational plan is what keeps your operations running securely and smoothly, day in and day out.
Making Our Template Work for Your Organization
Staring at a blank page to write a network security policy is a tough spot to be in. That’s exactly why we created our downloadable network security policy template—it gives you a solid foundation and a serious head start. This section is all about how to take that template and truly make it your own.
A template is just the starting point. The real value comes when you tailor it to fit the specific needs and quirks of your organization. I'll walk you through how to nail down your acceptable use rules, create a secure guest Wi-Fi experience, and build a clear framework for Bring Your Own Device (BYOD) situations.
Defining Your Acceptable Use Policy (AUP)
Your Acceptable Use Policy (AUP) is really the core of your entire security document. It lays out the rules of the road for how everyone—from the CEO down to a guest in the lobby—interacts with your network. The point isn’t to be overly restrictive; it's to set clear, common-sense expectations that keep your data and your people safe.
Think of your network as a shared resource. The AUP ensures it's used responsibly. This is where you'll list prohibited activities, like downloading illegal files or installing unauthorized software that could open you up to vulnerabilities. For instance, a Retail store’s AUP might explicitly ban connecting personal streaming sticks to the same Wi-Fi network that the point-of-sale systems rely on.
Creating a Secure and User-Friendly Guest Wi-Fi Experience
Guest Wi-Fi isn't a "nice-to-have" anymore; people expect it. But it's also a major potential entry point for threats if you don't manage it properly. Your policy needs to spell out exactly how guest access works, with a heavy emphasis on isolating that traffic from your sensitive, internal network.
This is where a Captive Portal is a game-changer. A Captive Portal acts as a digital front desk for your Wi-Fi. Before anyone can connect to your guest Wi-Fi, they land on a branded page where they have to agree to your terms. It’s a simple step, but it adds a critical layer of accountability.
For a school in the Education sector, this could mean directing students to a filtered network while giving faculty access to a separate, less restricted one. In a Retail setting, you can even use it for marketing opt-ins, turning your free Wi-Fi into a business asset.
Establishing a Clear BYOD Framework
With today's flexible work culture, BYOD is everywhere. Employees appreciate using their own devices, but for an IT team, it can be a security nightmare. A well-defined BYOD section in your network security policy template is essential for balancing that convenience with the control you need in a Corporate environment.
Your policy must be crystal clear about the security requirements for any personal device that touches company data. This typically includes:
