Hey, when the Wi-Fi goes down, everything just stops, right? It’s a frustratingly familiar feeling—a video call freezes mid-sentence, a retail payment terminal refuses to connect, or a critical file just won’t download. Let's be real: unreliable Wi-Fi isn't just a minor tech hiccup anymore; it's a genuine operational crisis that can hit your productivity, customer happiness, and even your revenue.
Why Stable Wi-Fi Is No Longer a Nice-to-Have
Let's be honest, when the internet connection drops, so does everyone's patience and productivity. We are well past the point where wireless access was a simple convenience. Today, it’s the absolute foundation of how modern businesses run, particularly in places with heavy foot traffic and high demand like in the education, retail, and corporate sectors.
This reliance is especially obvious in environments like retail stores, schools, and busy corporate offices. An unstable connection is more than just a headache for the IT department—it's a direct threat to your bottom line and the experience you provide to your users.
The Real Cost in Different Sectors
The fallout from poor connectivity looks different depending on the industry, but the impact is always significant. Each sector has its own set of challenges, which is exactly what a robust network built on hardware like Cisco Meraki is engineered to handle.
- Education: In a classroom, a dropped connection disrupts the entire flow of a lesson. Online resources become unreachable, and both students and teachers get frustrated. With digital learning now a standard, consistent uptime is simply not negotiable.
- Retail: For any retail shop, spotty Wi-Fi can mean failed transactions at the point-of-sale, employees unable to check inventory on the floor, and a frustrating experience for shoppers who expect to connect to a guest network.
- Corporate BYOD: In offices embracing a Bring Your Own Device (BYOD) policy, the network has to juggle a massive and unpredictable number of devices securely. When it fails, you’re looking at lost work hours and gaping security holes.
The heart of the problem is that our dependence on Wi-Fi has grown much faster than the capabilities of older, poorly configured networks. Every dropped signal is a missed opportunity—a lost sale, a disrupted class, or a delayed project.
The BYOD and Device Explosion
One of the biggest culprits behind modern wi-fi connectivity issues is the incredible number of devices all trying to connect at once. We're not just talking about laptops anymore. Think smartphones, tablets, smartwatches, and a whole host of IoT sensors all fighting for the same slice of bandwidth. This device explosion, especially in a corporate BYOD environment, is a recipe for network congestion.
This trend is a big reason the global Wi-Fi chipset market hit $20.5 billion in 2024 and continues to climb, driven by our ever-growing appetite for connected gadgets. This flood of devices is a primary cause for overloaded networks, leading to the slowdowns and dropouts we all know and hate.
To effectively manage this device-heavy reality, you need smart security and authentication. This is precisely where tools like a Captive Portal for guest access or advanced Authentication Solutions like IPSK and EasyPSK become critical for keeping things orderly and secure without making the login process a nightmare for users.
Pinpointing the Cause of Your Wi-Fi Problems
Before you can fix those frustrating connection drops, you need to put on your detective hat. Getting to the root cause of your Wi-Fi connectivity issues is the most critical first step, and honestly, the culprit is almost always tied to your specific environment. The problems that bring a university network to its knees are totally different from what plagues a retail store or a busy corporate office.
So, let's break down the "why" behind poor performance on your Cisco Meraki network. By digging into the unique challenges of different sectors, we can stop guessing and start solving.
The Education Conundrum: High Density and BYOD
Walk into any modern university lecture hall or student dorm, and you’re stepping into a perfect storm for Wi-Fi trouble. It’s a classic high-density demand scenario common in the Education sector. You’ve got hundreds of students, each with a laptop, a smartphone, and maybe a tablet, all trying to get online at the exact same time.
This massive device count creates a couple of immediate, network-crushing problems:
- Channel Congestion: Think of Wi-Fi channels as lanes on a highway. When too many devices try to cram into the same lane, traffic grinds to a halt. In a packed auditorium, that congestion means slow speeds and dropped connections for everyone.
- BYOD Management: Every single one of those student-owned devices is a unique variable. Just trying to manage access and maintain security for this Bring-Your-Own-Device flood is a monumental task if you don't have the right authentication solutions in place.
