Let's face it: a slow, unreliable Wi-Fi connection grinds productivity to a halt. Whether you're running a busy school, a crowded retail store, or a dynamic corporate office, spotty connectivity is more than just an annoyance—it's a direct obstacle to getting work done. If you've ever stared at a spinning wheel of death and wondered why your connection drops at the worst possible moment, the answer is often a single, invisible culprit: Wi-Fi interference.
Why Your Business Wi-Fi Feels So Unreliable
Picture your Wi-Fi signal as a clear conversation happening in a quiet room. Now, imagine a dozen other loud conversations starting up around you. Add a blaring TV in the corner and a running vacuum cleaner for good measure. It would be nearly impossible to hear or be heard, right? That chaos is exactly what Wi-Fi interference does to your network. It’s the digital "noise" that drowns out your signal, leading to frustrating slowdowns and dropped connections.
This digital static comes from a surprising number of places, many of which are unavoidable in a business setting. Every nearby company's network, every employee's Bluetooth headset, and even the microwave heating up lunch in the breakroom are all fighting for the same airwaves. A classic symptom of this battle is when your internet keeps cutting out for no apparent reason. Simply knowing the common culprits is the first step toward a more stable network.
The Challenge in Modern Environments
This problem gets much worse in high-density environments. Think about schools, retail spaces, and corporate offices with "Bring Your Own Device" (BYOD) policies. In these places, hundreds—sometimes thousands—of laptops, tablets, and smartphones are all trying to "talk" over the Wi-Fi at once. This creates an incredibly congested digital space where interference with wifi is practically guaranteed.
This is where having the right hardware, like the systems offered by Cisco Meraki, becomes crucial. Their equipment is specifically engineered to manage these crowded wireless environments effectively. To get a better handle on the type of gear that can fortify your network, take a look at our guide on enterprise WiFi access points.
The image below shows a typical office, highlighting just how many devices and physical objects can get in the way of a clean Wi-Fi signal.
As you can see, even a standard workspace is packed with potential interference sources, from personal gadgets to the very materials the building is made of.
Smart Solutions for a Noisy World
Fighting back against this digital noise requires more than just powerful hardware; it demands a smarter approach to network management. Smart Authentication Solutions are a critical piece of the puzzle. By using a Captive Portal for guests or advanced security like IPSK (also known as EasyPSK), you can control exactly who gets onto your network.
This isn't about being restrictive; it's about being strategic. When you ensure only authorized devices are connected, you cut down on unnecessary traffic and, as a direct result, reduce interference. This proactive combination of managing the airwaves and managing user access is what truly builds a reliable, high-performing wireless experience for everyone.
Identifying the Sources of Network Disruption
Ever wonder why your Wi-Fi suddenly grinds to a halt? Think of it like a conversation at a loud party. When it's just you and a few friends, it's easy to talk. But as more people arrive and start their own conversations, you have to speak louder and repeat yourself just to be heard. That's exactly what interference with wifi does to your network—it's the background noise that drowns out your signal.
To fix the problem, you first have to find the culprits. It's rarely one single thing causing the slowdown. Instead, it’s a mix of different invisible forces degrading your signal. Learning to spot them is the first real step toward a healthier network, especially when you're using a powerful tool like the Cisco Meraki dashboard to get a clear view of your environment.
