Hey there! We’ve all seen it: that dreaded "connection is limited" or "No Internet" message. It’s a frustratingly common problem, right? What it's really telling you is that your device has successfully shaken hands with the Wi-Fi router, but for some reason, it just can't get out onto the wider internet.
Think of it like being let into the lobby of a building but denied access to the main floors. You're in, but you can't go anywhere. Let's dig into why this happens and what you can do about it in a friendly, no-jargon way.
What Does a Limited WiFi Connection Actually Mean?
When that little yellow warning triangle pops up, your first instinct is probably to blame your laptop or maybe restart the router. At home, that often works. But in a busy office, a school campus, or a crowded retail store, the root cause is usually more complex.
This error signals a breakdown somewhere between your device and the global internet. Sometimes, it’s just plain old network congestion—too many people trying to get online at once. More often than not, especially in environments with BYOD (Bring Your Own Device) policies, it points to an authentication failure. These networks, common in education, retail, and corporate settings, are built to securely manage hundreds, if not thousands, of simultaneous connections.
The Critical Role of Network Authentication
In most public or business environments, you don't just connect to the Wi-Fi. You have to be granted access first. This is where robust networking hardware from industry leaders like Cisco and Cisco Meraki is essential. They're designed for high-density places where a single shared password would be a massive security risk and a management nightmare.
The real bottleneck is often the authentication step itself. This can take a few different forms:
- Captive Portals: These are the login pages you encounter at hotels, airports, and coffee shops. If that page doesn't load correctly, your device is left in limbo—connected to the local network but completely walled off from the internet.
- Authentication Solutions: Advanced networks use security protocols like IPSK (Identity Pre-Shared Key) or specialized solutions like EasyPSK. These systems give each user or device a unique key, which dramatically boosts security and control.
If an authentication server is offline or your device isn't properly registered, you’ll get hit with that limited connection error. Understanding these systems is the first step to a solution. For a deeper dive, you can check out our guide on what a captive portal is and how it works.
Here’s a pro tip from the field: If a single person in an office reports a "limited connection," it might just be a glitch with their device. But if a handful of people suddenly report the same issue? That’s almost always a network-level problem, likely tied to authentication or server capacity.
