Hey there! Trying to decide between WPA2 Enterprise and WPA2 Personal for your Wi-Fi? It might sound super technical, but it really boils down to one simple question: how do you want to manage who gets onto your network?
Think of it this way: WPA2 Personal uses a single password for everyone. It's like having one house key that you share with family and friends—incredibly simple for a small setup. On the flip side, WPA2 Enterprise gives each user their own unique login, like an individual keycard for a secure office building. This is the gold standard for security and management in any larger environment, from a bustling corporate office to a university campus.
Choosing Your Wi-Fi Security: A Quick Comparison
When you're setting up a Wi-Fi network, the security protocol you choose is your first line of defense. For most homes or tiny businesses, the sheer simplicity of WPA2 Personal is often more than enough. It's straightforward, easy to set up, and gets the job done without much fuss.
But what about a busy Corporate office, an entire Education campus, or a multi-location Retail store? Handing out the same password to every employee, student, and device becomes a security nightmare, especially when you factor in modern Bring Your Own Device (BYOD) policies. This is exactly where WPA2 Enterprise, built on the 802.1X standard, shines.
It operates less like a single key and more like an individual keycard system. Each person gets their own credentials. When someone leaves, you just deactivate their "keycard" from a central system—without affecting anyone else's access. No more changing the Wi-Fi password for the entire company!
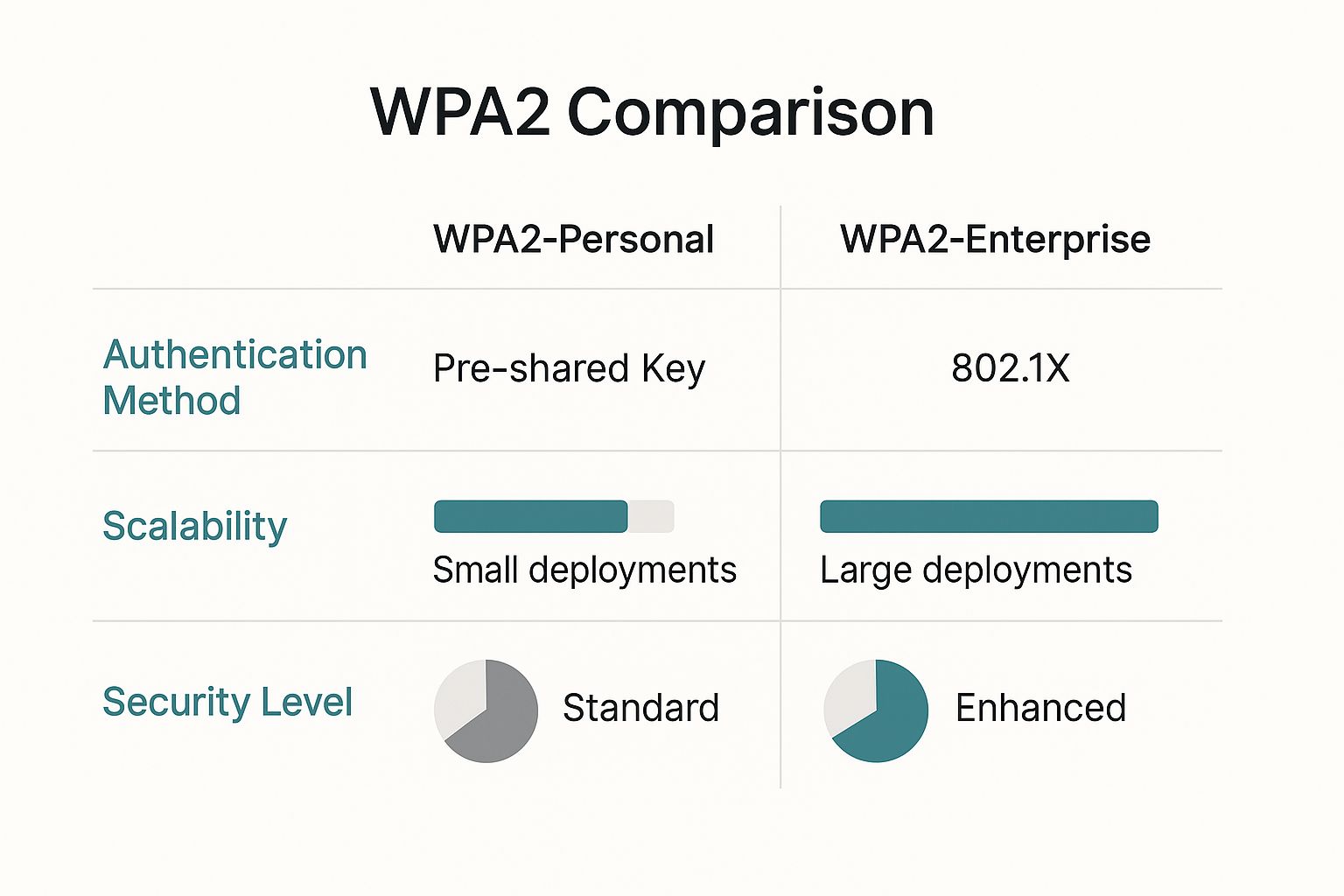
WPA2-Personal, also known as WPA2-PSK (Pre-Shared Key), is designed for simplicity. WPA2-Enterprise, however, uses a much more robust framework where every user is authenticated individually through a central server, like RADIUS. This makes it the clear choice for any organization that takes security seriously, especially in sectors like Education, Retail, and Corporate settings where BYOD is the norm.