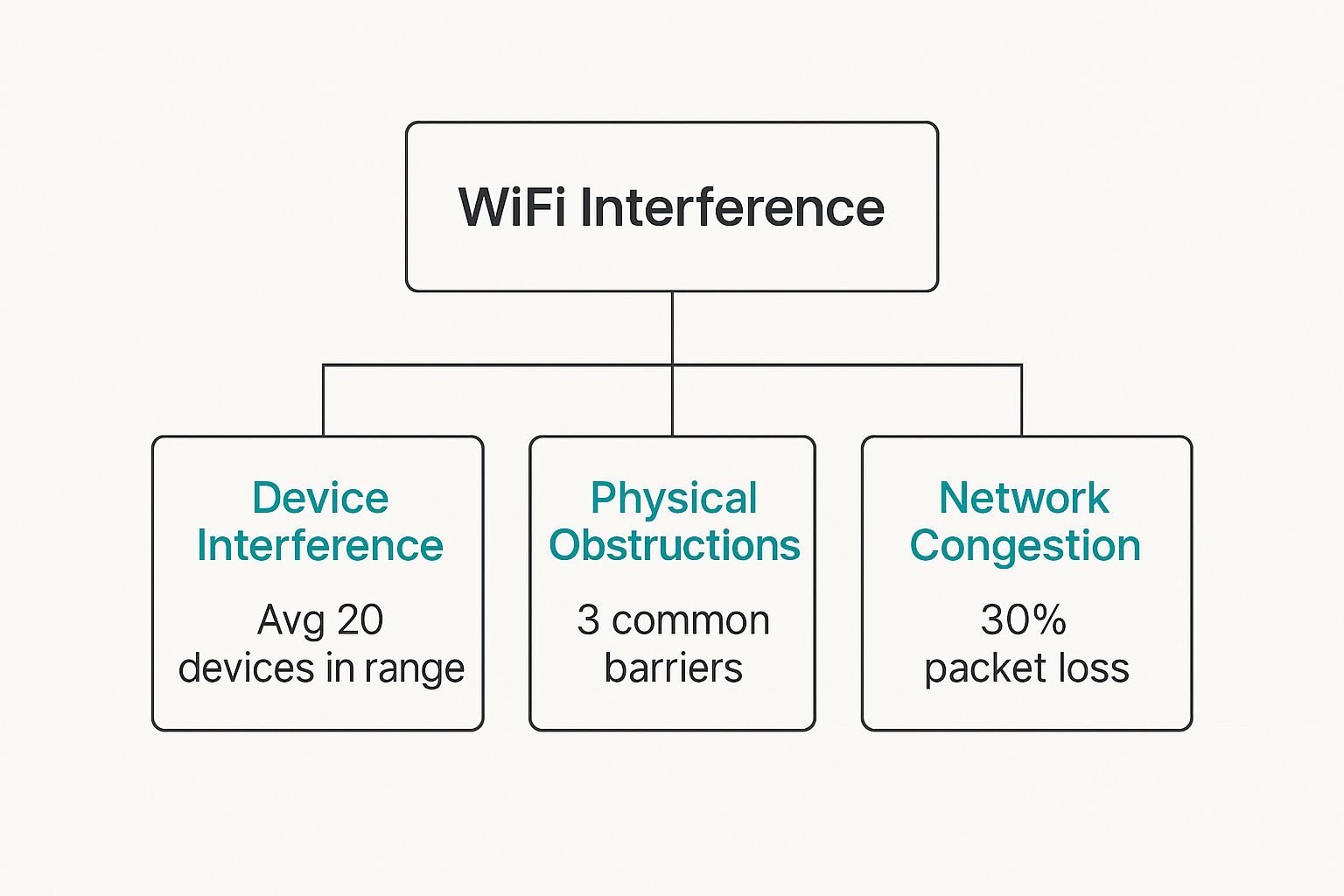
This image breaks down the three big categories of Wi-Fi interference, showing how everything from device clutter to physical walls can chip away at your performance.
As you can see, it’s often a combination of factors that weakens your network, from the sheer number of gadgets to common physical objects getting in the way.
To help you get a head start, here’s a quick look at some of the most common troublemakers. This table separates them into WiFi-based and non-WiFi sources, making it easier to pinpoint what might be causing issues in your own space.
Common Sources of WiFi Interference
| Interference Type | Source Example | How It Affects Your Network |
|---|---|---|
| Co-Channel | Neighboring APs on the same channel (e.g., two APs on Channel 6) | Your AP has to "wait its turn" to transmit, causing delays and lag. It's like a single-lane road where cars have to wait for oncoming traffic. |
| Adjacent-Channel | Nearby APs on overlapping channels (e.g., one on Channel 6, another on 7) | The signals bleed into each other, creating "noise" that corrupts data and forces retransmissions. It's like two radio stations playing slightly off-frequency. |
| Non-WiFi RF | Microwaves, Bluetooth devices, cordless phones, wireless cameras | These devices operate on the 2.4 GHz band and literally shout over your WiFi signal, causing drops and instability whenever they are active. |
| Physical Obstructions | Concrete walls, metal filing cabinets, fish tanks, tinted glass | Radio waves are blocked or absorbed by dense materials, creating dead zones and significantly reducing your network's reach and strength. |
Spotting these sources is half the battle. Once you know what to look for, you can start taking targeted steps to clean up your airwaves and improve your connection.