With global internet access now reaching roughly 5.56 billion people—nearly 68% of the world's population, according to data from Statista—the demand for stable connectivity is exploding. This puts incredible strain on wireless infrastructure, making "limited WiFi" a frequent complaint fueled by overloaded networks and authentication hurdles in busy areas.
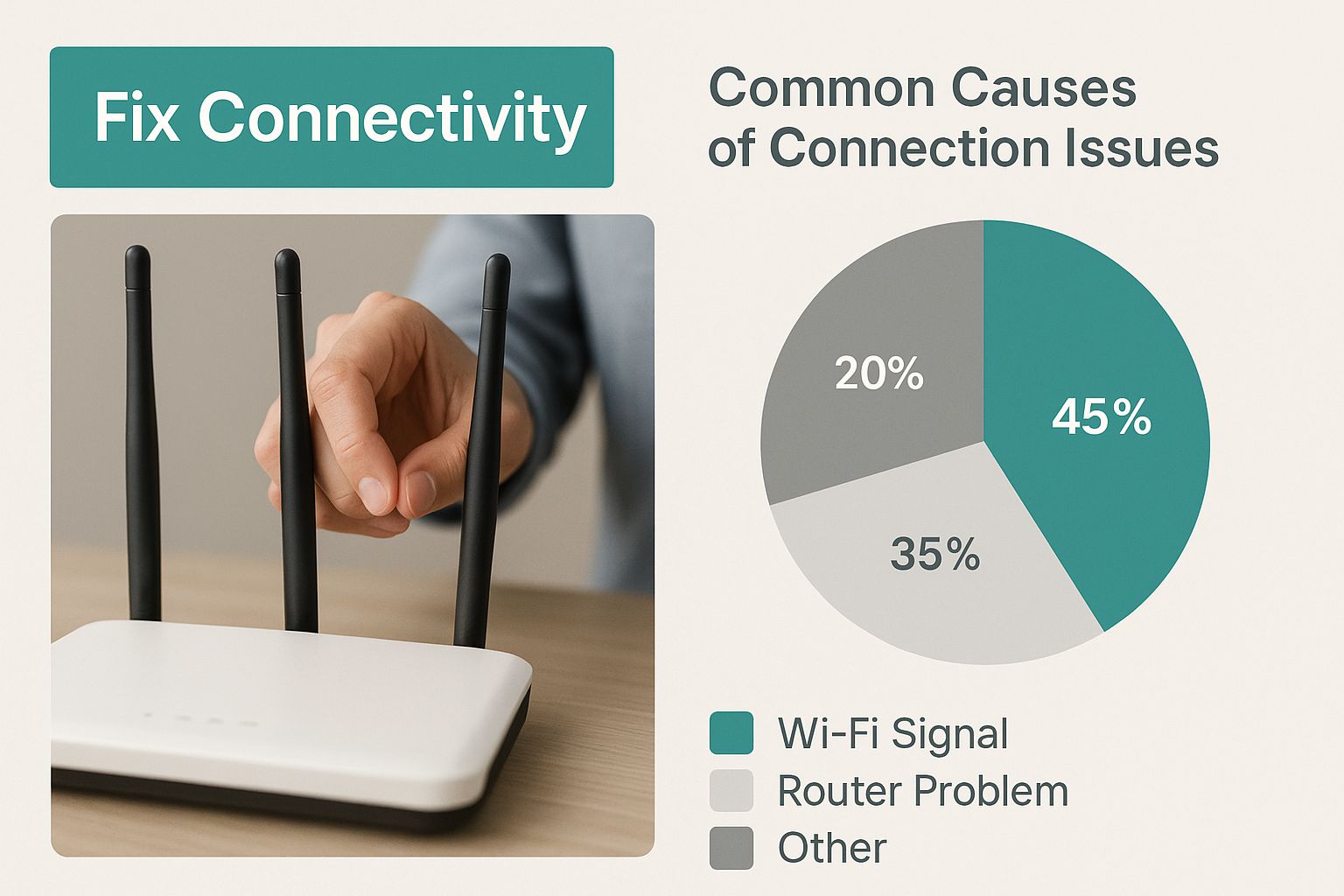
Before we jump into the fixes, let’s quickly identify the most common culprits.
Common Causes of Limited WiFi Connection
This table gives a quick glance at the most frequent reasons for limited connectivity and where you're most likely to encounter them.
| Problem Area | Common Symptom | Typical Environment |
|---|---|---|
| Authentication Failure | Can't get to the login page; password rejected. | Corporate offices, schools, hotels, public hotspots |
| IP Address Conflict | Device shows "self-assigned IP"; connects/disconnects. | Any network, but common in large BYOD settings |
| Network Congestion | Extremely slow speeds; connection drops randomly. | Coffee shops, airports, stadiums, large events |
| Outdated Drivers | Only one specific device can't connect properly. | Home or office, specific to a user's device |
| Router/AP Malfunction | No devices can get internet, but Wi-Fi signal is strong. | Home, small offices, or specific zones in a large building |
Recognizing these patterns is half the battle. Now that you have a better idea of what might be going wrong, we can move on to the practical steps for getting you back online.
Sometimes, that frustrating "connection is limited" error has nothing to do with your Wi-Fi signal strength. The real problem often lies in the authentication process—the digital handshake your device needs to perform to get approved for internet access. I see this all the time in busy environments like retail stores, education campuses, and offices with BYOD policies.
Many of these places use a Captive Portal. You know the one—it's that login page that pops up at a hotel or coffee shop. Its job is to "capture" you and make you accept terms or log in before you can get online.
When the Handshake Fails
The issue crops up when that Captive Portal page never loads. Your device is technically connected to the router, but it's stuck in a digital waiting room, completely cut off from the wider internet. This is a classic cause of the "limited connection" message and a huge source of frustration for users and support tickets for IT admins.
For networks built on platforms like Cisco Meraki, managing this access is a top priority for security and performance. Just handing out a single, shared password to everyone is asking for trouble. The moment that password gets out, your network's security is gone. That’s why smarter authentication solutions are quickly becoming the new normal.
