Let's get straight to the point, shall we? The old way of thinking about network security is pretty much broken. Zero Trust is a totally different approach, and it’s built on a single, powerful idea: never trust, always verify.
Think of it like a top-secret government building. It doesn't matter if you're a five-star general or a first-day intern; you're not getting through any door without proving who you are, every single time. That’s the Zero Trust mindset in a nutshell.
Moving Beyond The Castle-And-Moat
For decades, security was all about building a digital "castle-and-moat." If you were safely inside the network's walls, you were considered trustworthy. Simple, right? But that model is now dangerously outdated.
Today, the "network" isn't a single place anymore. Your employees are working from home, your students are in dorms, your guests are bringing their own devices (BYOD), and critical applications live in the cloud. The perimeter has dissolved. Zero Trust assumes that threats aren't just outside the walls; they could already be inside. It challenges every access request, no matter where it comes from.
Zero Trust vs Traditional Security
The shift from the old model to Zero Trust is a big one. It’s not just an upgrade; it's a complete philosophical change in how we approach security.
This table breaks down the core differences in a friendly way:
| Security Principle | Traditional 'Castle-and-Moat' Model | Modern Zero Trust Model |
|---|---|---|
| Default Trust Level | Implicit Trust: Anyone inside the network is trusted by default. | Explicit Denial: No one is trusted by default, inside or outside. |
| Verification | One-Time Check: Authenticate once at the perimeter (the "moat"). | Continuous Verification: Authenticate and authorize for every access request. |
| Focus | Network Location: Security is based on where a user is. | User & Device Identity: Security is based on who the user is and the health of their device. |
| Access Control | Broad Access: Once inside, users often have wide-ranging access. | Least Privilege: Users get the minimum access needed to do their job, and nothing more. |
| Threat Assumption | External Threats: Assumes bad actors are outside the network. | Internal & External Threats: Assumes a breach is always possible and threats can exist anywhere. |
Ultimately, the castle-and-moat model protects a perimeter that no longer truly exists. Zero Trust, on the other hand, is designed for the reality of modern, distributed networks, especially when using tech from partners like Cisco Meraki.