This infographic breaks down the core differences in a really clear way.
As you can see, while WPA2-Personal is great for simplicity in small environments, Enterprise is built from the ground up for serious security and scalability.
WPA2 Personal vs Enterprise At a Glance
To cut through the noise, here’s a table that lays out the core differences side-by-side. It’s a quick way to see how each protocol stacks up in terms of Authentication, ideal use cases, and overall security.
| Feature | WPA2-Personal (PSK) | WPA2-Enterprise (802.1X) |
|---|---|---|
| Authentication | Single shared password for all users. | Unique username/password for each user. |
| Best For | Homes, small offices, basic guest networks. | Corporate, Education, Retail, BYOD environments. |
| Security | Standard; becomes vulnerable if the password is leaked or shared. | High; offers granular user control and detailed access logs. |
| Management | Simple to set up, but a headache to manage at scale. | Centralized via a RADIUS server (e.g., on Cisco Meraki). |
It's also worth a shout-out to some cool modern Authentication Solutions like IPSK (Individual Pre-Shared Key) and EasyPSK. They offer a hybrid approach, giving you unique keys for devices without the full complexity of a RADIUS server, often managed through a Captive Portal. You can learn more about the different types of security keys for Wi-Fi and find the right fit for your needs.
Ultimately, the choice depends entirely on your environment's scale and security requirements.
The Critical Difference in Network Security
When you dig into the WPA2 Enterprise vs Personal debate, the conversation always circles back to one thing: security. It's the most significant differentiator, and getting your head around it is key. Think of WPA2 Personal as handing out the same physical key to your front door to every single person—employees, guests, everyone. It works, but it's a huge security gamble.
This single, shared password is known as a Pre-Shared Key (PSK), and it creates a massive potential vulnerability. What happens when an employee leaves the company? Or when a student's laptop is stolen from the campus coffee shop? Your entire network is exposed until you change the password and distribute the new one to every single user. It's a disruptive, clumsy process that simply doesn't scale for growing businesses, especially in dynamic environments like Retail or busy Corporate offices.
That single point of failure is precisely the problem WPA2 Enterprise was built to solve.
Granular Control with Individual Credentials
WPA2 Enterprise flips the script entirely. Instead of one password for everyone, it authenticates each person individually. This is accomplished using the 802.1X standard, where every user connects with their own unique set of credentials (like a username and password). These credentials aren't checked by the Wi-Fi router itself, but by a central authentication server, typically a RADIUS server. It’s the same robust technology trusted by universities and large enterprises to secure their networks.
With WPA2 Enterprise, you are no longer managing a password; you are managing people. Access is tied to the individual, not to a shared secret that can be easily leaked or forgotten.
This changes everything from a management perspective. When an employee in a BYOD environment resigns or a student in an Education setting graduates, you don't have to scramble to change a shared password. You just disable their individual account. Instantly, their access is revoked, and no one else on the network is affected. This level of granular control is non-negotiable for any organization serious about protecting sensitive data. The contrast with WPA2 Personal is stark: one compromised device on a Personal network can put the whole system at risk. You can dive deeper into this topic by exploring the fundamental differences between WPA2 Personal vs Enterprise.