A single shared password is like giving every employee the same key to the front door. If one key is lost or copied, the entire building is at risk. Modern authentication gives everyone their own unique key.
The Rise of Smarter Authentication
This is where more modern, secure methods enter the picture, providing a much safer and smoother experience than a single, easily compromised password.
- Identity Pre-Shared Key (IPSK): Instead of one password for the whole network, IPSK gives each user or device its own unique key. From a security and management perspective, this is a total game-changer.
- EasyPSK: This is really just a user-friendly name for systems that make managing all those unique keys simple, putting powerful security within reach for organizations of any size.
Think about it. With an IPSK system, if an employee leaves or a student in a BYOD environment loses their phone, an admin can instantly disable that one specific key. Nobody else is affected. You avoid the nightmare of changing the main Wi-Fi password and reconfiguring hundreds of devices. This is a core reason it’s so popular in Cisco Meraki setups.
If you're curious about the nitty-gritty, learning how IPSK works with RADIUS authentication offers a much deeper look into how these secure networks are built.
Moving to individual credentials makes troubleshooting so much easier. When a user can't connect, IT can check their specific key's status instead of chasing a ghost affecting the entire network. It’s a far more precise, secure, and ultimately better way to handle wireless access for everyone.
Managing Wi-Fi in High-Density Environments
Ever been in a packed lecture hall, a busy retail store on a weekend, or a corporate all-hands meeting and suddenly lost your Wi-Fi? You're not alone. This is a classic case where a standard Wi-Fi network, perfectly fine for a handful of users at home, simply buckles under pressure. When dozens of people get that "connection is limited" error at the same time, it’s a sure sign the network is overwhelmed.
Think of it this way: when too many devices try to connect to a single access point (AP), it's like a room where everyone is shouting at once. Nobody can be heard clearly. This is precisely the problem that enterprise-grade solutions from providers like Cisco Meraki are built to solve. They’re engineered from the ground up for the unique challenges of BYOD Corporate environments and bustling Education campuses.
Smart Strategies for Crowded Networks
To prevent this digital traffic jam, a well-designed network uses a few key tactics to keep everyone online and happy. These aren't just fancy add-ons; they are absolutely essential for delivering a smooth user experience in a crowded space.
Here are three of the most effective strategies I’ve seen in action:
- Band Steering: This is a clever feature that automatically pushes devices capable of using the 5GHz frequency off the overcrowded 2.4GHz band. It’s like a smart traffic controller opening up a brand-new, empty highway lane for faster-moving cars.
- Load Balancing: Instead of letting one access point get buried under connection requests, the network intelligently spreads the load across multiple nearby APs. This prevents any single piece of hardware from becoming a bottleneck.
- Smart AP Placement: This is more art than science sometimes. A professional network design involves strategically placing access points to ensure wall-to-wall coverage while minimizing interference between them. The goal is to eliminate those frustrating dead zones where connections just drop.
These features work in concert to create a network that can handle almost anything you throw at it. It's no surprise that hotels are now heavily investing in this kind of infrastructure, recognizing robust Wi-Fi as a crucial hotel amenity for managing guest density and satisfaction.
The core idea is simple: don't let devices fight for airtime. Actively manage the connections to create a balanced, efficient, and reliable wireless environment for everyone involved.
Planning for Peak Demand
When designing a network for a school, office, or store, you can't plan for average use. You have to design for peak demand. With mobile data usage projected to reach 200 exabytes globally per month by 2025, the strain on Wi-Fi is only getting worse. This incredible demand, especially in dense urban areas, is a primary cause of the "limited Wi-Fi connection" error when a network just can't keep pace.
Ultimately, successfully managing these environments comes down to combining the right hardware, like Cisco access points, with intelligent software. This includes robust authentication solutions like IPSK and Captive Portals that can handle a high volume of users securely. If you’re tasked with setting up public Wi-Fi, our guide on how to set up guest WiFi is a fantastic resource for creating a reliable and user-friendly experience from the start.