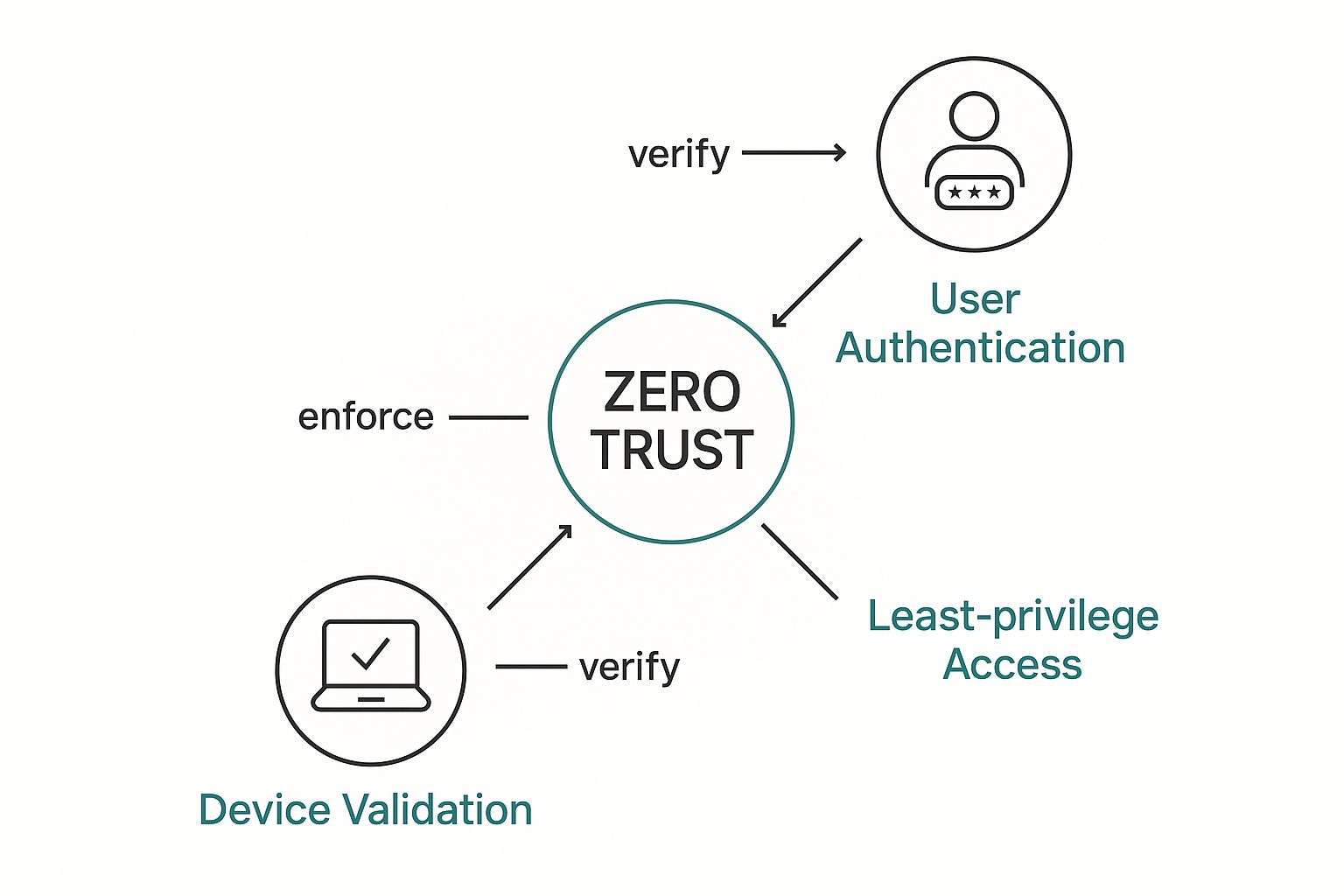
The 3 Core Pillars of Zero Trust
So, how does this actually work? Zero Trust isn't just one technology; it's a strategy built on three foundational pillars that work together. You don't just build a bigger wall; you create smarter, more dynamic checkpoints throughout your entire environment.
As this shows, the model relies on verifying the user, validating their device, and enforcing intelligent policies before granting access to anything. It’s a constant cycle of checks and balances.
How To Implement Zero Trust on Your Network
Putting this philosophy into practice might sound a bit intimidating, but it's more achievable than you think, especially with modern tools. For example, when it comes to Wi-Fi access in a busy Retail store, a large Education campus, or a BYOD Corporate office, you're already halfway there if you're using the right solutions.
Technologies like Captive Portals are a perfect real-world example. Before a guest can even think about getting online, the portal stops them and requires them to authenticate. That's a core Zero Trust action right there: verify first. We dive deeper into the practical steps in our guide on how to set up guest Wi-Fi securely.
This isn't just for guests, either. Advanced Authentication Solutions like IPSK or EasyPSK are used to grant different levels of access to employees, contractors, and even IoT devices, all based on their verified identity. The goal is to move away from trusting a physical connection and start trusting a validated identity.
The Core Principles of a Zero Trust Framework
Alright, so we’ve left the old "castle-and-moat" security model behind. Now, let's dig into what actually makes a Zero Trust framework tick. This isn't about buying a single piece of software; it's a completely different way of thinking about security, built on a few core, almost common-sense, principles. When you bring them together, they create a much smarter and more resilient defense for any modern business.
Think of these as the non-negotiable rules your security system must follow. They work together to inspect every single connection, making sure trust is something that's earned, not just given away.
Verify Continuously and Assume a Breach
The first and most important rule of Zero Trust is to never trust anyone by default. It doesn't matter if they're inside or outside your office walls. This approach operates from the get-go with the assumption that a threat might already be on your network.