The Problem of Crowded Airwaves
The most frequent source of interference is simply other Wi-Fi networks. This issue appears in two distinct ways, and knowing the difference is crucial for troubleshooting.
- Co-Channel Interference: Imagine two groups trying to hold separate meetings in the same conference room. They have to constantly pause to let the other group talk. That's what happens when multiple access points (APs) in your building are all using the same channel. Your AP is forced to wait for other APs to finish transmitting before it can send its own data, which creates frustrating lag.
- Adjacent-Channel Interference: Now, picture those same two groups in rooms with paper-thin walls. Their conversations bleed through, making it hard for anyone to focus. This is what happens when nearby networks use channels that are too close, like channels 3 and 4. Their signals overlap and essentially garble each other, leading to corrupted data and slow speeds.
These problems are a nightmare in dense Education and Retail settings, where every classroom or neighboring store has its own network, all competing for the same limited airtime.
When Non-Wi-Fi Devices Get in the Way
It’s not just other Wi-Fi networks you need to worry about. A surprising number of everyday gadgets operate on the same 2.4 GHz frequency as older Wi-Fi, turning your office into a constant battleground for bandwidth.
A crowded frequency is like a one-lane road during rush hour. Devices like Bluetooth headsets, cordless phones, and even the breakroom microwave are all trying to merge into traffic, causing slowdowns for everyone.
This kind of interference is particularly sneaky because it’s often intermittent. Your network might run perfectly one minute, then drop the instant someone makes popcorn. In a modern corporate BYOD (Bring Your Own Device) environment, where everyone has multiple gadgets, this issue gets amplified fast, turning a small annoyance into a major productivity killer.
Managing Access to Reduce Congestion
Finally, great network performance isn't just about signal clarity; it’s about controlling who gets on your network in the first place. A network flooded with unauthorized or unmanaged devices creates its own kind of congestion and interference. This is where smart Authentication Solutions become one of your most effective tools.
For example, using a Captive Portal for guest access or deploying advanced security like IPSK (also known as EasyPSK) helps you manage who connects. By ensuring only approved users and devices can get on, you drastically cut down the number of gadgets competing for airtime. You can get a better sense of these methods by exploring different types of security keys for WiFi. This strategic control is fundamental to building a cleaner, faster, and more reliable network for everyone who depends on it.
How to Detect and Analyze WiFi Interference
Knowing what's causing your Wi-Fi interference is one thing. Actually finding the culprit is a whole different ball game. You need to become a bit of a Wi-Fi detective, shifting from guessing what's wrong to knowing precisely where the problem is. This is a crucial skill for anyone managing a network, especially in busy Education, Retail, or corporate BYOD environments.
The good news? You can leave the magnifying glass and deerstalker hat in the closet. Modern network platforms, particularly from leaders like Cisco Meraki, come with powerful tools that do most of the heavy lifting. These systems turn the invisible world of radio waves into clear, actionable data, giving you a real-time window into your wireless environment.
Using Built-in Platform Tools
Your first, and often best, place to start the investigation is right inside your network management dashboard. Platforms such as the Cisco Meraki dashboard are built to give you a bird's-eye view of what's happening in your airwaves.
One of the most valuable features you'll find is real-time spectrum analysis. This tool is your secret weapon. It scans all the radio frequencies in your space and maps them out visually on a graph. Crucially, it doesn't just show you other Wi-Fi networks; it shows you everything that's making radio noise, including all those non-Wi-Fi offenders.
A spectrum analyzer helps you instantly see what's disrupting your network. It visually separates the good signals (your Wi-Fi) from the bad (interference), so you can pinpoint the source.
With a tool like this, you can immediately spot that the breakroom microwave is blasting the 2.4 GHz band every day at lunchtime. Or you might discover that a new wireless security camera was installed right on top of your most important Wi-Fi channel.
Another essential tool is the channel utilization graph. This chart shows you exactly how "busy" each Wi-Fi channel is. If you notice certain channels are constantly hovering near 100% utilization, that's a dead giveaway for co-channel interference. Your access points are essentially stuck waiting in a long line to talk, which grinds performance to a halt for everyone connected.
Think of it like a developer meticulously debugging code to find a single error. A network admin uses these diagnostic tools in the same way—to methodically pinpoint and resolve the exact sources of interference.