A Practical Playbook for BYOD in Business and Education
Bring Your Own Device (BYOD) policies are everywhere now, from corporate offices to school campuses. While giving people the freedom to use their own gear is great for flexibility, it can quickly turn into a massive headache for IT teams. When a user's personal laptop or phone flashes that dreaded "connection is limited" error, finding the root cause among a sea of different devices is a real challenge. That's why having a smart playbook is so crucial for taming the BYOD chaos.
In these mixed-device environments, the problem often boils down to authentication. A personal device might not be playing nice with the network’s security protocols, leaving it stuck in a sort of digital limbo—connected to the Wi-Fi, but with no actual internet access. This is a daily reality in the Education, Retail, and BYOD Corporate sectors.
Getting a handle on these connectivity issues often requires a more hands-on approach than just telling someone to restart their router.
As the image suggests, fixing these limited connections means actively managing your network, not just hoping for the best.
The Power of Granular Control
The old-school method of using one Wi-Fi password for everyone just doesn't cut it anymore. It's not secure, and it definitely doesn't scale. If that one password gets out—and it always does—your entire network is wide open. This is where modern Authentication Solutions come in, especially those built into powerful platforms like Cisco Meraki.
This is where Identity Pre-Shared Key (IPSK) and simpler systems like EasyPSK change the game. They are tailor-made for BYOD environments. Instead of one password for the entire organization, each user and device gets its own unique key.
Picture this: An employee leaves the company, or a student loses their phone. With IPSK, you just log in and revoke the key for that one specific device. Everyone else stays connected without a hitch. You avoid the chaos of changing the Wi-Fi password for hundreds of people and the flood of support tickets that follows.
This device-level control strikes the perfect balance. Users get the convenience of BYOD, and you get the airtight security and control you need.
Traditional WiFi vs. IPSK for BYOD Environments
When you put the old shared password method next to a modern IPSK approach, the benefits become crystal clear, especially for a busy company or school. It’s a night-and-day difference in security and manageability.
| Feature | Traditional Shared Password | IPSK / EasyPSK Solution |
|---|---|---|
| Security | Low. A single compromised password exposes the entire network. | High. Each device has a unique key, isolating any potential breaches. |
| Onboarding | Simple but insecure. Anyone with the password can connect. | Secure. Devices are onboarded with unique credentials, often automated. |
| Revoking Access | Difficult. Requires changing the password for all users and devices. | Simple. A single click revokes access for one specific device or user. |
| Troubleshooting | Challenging. Difficult to trace issues to a specific user or device. | Easy. Admins can see the status of each individual key and connection. |
Ultimately, moving to an IPSK model, perhaps through a platform like Cisco Meraki, helps you get ahead of the "connection is limited" errors before they even start. You shift from putting out fires to proactively managing a stable and secure network for every single person, on every single device.
Fine-Tuning Your Network's Foundation for Rock-Solid Reliability
Let’s get down to brass tacks. A fantastic Wi-Fi experience relies on a solid network foundation. Oftentimes, that frustrating "limited Wi-Fi connection" message has nothing to do with your internet provider at all. The real bottleneck is frequently your own internal network hardware.
You can have the fastest fiber optic plan available, but if your network is chugging along on outdated switches, gateways, or access points, it’s like trying to pour a gallon of water through a tiny funnel. The performance simply won't be there, and this becomes painfully obvious in demanding environments like BYOD Corporate networks or busy Education campuses.
Creating a Unified Network Ecosystem
This is precisely why investing in a modern, cohesive infrastructure from industry leaders like Cisco and Cisco Meraki makes such a difference. Their equipment is engineered to work together flawlessly. Just imagine your access points, switches, and security gateways all communicating with each other and being managed from a single, intuitive cloud dashboard.
This unified approach gives you some huge advantages:
- Effortless Monitoring: You get a complete, at-a-glance view of your entire network’s health, which makes spotting potential issues a breeze before they ever impact your users.
- Proactive Troubleshooting: The system can often flag a struggling switch or an overloaded access point on its own, letting you step in and fix it before the "my Wi-Fi is down" calls begin.