This means every access request, without exception, has to be authenticated and authorized. We're talking about employees in the building, remote staff at home, or even a guest hopping on your Wi-Fi. This constant, relentless verification is the foundation of the whole strategy.
A Zero Trust model assumes that an organization's network will be compromised or the perimeter will fail, challenging all users and devices to prove that they're not attackers.
This mindset is a game-changer, especially for modern Wi-Fi networks in places like Retail stores, Education campuses, or Corporate offices with BYOD (Bring Your Own Device) policies. A Cisco Meraki network, for example, can be set up to enforce this with a Captive Portal, which essentially stops every device at a digital checkpoint to demand credentials before it can connect.
Enforce the Principle of Least Privilege
Once a user or device proves who they are, the next principle kicks in: give them the absolute minimum level of access they need to do their job, and not an ounce more. This is what we call the principle of least privilege.
It’s like giving a guest a keycard that only opens the meeting room door, not the server room or the CEO's office. You’re drastically shrinking the potential damage an attacker could do if they ever managed to compromise that one account. In a BYOD world, this isn't just a good idea—it's essential.
Here’s what that looks like in the real world:
- A student in their dorm gets internet access but is walled off from the sensitive faculty network.
- A retail employee on the sales floor can use the inventory app on their tablet but can't touch the company's financial records.
- A corporate guest can use the public Wi-Fi, but they are completely isolated from all internal company resources.
This is where advanced Authentication Solutions like IPSK (Identity Pre-Shared Key) or EasyPSK really shine. They let you assign a unique, individual key to each user or device, tying their access permissions directly to their identity. This kind of granular control is a cornerstone of effective Zero Trust and a key part of our guide to network security for small businesses.
Use Micro-segmentation to Contain Threats
Finally, a Zero Trust strategy involves breaking your network up into many small, isolated zones—a practice known as micro-segmentation. The goal here is damage control. If a breach happens in one little segment, it's trapped there and can't spread like wildfire across your entire network.
Think of it like the watertight compartments in a submarine. One leak won't sink the whole boat. For a business, this could mean that a compromised payment terminal in a Retail shop can't get anywhere near the back-office servers.
By weaving these three principles together, you build a security framework that is proactive, highly specific, and truly ready for the complex challenges we face today.
Why Everyone Is Talking About Zero Trust
So, why has "Zero Trust" popped up in seemingly every IT and business conversation? It’s not just the latest industry buzzword. The shift is a direct, necessary reaction to real-world problems that older security models are failing to solve. The fundamental ways we work have changed, and our security has to catch up.
Think about the traditional security perimeter—that digital "castle and moat." It was built to protect everything inside the office walls. But that wall has effectively crumbled. Today, people work from home, coffee shops, and hotels. This move to hybrid work, combined with the explosion of cloud services, means your company's sensitive data is being accessed from everywhere, punching huge holes in those old defenses.
The New Reality of Work and Threats
Today’s workplace is a dynamic mix of company laptops, personal smartphones (BYOD), and countless IoT devices, all connecting to your network. This is the daily reality in fast-paced Retail environments, sprawling Education campuses, and agile Corporate offices. Every single one of these devices is a potential doorway for an attack.
Zero Trust tackles this reality head-on by operating on a simple but powerful assumption: no user or device is trustworthy by default. It shifts security away from a static, location-based defense to a dynamic, identity-focused model that protects your users and data, no matter where they are.
This approach is so critical because cyberattacks have become incredibly sophisticated. Attackers know that if they can just get past the initial firewall, they often have free reign inside a traditional network. This is exactly where old-school systems fall short and where Zero Trust shines, because it never stops asking questions and validating every single request. To understand how even foundational security tools have had to evolve, check out our guide on what is a stateful firewall.
A Market Driven by Necessity
The huge momentum behind Zero Trust isn't just talk; it's backed by serious market growth and investment. In 2024, the global Zero Trust security market was valued at an estimated USD 36.96 billion. It's projected to skyrocket to USD 92.42 billion by 2030, a surge fueled by the constant threat of cyberattacks and the practical demands of a remote-first world.