The Role of Modern Networking Platforms
Not too long ago, setting up WPA2 Enterprise was a daunting task, usually reserved for large organizations with big IT departments and budgets to match. That's not the case anymore. Modern networking platforms from innovators like Cisco have completely changed the landscape.
Cloud-managed solutions, such as Cisco Meraki, have made enterprise-grade security accessible for almost everyone by integrating RADIUS functionality right into their management dashboards. What used to require a dedicated server and specialized expertise can now be configured in minutes.
While WPA2 Enterprise with 802.1X is the gold standard, it's good to know there are other Authentication Solutions. Some offer a middle ground, like IPSK or EasyPSK, providing unique keys for each user or device without needing a full RADIUS setup. This flexibility means you can build a security strategy that truly fits your operational needs, whether you're a small business or a sprawling campus.
Real-World Use Cases in Retail, Education, and Corporate
Theory is great, but let's talk about where the rubber meets the road. How does the WPA2 Enterprise vs. WPA2 Personal choice play out in the real world? The right answer completely depends on the environment.
For a small, independent coffee shop or a local retail boutique, WPA2 Personal is usually the perfect fit. It’s incredibly straightforward to set up, needs no special hardware, and gets customers and staff online without any fuss. When you're only dealing with a handful of trusted devices, the security risk is manageable.
Scaling Up with Enterprise-Grade Security
But as soon as your organization starts to grow, the security landscape changes dramatically.
Take a large Corporate office that embraces a Bring-Your-Own-Device (BYOD) policy. In this setting, WPA2 Enterprise isn't just a nice-to-have; it's absolutely essential. It provides the only practical way to securely manage network access, protect sensitive company data on personal devices, and instantly revoke credentials when an employee leaves.
The need is even more apparent in Education. A university campus or school district has to manage network access for thousands of students, faculty, and guests, all with different needs and access rights. With WPA2 Enterprise, IT administrators can easily create distinct access roles. Students might get filtered internet access, while faculty can connect to internal servers and administrative resources. You can explore the unique challenges and solutions for providing secure Wi-Fi in schools in our detailed guide.
This is where networking solutions from providers like Cisco and its cloud-managed platform, Cisco Meraki, truly shine. They simplify what used to be a complex deployment of WPA2 Enterprise, making top-tier security much more accessible for multi-site Retail chains, sprawling campuses, and any growing business.
With WPA2 Enterprise, you move beyond a simple shared password and build a genuine authentication strategy. It gives you granular control to define who can access your network, what they can do once connected, and for how long.
The numbers back this up. While WPA2-Personal is dominant in small-scale settings, market data shows that over 80% of corporate and higher education institutions have already migrated to WPA2-Enterprise or newer standards. This shift is almost entirely driven by the security demands of BYOD and the need for regulatory compliance.
Beyond the Basic Login
Modern networks often go a step further by blending different authentication solutions for different user groups. For example, a Captive Portal can provide a branded, user-friendly login experience for guest access, while the core employee network remains secured with WPA2 Enterprise credentials.
There are also innovative approaches like IPSK (Identity Pre-Shared Key) or EasyPSK. These offer a powerful middle ground, giving each user or device a unique key without the full complexity of 802.1X. This is an ideal solution for environments that have a mix of corporate-owned devices and IoT gadgets that don't support traditional enterprise logins.
Comparing Management Overhead and Scalability
When you're weighing WPA2 Enterprise vs Personal, the conversation quickly moves beyond security features to the practicalities of day-to-day management. Let's be honest, WPA2 Personal is known for its incredible simplicity. You just choose a password, punch it into your router, and you're essentially done. But that ease of setup is deceptive and becomes a major liability as your network grows.
Think about the operational chaos of using a single password for a multi-location Retail business or across a university campus. What happens when an employee leaves or a laptop is stolen? The only truly secure move is to change the password for everyone. This means manually updating hundreds—if not thousands—of devices. It's an inefficient, disruptive process that creates a huge administrative bottleneck. Simply put, WPA2 Personal was never designed to scale.
This is precisely where WPA2 Enterprise demonstrates its value. It was engineered from the very beginning for large-scale deployments and centralized control.
Streamlining Operations with Centralized Management
WPA2 Enterprise flips the management model on its head. Instead of a chaotic, device-by-device free-for-all, you get a streamlined, centralized system. Historically, this meant setting up and maintaining a dedicated RADIUS server, which was often a complex undertaking. Thankfully, modern authentication solutions have completely changed that landscape.