This is where things like a smart Captive Portal for onboarding or using IPSK (Identity Pre-Shared Key) become absolute game-changers. An EasyPSK solution, for example, can give each student a unique key, making access control manageable even when dealing with thousands of users.
Retail Wi-Fi: Interference and Guest Expectations
In a retail store, the challenges feel different but are just as disruptive. Your network has to reliably support business-critical systems like payment terminals while also offering seamless guest Wi-Fi to shoppers.
The prime suspect here is often interference. Things you wouldn't even think of—wireless payment systems, security cameras, even the microwave in the breakroom—can create "noise" that messes with the Wi-Fi signal. If you want to dive deeper, you can learn more about the common sources of interference with WiFi that might be affecting your network.
For retail, you're always balancing two goals: protecting your operational network from interference and providing a frictionless login for guests. A slow or complicated guest network doesn't just annoy shoppers; it's a bad reflection on your brand.
A properly configured Cisco Meraki network can segment guest traffic away from your internal systems. From there, a Captive Portal can make the login process as simple as entering an email address or connecting with a social media account.
The Corporate BYOD Security Web
Corporate offices with a BYOD policy face their own tangled web of security and management headaches. The mission is to give employees easy access to the resources they need on their personal devices, all without swinging the door wide open for security threats.
A single, shared Wi-Fi password is just a security incident waiting to happen. When an employee leaves, you have to change the password for everyone, which is a massive disruption. This is precisely the kind of Wi-Fi connectivity issue that modern authentication solutions were built to prevent.
By using a system like EasyPSK on your Cisco Meraki network, you can issue individual, secure credentials for each employee's devices. Now, when someone leaves the company, you just revoke their key. No one else is impacted. It’s a clean, secure, and surprisingly user-friendly way to manage a complex BYOD environment.
Streamlining Logins with a Smart Captive Portal
Let’s be honest, that first login experience can make or break a user's perception of your Wi-Fi. When a student, shopper, or employee struggles to connect, the first thing they blame is the network. A clunky, confusing, or broken login process is one of the most common causes of Wi-Fi connectivity issues, and it happens before they even get online.
This is where a well-designed Captive Portal becomes your most valuable player.
Instead of seeing it as just a gatekeeper, think of a captive portal as a friendly welcome mat. When you pair it with powerful hardware like Cisco Meraki, the entire authentication process is transformed from a frustrating chore into a smooth, branded interaction. Solutions like Splash Access are built specifically for this, turning a huge pain point into a genuine strategic advantage for your organization.
Making Logins Effortless and Smart
The real magic of a modern Captive Portal lies in its flexibility. You can finally ditch the old, tired "enter a long, complicated password" routine and offer login methods that actually make sense for your users. The goal here is simple: eliminate authentication as a source of connectivity problems.
Different environments have different needs, and a smart portal can adapt beautifully:
- Retail: For shoppers, speed is everything. Offering one-click logins through social media or a simple email entry field gets them connected without a fuss. It's fast, easy, and keeps them happy.
- Education: In a university or school, security and proper identification are non-negotiable. This is a perfect use case for Single Sign-On (SSO), where you integrate the portal with existing school directories. Students and staff can log in with the same credentials they use for everything else.
- BYOD Corporate: For guests visiting your office, a simple, self-service registration process is ideal. It captures necessary visitor information and grants temporary, secure access, keeping your internal network safe while making life easy for visitors.