This financial data proves that business leaders aren't just discussing Zero Trust—they are actively putting their money into it. For a growing number of organizations, adopting this framework is no longer optional. It's the most practical and effective strategy for securing a modern, distributed workforce and protecting their most valuable digital assets.
Putting Zero Trust Into Practice: Real-World Scenarios
It’s one thing to talk about the theory of zero trust, but how does it actually look in the real world? Let's move from concepts to concrete examples and see how these principles apply in everyday places like shops, schools, and offices. This is where the rubber meets the road.
Think about how crowded modern Wi-Fi networks are. In any given building, you’ll find company laptops, employees’ personal phones, and guest devices all vying for a connection. A zero trust approach, especially when powered by solutions from a provider like Cisco Meraki, makes sure every single connection is handled securely and with the right level of access.
Smart Authentication for Different Users
Picture a large Retail store. The store manager needs full access to sales data and employee scheduling software on her laptop. At the same time, a cashier only needs to use the inventory app on a store-owned tablet. Meanwhile, a customer just wants to connect to the free guest Wi–Fi.
In a classic network model, managing these different access levels would be a real headache and a security risk. With zero trust, it’s a much cleaner process. Every user and device is treated as a separate, unverified entity that has to prove its identity before it can go anywhere.
This is managed using different Authentication Solutions tailored to the user:
- For Guests: The best front door is a Captive Portal. It intercepts every guest device, requiring users to agree to terms or provide basic details before they can get online. This simple check is a fundamental first step in zero trust. You can learn more about how to use a Captive Portal for Wi-Fi to establish that initial verification.
- For Staff and Company Devices: In Corporate or Education environments, you need something stronger for employees and students. This is where IPSK (Identity Pre-Shared Key), sometimes called EasyPSK, really shines. Instead of a single Wi-Fi password for the entire organization, each person or device gets a unique key.
By tying network access directly to a specific user with their own key, you gain incredible control. If a device is stolen or an employee leaves the company, you just revoke that one key. Nobody else is affected.
This fine-grained control is zero trust in a nutshell. It lets you enforce the principle of least privilege with pinpoint accuracy, dramatically improving security, especially in a BYOD (Bring Your Own Device) setting.
The Power of Visibility and Control
A huge part of zero trust is knowing exactly who and what is on your network at all times. Modern security systems don't just grant access once; they watch it continuously.
This is what that looks like in practice. The Cisco Meraki dashboard gives a clear, live view of all connected devices, their assigned policies, and their data usage.
This level of visibility is invaluable. It empowers administrators to spot strange behavior, ensure security policies are working as intended, and respond to threats quickly. It’s how the abstract concept of "always verify" becomes a manageable, real-time security practice.
Navigating Your Zero Trust Journey
Making the move to a zero trust security model is a big deal, but it’s best to think of it as a continuous journey, not a one-and-done project. This shift in mindset brings some powerful advantages to any organization, whether you're running a busy Retail store, a sprawling Education campus, or a modern Corporate office filled with personal devices (BYOD).
One of the biggest wins is a massive improvement in protection against data breaches. When you're constantly verifying every user and every device, you're shrinking the potential attack surface. Even if an attacker manages to compromise a single account, the principle of least privilege stops them in their tracks, preventing them from moving freely through your network. The threat is contained instantly.
Another huge benefit is finally getting complete visibility into what’s happening on your network. With the right tools, like those from Cisco Meraki, administrators can see exactly who is accessing what, from where, and on which device. This level of clarity makes spotting unusual activity incredibly simple and takes the headache out of troubleshooting.
This kind of granular insight and control doesn’t just boost security. It also makes meeting compliance standards for regulations like HIPAA or PCI-DSS much more straightforward. The detailed logs from a zero trust system create a crystal-clear audit trail for every single access request.
