A new and potent variant of ransomware is making headlines in a cyber attack that shares many similarities with last month’s record-breaking WannaCry outbreak. Hackers targeted out-of-date systems in Ukraine, but the threat quickly spread to Europe and North America, impacting several major global organizations. Although both variants share a lot of the same characteristics, several key differences to the anatomy of Nyetya1 suggest hackers are not making some of the same mistakes that led to WannaCry’s rapid demise.
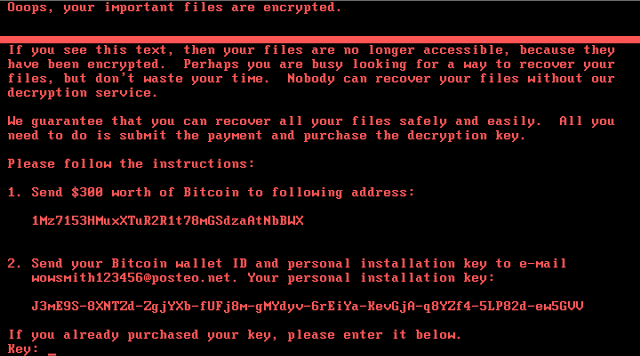
Example of a system infected with Nyetya ransomware
Talos, Cisco’s industry-leading threat intelligence team, quickly got to work and produced a preliminary evaluation of the threat, confirming that Meraki MX customers are fully protected by Advanced Security features including Advanced Malware Protection (AMP) and IDS/IPS. Newly released support for AMP Threat Grid also helps identify malicious binaries and build protection into all Cisco Security products.
Since Nyetya uses the same EternalBlue exploit used by WannaCry to spread, it is imperative that inbound firewall rules protect against remote SMBv1 execution (Meraki’s security appliance firewall will defend against all inbound connection requests by default). It is also highly recommended that all Windows-based systems are fully updated to defend against further spreading of the threat.
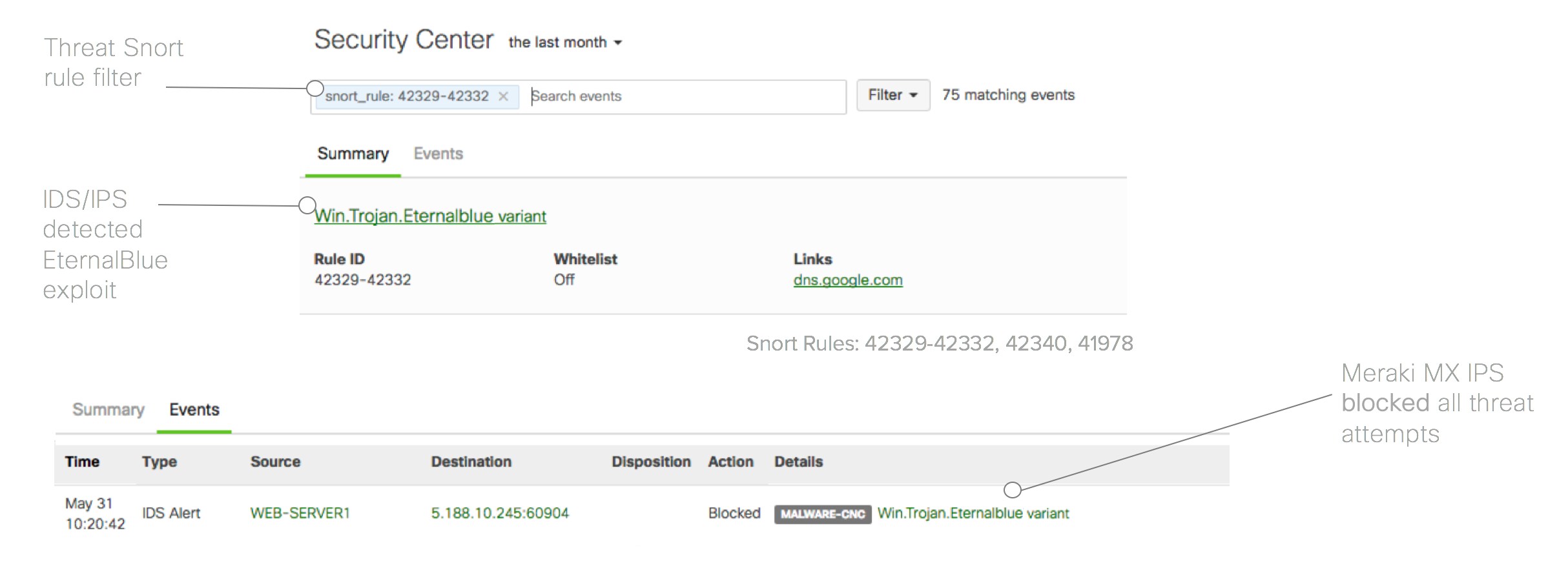
Example of Meraki MX with Intrusion Prevention blocking Nyetya Eternal Blue exploit
We will continue to monitor and provide updates on the Nyetya outbreak. To learn more about the Meraki MX, please visit our website or sign up for an upcoming webinar.
1Originally identified as ‘Petya’, the current outbreak is a Petya clone with additional enhancements including stronger encryption. The new offshoot is being described as “Not Petya” or Nyetya and also “GoldenEye”.