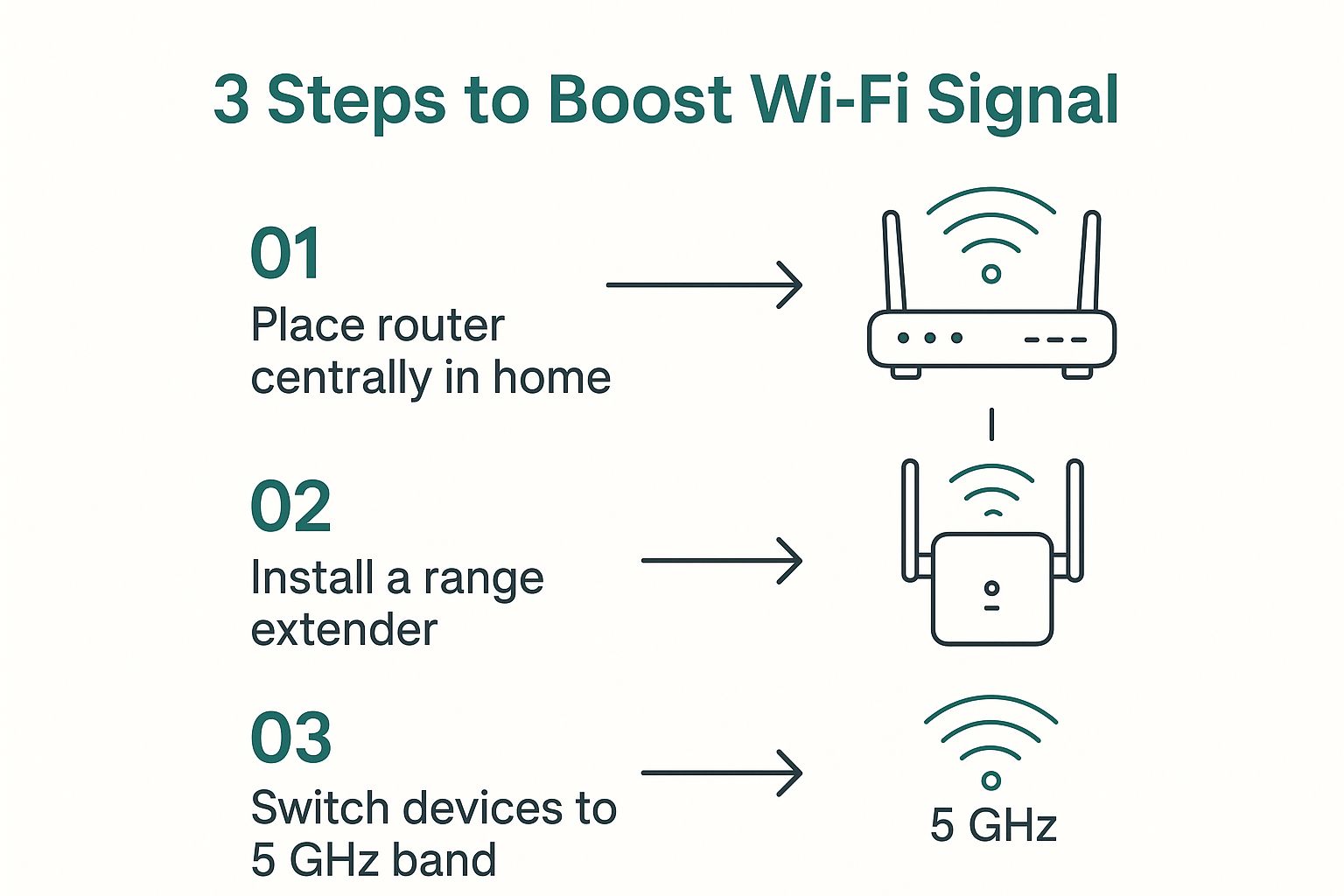
The image below gives a few simple, universal tips for improving a Wi-Fi signal, which perfectly complements the goal of creating a frictionless connection from start to finish.
As you can see, a great Wi-Fi experience is about more than just strong signals; it's also about a smart, user-friendly access experience.
Common Authentication Issues and Captive Portal Solutions
Too often, IT teams chase down "bad Wi-Fi" reports that are actually just authentication headaches. The following table breaks down some of the most frequent login challenges and shows how a smart Captive Portal on a Cisco Meraki network can solve them.
| Authentication Challenge | Impact on Users & IT | How a Captive Portal Solves It |
|---|---|---|
| Complex Password Requirements | Users forget passwords, leading to frustration and increased IT support tickets for password resets. | Offers simple login options like social media (Facebook, Google), email forms, or one-time codes, eliminating password friction. |
| Insecure Shared Passwords | A single shared key for guests is a security risk. If it leaks, anyone can access the network. | Provides individual, time-limited access for each user. It also logs each connection, improving security and accountability. |
| Lack of User Identification | In a BYOD Corporate or Education setting, anonymous access makes it hard to track usage or enforce policies. | Integrates with Single Sign-On (SSO) or requires registration, tying network access to a verified identity. |
| Poor User Onboarding | A generic, unbranded login page looks unprofessional and can be confusing for users. | Delivers a fully branded, customized splash page that provides clear instructions, reinforces brand trust, and can display terms and conditions. |
Ultimately, by getting the login experience right, you cut down on unnecessary support requests and give users a seamless, professional first impression of your network.