- Mandatory Passcodes: Requiring a screen lock on all devices.
- Software Updates: Ensuring operating systems and apps are kept current to patch security holes.
- Secure Onboarding: Using modern Authentication Solutions like EasyPSK to grant and manage access.
A great BYOD policy empowers people; it doesn't restrict them. It offers the freedom employees want while giving the organization the security it absolutely needs. It’s a win-win that supports productivity.
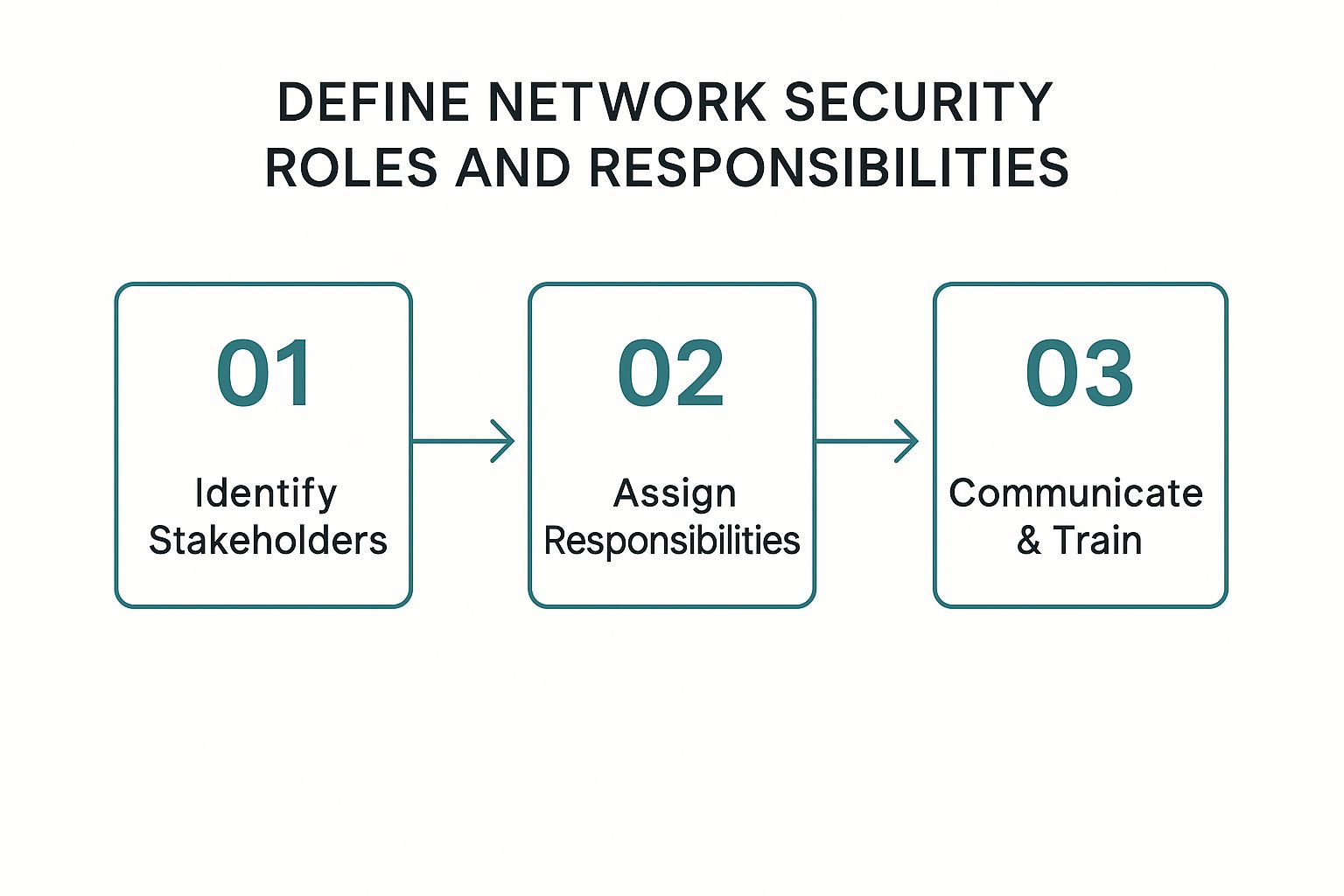
Defining these roles and responsibilities is a foundational part of customizing your policy. This infographic breaks down the simple, three-step process for getting it right.
As you can see, a successful policy isn't just written and filed away. It's owned, communicated, and understood by everyone involved.
Tailoring Authentication for Your Environment
The type of authentication you choose has a massive impact on your overall security. Generic, shared passwords for Wi-Fi are a thing of the past—and for good reason. Modern solutions, especially those available from platforms like Cisco Meraki, give you much more granular control.
For example, using IPSK (Identity Pre-Shared Key), sometimes called EasyPSK, lets you assign a unique password to every single user or device.
Think about it: an employee leaves the company. If you're using a single shared password, you have to update it on every laptop, phone, and tablet in the office. It's a logistical headache. With IPSK, you just revoke that one user's key, and their access is gone instantly, without disrupting anyone else. This is incredibly useful in a fast-moving Corporate BYOD environment or on a large university campus where students and staff change constantly.
By thoughtfully adapting these key areas—AUP, guest access, BYOD, and authentication—you'll turn a generic template into a powerful, living document that actively defends your organization.
Securing Network Access with Modern Authentication
That old, shared Wi-Fi password scribbled on a sticky note? We've all seen it. But it's more than just a messy habit—it's a massive security liability. It’s time for a much smarter approach, one that forms a critical part of any effective network security policy template.
Let's walk through how to move beyond outdated practices and into a world of controlled, secure network access that’s surprisingly user-friendly.
This shift towards structured security isn't just an internal best practice; it's a global movement. A 2024 report from the International Telecommunication Union highlights a major worldwide trend toward formalized cybersecurity frameworks. As of recently, 177 countries had enacted data protection or privacy regulations, and 139 countries had active Computer Incident Response Teams (CIRTs).
This reflects a growing global commitment to integrating structured network security policies at a national level. You can dig into the specifics by checking out the full report on global cybersecurity trends.