Cloud-managed networking platforms, especially from leaders like Cisco Meraki, have made enterprise-grade Wi-Fi far more accessible. Many of these platforms bake RADIUS functionality directly into their management dashboards or integrate smoothly with cloud identity providers. This change has dismantled the old barriers to entry, making top-tier security a realistic option for Corporate, Education, and Retail environments of any size.
The initial investment in setting up WPA2 Enterprise pays for itself over and over again. You stop managing countless shared passwords and start managing individual user identities, which is a fundamentally more secure and efficient model for any organization.
Look at how it transforms routine administrative tasks:
- Onboarding: A new hire in a BYOD environment can get secure network access with their personal credentials. IT can grant this access in seconds from a single dashboard.
- Offboarding: When an employee leaves the company, their access can be revoked instantly without disrupting a single other user on the network.
- Monitoring: Your IT team gets a clear view of who is connected, which devices they're using, and when they’re accessing the network.
This level of granular control is a world away from the all-or-nothing approach of WPA2 Personal.
The Rise of Hybrid Authentication Solutions
For organizations that need something more robust than WPA2 Personal but find a full WPA2 Enterprise setup to be overkill for certain situations, there are fantastic hybrid authentication solutions available. Technologies like IPSK (Identity Pre-Shared Key) or EasyPSK neatly bridge this gap. They empower administrators to issue a unique password for each user or device, giving you granular control without the full 802.1X infrastructure.
This approach is incredibly useful in places like student dorms or for connecting IoT devices that lack support for enterprise-level logins. These solutions are often managed through a straightforward Captive Portal, offering a major security upgrade over a single shared password while keeping the management overhead low. Ultimately, platforms from providers like Cisco offer the flexibility to mix and match, so you can apply the right level of security and management exactly where you need it.
Exploring Modern Authentication Solutions Like IPSK
The debate over WPA2 Enterprise vs Personal can sometimes feel like a choice between two extremes. What happens when your needs fall somewhere in the middle? Many organizations need much more security than a single password offers but aren't quite ready to manage a full 802.1X deployment. This is where modern authentication solutions create a practical bridge between simplicity and robust security.
You’ve almost certainly encountered Captive Portals. They’re the branded login pages at hotels, airports, and coffee shops that require you to agree to terms or enter an email to get online. While they're excellent for managing guest access in Retail or hospitality, they don't fundamentally secure the connection itself.
A Hybrid Approach with IPSK and EasyPSK
For a major security boost without the complexity of a RADIUS server, technologies like Identity Pre-Shared Key (IPSK) or EasyPSK are a revelation. Originally championed by networking leaders like Cisco Meraki, IPSK allows you to assign a unique password to each user or device, all while operating within the familiar WPA2-Personal framework.
This simple concept solves the single biggest security problem of a shared password. If an employee in a Corporate BYOD environment loses their laptop, you just revoke their specific key. When a student leaves a university, their access can be instantly cut off without affecting anyone else. To see how this can be implemented, you can learn more about setting up IPSK with RADIUS authentication for even greater flexibility.
This screenshot shows a typical setup for a modern authentication solution.
The real magic is the ability to generate and manage unique keys for individuals or groups. This gives you fine-grained control without forcing you to completely re-engineer your network infrastructure.
IPSK provides the user-specific control of WPA2 Enterprise with the straightforward setup of WPA2 Personal. It's the ideal middle ground for securing environments with diverse device types, like IoT gadgets, smart TVs, and printers, that don't support 802.1X.
This hybrid model is a perfect fit for scenarios where a single password just doesn't offer enough accountability. Think of a student housing complex, a multi-tenant office building, or a Retail store balancing corporate devices with guest access. IPSK delivers a much stronger security posture and far simpler management, making it one of the most practical authentication solutions for today's diverse networks.
Making the Right Choice for Your Network
So, how do you decide? When you're weighing WPA2 Enterprise vs Personal, the choice really comes down to your specific environment. Thankfully, once you know what to look for, the right path is usually pretty clear.
For your home network or maybe a tiny office with a few trusted devices, WPA2 Personal is perfectly fine. It’s straightforward, it works, and you don't have to deal with any extra complexity. But the second you start managing multiple users, handling sensitive data, or trying to support a BYOD policy, the conversation changes entirely.