Beyond Just a Login Page
A great Captive Portal does more than just authenticate users; it's a powerful tool for branding, security, and compliance. When you customize the splash page on your Cisco Meraki network, you're not just providing a connection—you're creating a consistent brand experience. This is your chance to display promotions in a retail store, share important campus announcements in education, or reinforce your company’s brand in a corporate setting.
Key Takeaway: A user who can't figure out how to log in will report a "Wi-Fi problem," even if the network itself is perfectly healthy. A smart portal solves this user-facing issue before it ever becomes a support ticket.
These portals are also essential for modern security. One of the best authentication solutions for corporate and school environments is Single Sign-On (SSO). It allows users to access multiple applications with a single set of credentials managed by a central identity provider. To learn more, explore the benefits of Single Sign-On.
For environments with heavy BYOD Corporate use or in large-scale education deployments, you might need even more advanced methods like IPSK and EasyPSK. These solutions, which we'll cover next, take security to another level by assigning a unique key to each device. But even they rely on a smooth onboarding process, which is often initiated through the captive portal. By streamlining that first step, you pave the way for a more secure and reliable network experience for everyone.
Securing Your BYOD Network with EasyPSK
Bring Your Own Device (BYOD) policies sound great in theory—they offer flexibility and freedom. But for the IT team on the ground, they can quickly spiral into a security and management nightmare. When you're dealing with a constant flood of personal devices from students, staff, or employees, you realize that most Wi-Fi connectivity issues don't start with a bad signal. They start with messy, insecure authentication.
The old-school approach of using a single, shared password for everyone is a disaster waiting to happen. It’s not just inconvenient; it’s a massive security risk that gets passed around faster than office gossip. The real fix lies in smarter authentication solutions built to handle the scale and variety of a modern network.
Moving Beyond the Single Shared Password
That one-password-fits-all model is fundamentally broken, especially in sectors like Education, Retail, and BYOD Corporate environments. Think about it: when an employee leaves or a student misplaces their laptop, what’s your only move? You have to change the password for everyone, creating a major headache and disrupting the entire organization.
This is where a technology like Identity Pre-Shared Key (IPSK) completely changes the game. Instead of one key for the whole network, IPSK gives you the power to assign a unique, private password to every single user or device. They all connect to the same Wi-Fi network name (SSID), but each one has its own individual key.
The core idea is simple but incredibly effective: security should be personal. By tying network access directly to an individual or their specific device, you gain phenomenal control without creating a frustrating experience for your users.
This method has become the gold standard for managing large numbers of devices, especially on a Cisco Meraki infrastructure. But a new question arises: how do you deploy and manage thousands of unique keys without creating a massive administrative bottleneck?
That’s where EasyPSK comes in.
Making Advanced Security Practical with EasyPSK
EasyPSK is Splash Access's practical and powerful take on the IPSK concept, designed to integrate seamlessly with Cisco Meraki networks. It takes the robust theory of individual keys and makes it surprisingly simple to manage, even at a scale of thousands of users.
Here’s a simple way to look at it: Your Captive Portal acts as the friendly front door, welcoming users and confirming who they are. Once they’re verified, EasyPSK is the system working behind the scenes, automatically generating and assigning their personal, secure Wi-Fi key.
This process delivers some huge advantages:
- Granular Control: You can set expiration dates for keys, limit the number of devices a user can connect, and even assign different bandwidth profiles based on user groups.
- Painless Revocation: If a device is lost or an employee leaves, you just revoke their specific key from the dashboard. Nobody else is affected, and the network stays secure.
- Seamless User Experience: From the user's perspective, the process is incredibly smooth. They log in once through the portal, get a key, and can use it on all their devices without having to log in over and over.
For any organization struggling to get a handle on its BYOD environment, this is the logical next step. It shifts Wi-Fi security from a clumsy, all-or-nothing system to a precise and automated one.