The Captive Portal: Your Digital Front Door
Your first line of defense, especially for guest networks, is often a Captive Portal. Think of it as a digital front desk for your Wi-Fi. Before anyone can get online, they are directed to a branded landing page, creating a controlled entry point that accomplishes several key goals at once.
First, it forces users to agree to your Acceptable Use Policy (AUP). That simple click-to-agree step adds a crucial layer of accountability. It's also a fantastic opportunity to showcase your brand, whether you're a Retail store, a school in the Education sector, or a Corporate office.
Most importantly, it segments traffic from the very beginning. Guests are firewalled off from your secure internal network, which is non-negotiable for protecting sensitive data in Retail (Point-of-Sale systems) or Education (student information systems).
Game-Changing Authentication with IPSK and EasyPSK
While Captive Portals are great for guests, you need something more robust for employees, students, or long-term visitors, especially in a Corporate BYOD (Bring Your Own Device) setting. This is where technologies like IPSK (Identity Pre-Shared Key) and EasyPSK truly shine. They are fundamentally different from a standard shared password.
With a traditional password, everyone uses the same key. If an employee leaves or a device is lost, you're looking at a massive disruption—you have to change the password and then update it on every single device in the organization.
IPSK and EasyPSK, available through platforms like Cisco Meraki, solve this problem elegantly. Instead of one key for the whole network, you assign a unique, individual password to each user or even each device.
This is a monumental leap in security and manageability. You gain the power to revoke network access for a single person's devices instantly, without affecting anyone else on the network. It’s the perfect blend of high security and low administrative effort.
How Modern Authentication Works in the Real World
Let's make this practical. Imagine you run a co-working space using a Cisco Meraki network. Here’s how these Authentication Solutions would work in your daily operations:
- Daily Visitors: A short-term visitor arrives. They connect to the guest Wi-Fi, are greeted by your branded Captive Portal, enter their email, agree to the terms, and get online. Their traffic is completely isolated from your main network.
- Monthly Members: A member signs up for a month. Using an EasyPSK solution, you generate a unique key that's valid only for their devices and only for 30 days. When their membership expires, their access automatically terminates. No manual clean-up needed.
- Permanent Staff: Your own staff connect using their unique IPSK credentials. If a team member leaves, you simply log into your dashboard and revoke their key. Their access is gone, and business continues as usual for everyone else.
This level of granular control is essential for a modern network security policy template. It turns access management from a reactive chore into a proactive security strategy. Of course, these access controls are bolstered by strong internal protections. To better understand how networks are segmented and protected from within, you might be interested in our guide on what a stateful firewall is and how it works. By combining these advanced tools, you build a network that is both welcoming and incredibly secure.
Tailoring Your Policy to Your Industry
A generic network security policy is a starting point, not a final product. The reality is that the security needs of a busy Retail store are worlds apart from those of a university campus or a Corporate headquarters. Your job is to take that foundational template and sharpen it into a tool that addresses the specific risks and operational demands of your environment.
Let's walk through what this looks like in practice. I'll share some insights from what I've seen work across different sectors, focusing on how smart Authentication Solutions and network design can solve real-world problems.
Education: Juggling Access for Students, Staff, and Guests
Schools and universities are some of the most complex network environments out there. You have a mix of students, faculty, administrators, and guests all in one place, each with vastly different needs and permissions. The main goal is to build a digital space that's safe for learning but also functional for staff.
Your policy has to draw clear lines in the sand. For example:
- Students: They need solid access to educational websites and online tools, but you also have a duty to shield them from harmful content. This means solid content filtering is non-negotiable, as are bandwidth controls to keep things fair for everyone.
- Faculty & Staff: These users need privileged access to sensitive systems—think grade portals, student records, and administrative software. Their network segment must be secure and highly reliable.
- Guests: Any visitors should land on a completely separate, firewalled network. Giving them simple, internet-only access through a Captive Portal is the standard, and for good reason.
With a platform like Cisco Meraki, this kind of segmentation is pretty straightforward. You can spin up different SSIDs for each group, applying a unique set of rules to each one. To get a much deeper look at the specific challenges in this space, check out our guide on deploying effective and safe Wi-Fi in schools. It’s packed with practical strategies for creating a secure digital learning environment.