- Seamless Upgrades: Firmware updates are automatically deployed from the cloud. This means your hardware is always secure and equipped with the latest features without you having to lift a finger.
For more hands-on strategies to boost your network's performance, these expert tips for eliminating connectivity issues are a great resource.
The quality of your internal hardware has a direct and profound impact on your Wi-Fi reliability. Outdated gear is one of the most common—and most overlooked—causes of chronic connection problems.
Why Authentication and Infrastructure Are Two Sides of the Same Coin
Your network’s physical backbone is only half the battle. Robust authentication solutions are the other critical piece of the puzzle. You can have the best hardware money can buy, but a shaky or poorly configured authentication system can grind everything to a halt.
This is where solutions like IPSK or EasyPSK become so valuable. They ensure that once a device gets onto your high-performance network, it stays connected securely and stably. To get a better handle on these security layers, take a look at our guide comparing WPA2 Personal vs. Enterprise security.
The problem of infrastructure quality isn't just local; it's a global challenge. Even as countries like China and India have brought over a billion new users online, many still grapple with limited Wi-Fi due to aging hardware and congested public hotspots. High internet adoption doesn't automatically mean a great experience. Investing in your network backbone is truly the most effective long-term strategy for stamping out connectivity complaints for good.
Frequently Asked Questions About Limited WiFi
Still wrestling with that frustrating "limited connection" error? I get it. Let's walk through some of the most common questions I hear from users and IT pros who are trying to pin down these tricky WiFi problems.
Why Does My WiFi Work for Some Devices But Not Others?
This is a classic head-scratcher. When one device connects fine but another won’t, it almost always points to an authentication issue. This is especially true in BYOD Corporate or Education environments where everyone brings their own gear.
Often, one device is simply failing its login attempt on a Captive Portal, while another gets right through. It can also be a simple compatibility problem. For instance, an older laptop might not support the modern security protocol or the specific WiFi band the network is using.
If you're on a managed network like Cisco Meraki, this could be intentional. An administrator might have set up rules that only allow registered devices to connect, which is often managed with a secure IPSK system.
What Is a Captive Portal and Why Does It Sometimes Fail to Load?
You know that login page you see at hotels, airports, and coffee shops before you can get online? That’s a Captive Portal. It essentially "captures" your browser and forces you to log in or accept the terms of service.
If it fails to load, it’s usually because your browser's security settings are blocking the automatic redirect needed to display the page. A quick fix is to clear your browser cache. Another trick that often works is telling your device to "forget" the network and then rejoining it. This can give it the nudge it needs to find and load the portal correctly.
For network admins, a failing captive portal is a major red flag. It often means a misconfiguration in the network settings is preventing devices from getting the right instructions to find the login page.
How Can an IPSK Solution Help My Retail Business?
In a retail setting, you're juggling two distinct groups: staff devices and customer WiFi. Using a single password for everything—from staff point-of-sale systems to inventory scanners—is a massive security risk.
This is where IPSK and EasyPSK solutions shine. They allow you to assign a unique, permanent key to each business-critical device. If a scanner gets lost or an employee's tablet is stolen, you just revoke its specific key without disrupting any other operations. It’s a game-changer.
You can still offer guest WiFi through a standard Captive Portal. But IPSK also lets you give unique, temporary keys to special partners or VIP customers for a more premium, secure connection. This kind of network segmentation is a huge upgrade for both security and reliability. Getting familiar with security keys for WiFi can help you understand these more advanced authentication methods.
Is a Limited Connection My Device's Fault or the Network's?
It could be either, but in a business, school, or retail store, the problem is most often on the network's side.
While restarting your device is always a good first step, if several people are hitting the same wall, it's almost certainly a network problem. The culprit could be anything from simple network congestion to an issue with the authentication solutions server.
Enterprise systems from providers like Cisco and Meraki give administrators a central dashboard to see if the problem is widespread, which helps them pinpoint the source much faster than guesswork ever could.
Splash Access provides instantly deployable captive portals and advanced authentication solutions for Cisco Meraki, helping you eliminate connectivity issues for good. Learn more and enhance your guest Wi-Fi experience at https://www.splashaccess.com.