Real-World Scenarios in Education and Corporate Settings
In a university setting, EasyPSK can automate the entire Wi-Fi onboarding process for student housing. When a student moves in, they register their phone, laptop, and gaming console through a self-service portal. The system then issues a unique key that's valid for the entire school year, which instantly stops password sharing between dorms and dramatically cuts down on IT support tickets.
In a BYOD Corporate environment, the process is just as smooth. A new hire can be onboarded with a key that grants them network access appropriate to their role. The moment they leave the company, their access is cut off by revoking that one key, instantly closing a common and dangerous security hole.
There are many ways to implement this, and you can explore different methods for deploying security keys for WiFi to find what works best for your organization. Ultimately, this approach turns the chaos of managing a constant churn of users and devices into a secure, manageable process.
Fine-Tuning Your Cisco Meraki Network Performance
Owning powerful Cisco Meraki hardware is one thing, but truly mastering it to eliminate wi-fi connectivity issues is where the real skill comes in. This isn't about just plugging in an access point and crossing your fingers. It's about getting your hands dirty in the settings to actively manage your wireless environment and build a rock-solid user experience.
Think of your Meraki dashboard as the command center for your network's health. It’s loaded with professional-grade tools that, if you know how to use them, can help you hunt down and squash the root causes of poor performance. Whether you're dealing with a packed auditorium in education or a busy checkout line in retail, the key is to be proactive, not reactive.
Hunting for Trouble with RF Spectrum Analysis
One of the most potent tools in your arsenal is the RF (Radio Frequency) spectrum analysis. It gives you a superpower: the ability to see the invisible noise that can absolutely cripple your Wi-Fi signal. I've used this to uncover everything from rogue Bluetooth devices and breakroom microwaves to old, noisy security cameras causing interference.
When you run an RF analysis, you can pinpoint these problematic frequencies. From there, you can manually adjust your channel plan, essentially steering your critical traffic onto a cleaner, less congested "highway." This is a non-negotiable step in high-density environments where every sliver of spectrum is precious real estate.
The goal here is simple: find a clear, open road for your Wi-Fi signal. RF analysis turns what used to be guesswork into a sharp, data-driven decision.
Intelligent Bandwidth Shaping for Fair Usage
Let's be honest, not all network traffic is created equal. A student streaming a 4K movie in their dorm room shouldn't choke out the connection for someone else trying to access an online textbook. This is exactly what bandwidth limits and traffic shaping are for.
Inside the Meraki dashboard, you can set up some smart rules to ensure everyone gets their fair share of the connection. I've found a few approaches work particularly well:
- Per-Client Limit: This is the simplest fix. Just cap the maximum bandwidth for each individual device. It’s a straightforward but incredibly effective way to stop one heavy user from tanking the network for everyone else.
- Per-SSID Limit: You can apply a total bandwidth limit to a specific network, like your guest Wi-Fi. This is great for making sure your primary operational network—the one for staff or critical systems—always has the resources it needs.
- Application Shaping: This is where it gets really granular. You can prioritize what truly matters, like payment processing in a retail store or learning management systems in a school, over things like social media or video streaming.
These controls are a lifesaver, especially in BYOD Corporate environments where you have zero control over what apps people are running. By managing bandwidth this way, you stop resource hogs from manufacturing wi-fi connectivity issues for the entire office.
Using Client Tracking to Find Dead Zones
You know that one corner of the office where someone is always complaining about a bad connection? The client tracking feature in your Meraki dashboard is how you solve that mystery. It shows you, in real-time and historically, exactly where every device is connected, what its signal strength looks like, and which access point it's latched onto.
This data is gold for diagnosing physical-layer problems. If you see a cluster of clients with weak signals all huddled in one area, you've just found a coverage dead zone. Now you can make an informed choice: either reposition a nearby AP or, more likely, add a new one to fill that gap.
Of course, the challenges are always evolving. As we look toward future advancements like 6G and new Wi-Fi standards, the pressure on our networks only grows. More devices and richer content are constantly straining capacity, while cybersecurity threats get more sophisticated. You can find out more about how 2025 connectivity trends are shaping our networks. This reality makes proactive network tuning more critical than ever.