The Good Old-Fashioned Walk-Through
As great as software tools are, you should never underestimate the power of a simple physical walk-through. Sometimes the source of your interference with WiFi is hiding in plain sight.
Take a stroll around your facility, keeping an eye out for the usual suspects. Pay extra attention to the areas where people complain about the Wi-Fi the most.
- Breakrooms & Kitchens: Microwaves are notorious for killing the 2.4 GHz band.
- Office Spaces: Look for cordless phone bases, Bluetooth speakers, or even poorly shielded computer monitors.
- Near Windows: Peek outside. A neighboring business might have powerful access points bleeding right through your walls.
This hands-on approach is especially important in places like Retail and Education, where new gadgets are constantly being plugged in without anyone telling the IT department. That slick new digital sign or interactive display could be the very thing causing all your connection headaches.
The Role of Authentication in Detection
This might sound a little strange, but your user authentication method can actually be a diagnostic tool. If your network has weak or nonexistent access control, it can quickly become a free-for-all. When that happens, it's nearly impossible to tell if you're dealing with genuine RF interference or just massive congestion from a flood of unauthorized devices.
By implementing smart Authentication Solutions, you create a controlled and known environment. Once you have a clear list of who and what is on your network, troubleshooting becomes far easier. This is where methods like IPSK (also known as EasyPSK) or Captive Portals show their value beyond just security. If performance is still sluggish after locking down the network, you can confidently rule out device overload and focus your investigation on RF interference.
Having strong network controls is fundamental to building a manageable and reliable system. You can explore how to implement these through effective wireless access control systems.
Actionable Strategies to Mitigate Interference
Pinpointing the problem is half the battle. Now comes the part that actually makes your network reliable: fixing the interference with wifi. Since you know what to look for, let's walk through some practical ways to get clearer, more stable connections. These aren't just minor technical tweaks; they're foundational changes that can turn a frustrating network into a dependable asset.
Often, the best place to start is by getting back to basics with smart channel planning and thoughtful access point (AP) placement. Think of Wi-Fi channels as lanes on a highway. If too many networks try to cram into the same lane, you get a traffic jam. By manually setting your APs to non-overlapping channels—like 1, 6, and 11 on the 2.4 GHz band—you give each one its own clear path, which dramatically cuts down on co-channel interference.
Where you put your APs is just as important. Sticking an AP behind a thick concrete wall or inside a metal filing cabinet is like trying to shout instructions from another room. The signal gets muffled and weak. A proper site survey and layout ensure your APs have a clean line of sight to the devices they serve, a must-have for physically complex buildings like schools or large retail stores.
Let Your Network Manage Itself
While manual tuning is a solid start, today's networks—especially in dynamic BYOD Corporate environments—need something smarter. This is where modern systems like Cisco Meraki really come into their own. Their platforms feature a powerful tool called Radio Resource Management (RRM), which essentially acts as an automated air traffic controller for your Wi-Fi.
RRM continuously scans your wireless environment for interference and congestion. It then automatically adjusts channel assignments and AP power levels in real-time to sidestep noise, making sure your network is always operating on the cleanest, most efficient path available.
This kind of automation saves countless hours of hands-on work and adapts on the fly to new challenges, like when a neighboring business powers up a new, high-strength network. It’s a set-it-and-forget-it feature that keeps your Wi-Fi humming along smoothly.
Guiding Traffic to the Fast Lane
Another incredibly effective technique is band steering. Many modern devices are dual-band, meaning they can connect to both the crowded 2.4 GHz band and the wider, faster 5 GHz band. Band steering simply "nudges" those capable devices over to the 5 GHz band, freeing up the 2.4 GHz highway for older legacy devices that have no other choice.
This is a game-changer in high-density sectors like Education and Retail, where hundreds of smartphones, tablets, and laptops are all fighting for airtime. By shifting as much traffic as possible to the 5 GHz superhighway, you instantly improve speed and capacity for everyone.
Of course, technical solutions are only part of the story. Physical sources of interference can be just as disruptive. To combat signal degradation at its source, you might need to look at infrastructure improvements, like implementing robust EMI shielding solutions for heavy machinery or critical power systems to reduce ambient electromagnetic noise.