Your Decision Checklist
For any real organization—a Corporate office, a busy Retail shop, or an Education campus—WPA2 Enterprise is the only serious choice. The security, scalability, and fine-grained control it offers are foundational for a modern, secure network.
Not sure where you land? Run through this quick checklist:
- User Count: Do you have more than 10-15 people connecting to the Wi-Fi? If the answer is yes, managing unique credentials with Enterprise is vastly more secure and sensible than passing around a single password that never changes.
- Data Sensitivity: Are your users accessing confidential client information, financial records, or other sensitive data over the wireless network? Enterprise-level encryption and individual authentication are non-negotiable for protecting that data.
- Device Management: Do you have a BYOD policy or need a solid plan for guest access? With Enterprise, you can instantly revoke a former employee's access without forcing every other user to re-enter a new password.
This decision tree gives you a great visual for when to make the jump.
As the flowchart shows, the minute your needs for security and user management grow, WPA2 Enterprise becomes the clear winner.
Finding the Right Solution
Deploying WPA2 Enterprise used to be a headache, but modern platforms from providers like Cisco and Meraki have made it much more accessible. But what about guests? This is where a hybrid approach often works best. You can lock down your primary network with Enterprise and use Captive Portals for visitor access. If that sounds like what you need, our guide on how to set up guest Wi-Fi securely is a great next step.
For those edge cases where a single password isn't enough but a full 802.1X implementation feels like overkill, there are some great middle-ground options. Authentication Solutions like IPSK or EasyPSK can provide a unique key for each user without all the heavy infrastructure, giving you the best of both worlds.
Answering Your Lingering Questions
After breaking down the core differences between WPA2 Enterprise and Personal, you probably still have a few specific questions bouncing around. That's completely normal. Let's dig into some of the most common concerns we hear from organizations trying to choose the right path.
We'll clear up any lingering confusion about complexity, handling guest access, and some of the newer authentication solutions out there. The goal is to give you the confidence to make the right call for your business.
Is WPA2 Enterprise Really Too Complicated for a Medium-Sized Business?
This is a common misconception, but the short answer is no, not anymore. In the past, setting up WPA2 Enterprise meant wrestling with on-premise RADIUS servers and required some serious IT muscle. But the game has changed.
Modern cloud-managed networking platforms, like Cisco Meraki, have made deploying WPA2 Enterprise incredibly straightforward. Many of these systems come with built-in RADIUS server capabilities or integrate seamlessly with cloud identity providers. What once took a specialized team days to set up can often be configured in less than an hour, making the massive security upgrade well worth the minimal effort for most Corporate and Retail businesses.
How Should I Handle Guest Wi-Fi with WPA2 Enterprise?
While you could technically use WPA2 Enterprise for guests, a hybrid approach is almost always the more practical and secure solution. Think of it as a two-track system. Your primary, secure network for employees in a BYOD environment should absolutely run on WPA2 Enterprise, with each person using their unique credentials.
For visitors, the best practice is to set up a completely separate guest network on a different SSID. This network can use a Captive Portal for authentication. This not only isolates guest traffic from your internal network but also gives you a branded login page where you can display terms of service or even capture user details for marketing.
This two-pronged strategy delivers the best of both worlds: rock-solid, certificate-based security for your team and a simple, controlled login experience for guests. It’s the go-to setup for most Education campuses and large-scale Retail environments.
What is IPSK and Where Does it Fit In?
IPSK, or Identity Pre-Shared Key, is a brilliant middle-ground solution. You might also hear it called EasyPSK. It works much like WPA2 Personal, where devices connect with a pre-shared key, but here's the crucial difference: each user or device gets its own unique key.
This single change patches the biggest security hole in the traditional single-password model. If an employee leaves or a device's key is compromised, you just revoke that one specific key. No more changing the password for the entire organization and reconnecting every single device. It’s an ideal choice when you need more security than a single password but have devices that can't handle the client software for a full WPA2 Enterprise setup—think printers, IoT sensors, or smart TVs.
At Splash Access, our entire focus is on making these advanced Wi-Fi Authentication Solutions simple to deploy and manage. Whether you need an elegant Captive Portal for your guests, a streamlined IPSK solution for your mix of devices, or full WPA2 Enterprise integration with your Cisco Meraki network, our platform is built to make it happen. Find out how we can help you create a secure, branded, and data-rich Wi-Fi experience at https://www.splashaccess.com.