Pro Tips for High-Density Deployments
Configuring APs for places like lecture halls, concert venues, or bustling retail floors is a different ballgame. In these high-density situations, your main goal is to cut down on "airtime" consumption and interference between your own access points.
It might sound counterintuitive, but start by lowering the transmit power on your APs. This shrinks the coverage cell for each AP, which has the brilliant side effect of forcing clients to connect to the access point that's physically closest to them. This dramatically reduces co-channel interference and helps spread the device load much more evenly across your hardware. Pair this technique with a smart channel plan, and you'll have a network that performs flawlessly, even when it's packed to the rafters.
Your Wi-Fi Questions Answered
We get a lot of the same questions from organizations wrestling with tricky Wi-Fi connectivity issues. It's a common struggle. So, to help out, we’ve put together some straightforward answers to guide you through solving these headaches and getting the most out of your Cisco Meraki and Splash Access setup.
Let's dive into the specifics and clear up some of the confusion around modern Wi-Fi management.
How Can a Captive Portal Improve My Retail Store Wi-Fi?
In retail, a Captive Portal is so much more than a login screen—it’s your digital front door. When a customer connects to your Wi-Fi, you have a golden opportunity to greet them with a fully branded page. You can showcase your latest promotions, invite them to join a loyalty program, or point them to your social media.
With a tool like Splash Access layered on your Cisco Meraki network, you can offer simple one-click logins via social media or email. This instantly solves the friction of remembering complex passwords. More importantly, it helps you gather valuable marketing insights (with user consent, of course) to better understand your shoppers. You're not just giving away free Wi-Fi; you're creating a powerful business tool that elevates the customer experience.
What Makes EasyPSK Better for Our School BYOD Network?
EasyPSK, a form of Identity Pre-Shared Key (IPSK), is a massive security upgrade for any campus in the education sector. Forget relying on a single password for everyone—a password that inevitably gets shared and becomes a liability. EasyPSK lets you give each student and staff member their own unique, personal key.
What's really great is that they all use this personal key to connect to the same Wi-Fi network name (SSID). So, if a student leaves the school or a device is lost, you just disable that one key from a central dashboard. Nobody else is affected. For a Cisco Meraki network managing hundreds or thousands of personal devices, this approach makes security both stronger and far simpler to manage.
The real win here is accountability and control. When network access is tied to an individual, you eliminate the chaos of shared credentials and gain a crystal-clear picture of who is on your network at all times.
My Wi-Fi Slows Down in Crowded Areas. Can Cisco Meraki Fix This?
Absolutely. Slow Wi-Fi in crowded places is a classic high-density problem, and Cisco Meraki hardware is built specifically to handle this exact scenario. The key is to actively manage the airwaves using the tools right inside the Meraki dashboard.
You can lean on RF optimization features that automatically scan the environment and shift your wireless channels to sidestep interference from neighboring networks. You can also implement traffic shaping rules to prioritize what's important—for example, making sure educational apps get more bandwidth than YouTube during class. By looking at client data, you can spot where device density is highest and fine-tune your access point placement and power levels, smoothing out performance for everyone, even during the busiest periods.
Can I Securely Use One Wi-Fi Network for Both Guests and Staff?
Yes, and it’s a smart, efficient way to simplify your network without cutting corners on security. With a Cisco Meraki network that uses Authentication Solutions like Splash Access, you can broadcast a single SSID that intelligently routes users based on who they are.
Here’s how it works in the real world:
- Guests: A visitor connects and sees a branded Captive Portal. They might log in with their social media account or email, which then places them on a separate, firewalled network with restricted access.
- Staff: An employee connects to that exact same network name but logs in with their secure company credentials, like an EasyPSK key. The system recognizes them and grants full, secure access to internal company resources.
From the user's perspective, it feels like one simple network. But behind the scenes, you’re maintaining strict segmentation and control, preventing wi-fi connectivity issues and keeping your sensitive data completely safe. It’s the best of both worlds—simplicity for them, robust security for you.
Ready to turn your Wi-Fi from a source of frustration into a powerful asset? Splash Access integrates seamlessly with your Cisco Meraki hardware to deliver secure, branded, and frictionless connectivity. Start your free trial today and see for yourself how easy it can be.