Retail: Protecting Payments and Engaging Shoppers
In Retail, it all comes down to two things: protecting financial data and improving the customer experience. Your network is the backbone for everything from your point-of-sale (POS) terminals and inventory systems to the free Wi-Fi you offer shoppers. A breach here isn't just an IT headache; it's a direct hit to your bottom line and the trust you've built with customers.
The golden rule in retail is total network isolation. Your guest Wi-Fi must be completely firewalled from the core network that processes payments and manages inventory. There are absolutely no exceptions.
A Captive Portal is more than just a security layer in Retail—it's a marketing engine. It secures guest access by making users agree to your terms, but it can also collect emails for your newsletter or push a digital coupon right to their screen. Suddenly, a security requirement becomes a tool for growing your business.
Corporate Offices: Taming the BYOD Challenge
The modern workplace is flexible, and that means Bring Your Own Device (BYOD) isn't going anywhere. Employees expect to use their personal laptops and phones for work, but this creates a massive headache for security teams. How do you protect company data on devices you don’t actually own?
This is where your network security policy template needs a well-defined BYOD section, supported by strong Authentication Solutions. The policy must spell out the ground rules for any personal device connecting to the network, including:
- Mandatory screen locks and strong passwords.
- Keeping the device's OS and security software updated.
- Granting the company permission to wipe corporate data if the device is lost or the employee leaves.
The trick is enforcing these rules without making life difficult for your team. This is precisely where solutions like IPSK (Individual Pre-Shared Key) and EasyPSK shine. You can issue a unique Wi-Fi key for each employee's collection of devices. If a device is lost or an employee departs, you just revoke their specific key in seconds, affecting no one else. It makes managing a Corporate BYOD program both secure and surprisingly efficient.
Policy Focus by Industry Sector
To really drive this home, let’s look at how security priorities shift across these three sectors. The core challenge is always security, but what you’re securing and how you do it changes dramatically based on the environment. The table below breaks down these unique focuses.
| Industry Sector | Primary Security Concern | Recommended Solution (e.g., IPSK, Captive Portal) | Key Policy Clause |
|---|---|---|---|
| Education | Differentiating access and protecting minors | Content Filtering, Separate SSIDs, Captive Portal | "User-group access levels (Student, Staff, Guest) will be strictly enforced…" |
| Retail | Protecting payment data (PCI DSS compliance) | Network Segmentation, Guest Wi-Fi with Captive Portal | "The Guest Wi-Fi network will be logically and physically isolated from the POS network." |
| Corporate | Securing company data on employee-owned devices (BYOD) | IPSK / EasyPSK, MDM (Mobile Device Management) | "Personal devices must meet minimum security standards before network access is granted." |
As you can see, the "right" solution isn't universal. It's about matching the right technology and policy language to the specific risks you face every day. This tailored approach is what separates a policy that just sits on a shelf from one that actively protects your organization.
Putting Your New Policy into Action
So, you've put in the hard work and tailored your network security policy template to fit your organization. The rules are defined, the blanks are filled. That’s a fantastic start, but a policy document gathering digital dust in a folder doesn't protect anyone. Now for the crucial part: bringing it to life in a way that your team will actually get on board with.
The trick is to frame this rollout positively. This isn't about bureaucracy or adding red tape. It's about building a safer, more reliable digital space for everyone. The end goal is a smooth transition where good security habits become second nature, not just another top-down mandate.
Laying the Technical Groundwork First
Before you even think about announcing the new policy, you need to get the technical pieces in place. This is where your written rules become real, enforced by your network gear. If you happen to be on a Cisco Meraki network, for instance, this is a refreshingly simple process you can manage right from your dashboard.
You’ll be translating your policy statements into tangible network settings. This usually involves a few key steps:
- Creating separate SSIDs: You'll want distinct Wi-Fi networks for different groups—staff, guests, and maybe even IoT or special-purpose devices. Each gets its own ruleset.
- Setting up access controls: This is where you implement modern Authentication Solutions like IPSK or EasyPSK. Giving every user and device a unique key is a game-changer, especially for Corporate BYOD scenarios.
- Deploying a captive portal: For your guest network, this is the branded sign-in page where users accept your terms before getting online.
Getting this foundation built before the announcement is critical. It ensures that when you tell everyone about the new policy, the system is ready to support it. This prevents a lot of confusion and shows you've thought the whole thing through.
Focus on the "Why," Not Just the "What"
How you talk about these changes will make or break your rollout. Skip the dry, jargon-filled email. Instead, focus on the shared benefits and explain why this is happening. Your team, students, or customers need to understand the reasoning behind the shift.