Finally, never underestimate the power of intelligent user management. Using smart Authentication Solutions, such as a Captive Portal for guest access, is a brilliant way to control who is on your network and what they can do. When you have visibility and control, you can manage bandwidth more effectively and stop rogue devices from causing chaos. Our guide on how to set up guest wifi is a great resource for getting this up and running.
Using Smart Authentication to Stabilize Your Network
A stable network isn't just about clear airwaves. We've talked a lot about physical sources of interference with WiFi, but a massive drain on performance often comes from something much closer to home: your own users. A network flooded with unauthorized or unmanaged devices creates its own brand of digital chaos and congestion.
This is where modern Authentication Solutions come in. They're not just a security measure anymore; they're a powerful performance-tuning tool. By intelligently controlling who gets onto your network, you can slash unnecessary traffic, clean up your airwaves, and save that precious bandwidth for the people and applications that truly need it. It’s less about locking people out and more about creating a clean, orderly environment for everyone.
For any business that serves the public, like in Retail or hospitality, the Captive Portal is the perfect front door for your network. It's that familiar login page you see at a coffee shop or hotel—and it's one of the most effective ways to manage guest access without giving your users or your IT team a headache.
The scene below captures why this matters: a team collaborating, relying on a network that works smoothly for every single authorized user.
That kind of productivity is only possible when the network underneath can handle the demands of multiple people and their devices without faltering.
Managing Guest Access with Captive Portals
Think of a Captive Portal as a friendly gatekeeper. Instead of letting every device within range automatically hop onto your network and suck up bandwidth, it asks users to check in first. That simple step gives you immense control.
With a well-designed Captive Portal, you can:
- Prevent Bandwidth Hogs: Stop random users from connecting to stream videos or download huge files, which directly impacts performance for paying customers and staff.
- Set Usage Limits: You can apply time or data restrictions to guest users, ensuring your critical business operations always have the priority they need.
- Enhance Security: By requiring authentication, you create a crucial barrier against potentially malicious devices joining your network and causing trouble.
Platforms like Cisco Meraki, when combined with advanced portal solutions, make this process feel effortless. For a retail store, this means your point-of-sale systems will never lag during a rush. For a hotel, it guarantees every guest gets a fair and consistent slice of the internet.
Securing BYOD with IPSK and EasyPSK
While Captive Portals are great for guests, they aren't the right tool for your trusted internal users, especially in Education or BYOD Corporate settings. Asking employees or students to log in through a portal every day is just a nuisance. This is where a more robust, user-friendly solution called Identity Pre-Shared Key (IPSK)—often called EasyPSK—really shines.
IPSK is the perfect middle ground between a simple, insecure shared password and a complex, enterprise-grade security system. It lets you give a unique password to every single user or device, giving you fine-grained control without the usual IT overhead.
Picture a large school campus. Giving every student and faculty member the same Wi-Fi password is a security nightmare waiting to happen. If one person shares it, your entire network is wide open. With IPSK, each person gets their own key.
- If a student's laptop gets a virus, you can revoke its access instantly without affecting anyone else.
- When a staff member leaves the company, their key is simply deactivated.
- You gain a crystal-clear view of exactly which devices belong to which user, making troubleshooting worlds easier.
This method directly combats interference with WiFi by preventing a flood of unidentifiable devices from cluttering your network. By making sure only authorized, known devices are connected, you reduce the overall load and create a more stable, predictable, and secure wireless experience. For any organization struggling with a chaotic BYOD policy, EasyPSK is a game-changer.
Building a Resilient Wi-Fi Network for the Future
We’ve journeyed through the noisy, invisible world of Wi-Fi, and now it’s time to put all the pieces together. Building a truly resilient network isn’t about fixing one isolated problem. It’s about taking a holistic view that combines smart hardware, intelligent software, and sensible access policies to deliver a connection that’s fast, reliable, and secure for everyone.
The first step in fighting interference with WiFi is getting the right tools for the job. Platforms like Cisco Meraki are built for modern network management, giving you the power to see what’s really happening on your airwaves. Instead of guessing, you can pinpoint the exact sources of interference—from a neighboring business's network to that notorious breakroom microwave.
Combining Smart Tech with Secure Access
But clear airwaves are only half the battle. Even the most perfectly tuned network can get bogged down by too many devices trying to connect at once. This is a huge issue in high-density places like Education campuses, busy Retail stores, or corporate offices that have liberal BYOD policies. This is where modern Authentication Solutions become your secret weapon against network congestion.
A resilient Wi-Fi network isn’t just strong; it’s also smart. It knows who should be on the network and what they need, ensuring critical operations always have priority while providing a great experience for everyone else.
Implementing a Captive Portal creates a controlled front door for guests. It’s a simple step that stops the free-for-all of unknown devices gobbling up your bandwidth—a surprisingly common problem. For your internal team, especially in a BYOD Corporate environment, a more permanent solution like IPSK (also known as EasyPSK) offers a secure and simple way to onboard devices without headaches. It ensures only authorized users can get on, which dramatically cuts down on unnecessary traffic.
Your Roadmap to a Better Network
Creating this kind of robust ecosystem is a direct investment in productivity and user happiness. While tackling interference is critical, the bedrock of a great network often starts with choosing the best business internet providers to guarantee you have a solid foundation from the start.
Here’s your complete roadmap to success:
- Identify Interference: Use tools from partners like Cisco Meraki to get a clear picture of what's happening in your airspace.
- Mitigate Noise: Put strategies like channel planning and band steering into practice to carve out cleaner communication paths.
- Control Access: Deploy smart Authentication Solutions like Captive Portals and IPSK/EasyPSK to manage the load on your network and tighten up security.
This three-pronged approach is the key to building a network that just works, plain and simple. For businesses in the hospitality sector, these principles are absolutely essential for keeping guests happy. You can learn more about crafting first-class connections in our guide to https://splashaccess.com/hotel-wifi-solutions/.
By bringing these elements together, you’ll build a Wi-Fi experience that not only meets the demands of today but is also ready for whatever tomorrow throws at it.
Frequently Asked Questions
Still have some questions about dealing with Wi-Fi interference? You're in good company. Let's walk through some of the most common questions IT managers ask when they're trying to build a more resilient network.
What’s the Fastest Way to Pinpoint WiFi Interference?
Hands down, the quickest and most accurate method is using a spectrum analyzer. You don't necessarily need a separate, clunky device for this anymore. Modern network platforms like Cisco Meraki build this functionality right into their management dashboards.
A spectrum analyzer gives you a live, visual map of all the radio frequencies operating in your space. This means you can see everything—not just other Wi-Fi networks, but also disruptive non-Wi-Fi signals from things like microwaves or wireless cameras. It takes the guesswork out of troubleshooting, letting you instantly see what's causing the problem.
How Does a Captive Portal Actually Improve Network Performance?
A Captive Portal is more than just a welcome screen; it's a powerful tool for managing network performance. Think of it as a bouncer for your Wi-Fi. It stops every unauthorized device from just hopping onto your network and draining your bandwidth. This is mission-critical in places like Retail, where a laggy point-of-sale system is simply not an option.
By forcing guest users to log in, you gain control. You can see who is connecting, limit the number of devices, and even set bandwidth caps. This ensures your essential business systems always have the speed they need, cutting down on the network congestion that acts as a major form of interference with wifi.
Is IPSK a Good Fit for a School's BYOD Policy?
Yes, it’s a fantastic solution. IPSK (Identity Pre-Shared Key), often called EasyPSK, is tailor-made for the challenges of an Education environment. It perfectly blends strong security with the simplicity needed for a Bring Your Own Device (BYOD) program.
Instead of a single, shared password that inevitably gets passed around, each student, staff member, or device gets its own unique key.
- Granular Control: If a student's laptop is causing issues or they leave the school, you can revoke its key instantly.
- Zero Disruption: Revoking one key doesn't affect anyone else on the network.
- Enhanced Security: It dramatically boosts security and network stability by ensuring only approved users and devices can connect.
Can You Really Have Too Many WiFi Access Points?
Absolutely. It's a classic case of "more is not always better." While it might seem like adding more access points (APs) would improve coverage, packing too many into one area is a surefire way to create Wi-Fi interference.
When APs are too close together, they start competing for the same radio channels. This leads to what we call co-channel and adjacent-channel interference, where your own network hardware ends up fighting itself for airtime, slowing everything down. The real goal isn't just more APs, but smarter placement based on a professional site survey.
Ready to stop wrestling with interference and start managing your network with intelligence? Splash Access works directly with Cisco Meraki to deliver powerful authentication like Captive Portals and IPSK. Take back control of your network at https://www.splashaccess.com.