Frame it as a team effort to protect everyone. For example, explain that moving to EasyPSK means if someone's phone is lost or stolen, you can instantly revoke its access without kicking everyone else off the network—a huge win for security and convenience. If you run a Retail shop, explain how a secure Captive Portal protects customer data while giving them a better, safer browsing experience.
The goal is to build buy-in, not just compliance. When people understand that the policy is there to protect their work, their data, and the organization's stability, they are far more likely to become security allies.
Here’s a sobering thought: very few organizations have truly mastered their security. Recent cybersecurity statistics reveal that a mere 3% of organizations globally have a “mature” level of security readiness—a benchmark a strong policy helps you reach. Considering 76% of businesses in major English-speaking economies were hit by at least one cyberattack recently, being proactive isn't just a good idea; it's essential. You can learn more about the current landscape of cybersecurity threats and readiness from BrightDefense.
Make Training Simple and Accessible
Finally, don't overwhelm people with a 20-page technical manual. No one will read it. Your training materials should be simple and easy to digest. Think quick-start guides, short explainer videos, or even informal lunch-and-learn sessions.
Keep the focus on the practical, day-to-day changes. Show them exactly how to connect their laptop using the new IPSK password or what the new Captive Portal for guests looks like. For instance, clear instructions are everything when implementing a guest network. If you need a good example, our guide on how to set up guest Wi-Fi breaks it down simply. A successful rollout is all about clear communication and making the new process as painless as possible.
Common Questions About Network Security Policies
Even with the best template in hand, putting a network security policy into practice always brings up questions. It's a dense subject, but once you get past the jargon, the core ideas are pretty straightforward. Let's walk through some of the most common questions I hear from clients to help you feel more confident.
My goal here isn't to give you textbook definitions, but real-world answers you can actually use.
How Often Should I Review My Network Security Policy?
Think of your policy as a living document. It's not something you write once, file away, and forget about. The cyber world moves incredibly fast, so a policy that was airtight 12 months ago could easily be full of holes today.
As a rule of thumb, you should plan for a full, deep-dive review at least once a year.
But you also need to be more reactive. Certain events should trigger an immediate policy review. For example:
- You've rolled out a significant new technology, like a major cloud service.
- Your operational model has changed, maybe with a new Corporate BYOD program.
- You've experienced any kind of security incident, no matter how small it seemed.
These regular check-ins are vital. They ensure your defenses, especially those you manage through a powerful dashboard like Cisco Meraki, are always aligned with current reality.
What Is the Real Difference Between IPSK and a Standard Wi-Fi Password?
This is a fantastic question because it gets right to the core of modern Authentication Solutions. A standard Wi-Fi password—what we technically call a Pre-Shared Key (PSK)—is a single password that everyone uses. Think about the chaos when an employee leaves or a phone is stolen. You have to change the password and then communicate it to every single person. It's a huge operational headache, whether you're in Retail or Education.
IPSK (Identity Pre-Shared Key) completely changes the game. Systems like EasyPSK on a Cisco Meraki network let you assign a unique password to each user or device, all for the same Wi-Fi network.
This approach is fundamentally more secure and infinitely easier to manage. You can instantly kill access for one specific user without affecting anyone else. For any modern network, it's a must-have.
This method transforms access management from a blunt instrument into a surgical tool. We dive deeper into this topic in our guide on using security keys for Wi-Fi.
Can a Captive Portal Actually Improve My Network Security?
Absolutely. A Captive Portal is so much more than just a branded login screen. It acts as a hard security boundary, separating untrusted devices on your guest Wi-Fi from your secure internal network.
It also forces users to explicitly agree to your terms and conditions before they get online, which is a big deal for both legal and security accountability. For a Retail shop, it can be used to securely collect marketing opt-ins. In a school or office with a Corporate BYOD policy, it can route different users to different network segments with tailored permissions. It’s your first and best chance to control who gets on your Wi-Fi and what they can do.
At Splash Access, we live and breathe this stuff. Our entire platform is built to make advanced security features easy to use. By integrating directly with Cisco Meraki, we help you deploy robust Captive Portals and manage thousands of unique keys with EasyPSK, making top-tier network security a reality for any organization. Explore how Splash Access can transform your network security today.