Facing the Practical Hurdles
Of course, it's just as important to be realistic about the challenges. No major security upgrade comes without a few bumps in the road, and knowing what they are ahead of time is key to a smooth rollout. For a closer look at proactive security measures, you can read our guide on the best practices for network security.
Rolling out a zero trust framework isn't always easy. You might run into:
- Integration Headaches: Making new tools play nicely with older, legacy systems can be tricky.
- Resource Demands: This is a strategic investment in both time and money, and it needs to be planned for.
- Talent Gaps: There's a well-known shortage of cybersecurity experts, which can slow things down.
- Performance Worries: Stricter access controls could slow things down if not designed carefully.
You can find a deep dive into these implementation hurdles and market trends in this detailed industry report.
A Phased and Smart Approach
Don't let those challenges scare you off. They just prove the need for a thoughtful, step-by-step approach. You absolutely do not have to flip a switch and change your entire network overnight.
Start where it matters most. For many, securing Wi-Fi access is the perfect first step. Putting strong Authentication Solutions in place—like a Captive Portal for guests or IPSK/EasyPSK for employees—gives you an immediate and noticeable security boost. From that solid foundation, you can gradually extend zero trust principles to other parts of your network.
By balancing the incredible benefits with a practical view of the challenges, you can create a realistic roadmap. This allows you to get ahead of potential issues, make smarter investments, and ensure your journey to a more secure network is a successful one.
How Different Industries Are Putting Zero Trust into Practice
Zero trust isn't some rigid, one-size-fits-all blueprint reserved for massive tech corporations. Think of it more as a flexible security philosophy that different industries are shaping to solve their own unique, real-world problems. From bustling Retail stores to sprawling Education campuses and modern Corporate offices, that core mantra of "never trust, always verify" is showing up in some fascinating ways.
It’s probably no surprise that the industries handling our most sensitive information are leading the charge. Sectors like financial services and healthcare are constantly navigating a maze of strict regulations, which makes the verifiable, explicit nature of zero trust a natural fit for their compliance and security goals.
Leading the Charge in Regulated Fields
When you look at who's adopting zero trust, you can almost see a direct line to how sensitive their data is and how heavy their regulatory burden is. For example, the financial services sector is way out in front with a 91% adoption rate. This is largely because they have to meet stringent standards like PCI-DSS to protect financial data.
Healthcare is right on its heels, with an 85% adoption rate as organizations work tirelessly to safeguard patient information under HIPAA. You can find more details in these zero trust adoption statistics and trends. The takeaway is clear: where the data is most critical, zero trust is no longer a "nice-to-have"—it's an essential part of the security strategy.
Zero Trust in Everyday Environments: Education, Retail & Corporate BYOD
Beyond those high-stakes, regulated fields, the principles of zero trust are proving just as valuable in places we visit every day. It's particularly useful in environments that have to manage a ton of different users and devices connecting to Wi-Fi, especially with BYOD (Bring Your Own Device) policies in place.
-
Education: Picture a busy university campus. A zero trust approach ensures that a student’s personal laptop, a professor’s university-issued tablet, and a visiting parent's smartphone can all connect to the campus Wi-Fi without creating a security nightmare. By using Authentication Solutions like a Captive Portal for temporary guests and IPSK (or EasyPSK) for students and staff, the network can intelligently assign specific access rights. This means a student simply can't wander into the faculty records, and a guest's device is kept completely isolated from the main campus network.
-
Retail: In a modern store, zero trust secures every single connection, from the front door to the stockroom. A customer who logs into the free guest Wi-Fi is kept completely separate from the critical point-of-sale (POS) systems. An employee’s barcode scanner is granted access only to the inventory management system, never to sensitive customer payment data. This kind of granular control, made possible by solutions from providers like Cisco Meraki, turns abstract security policies into practical, real-world rules that keep the business running and protect everyone's information.
-
Corporate BYOD: In a busy office where employees use their own devices, Zero Trust is a lifesaver. Using Authentication Solutions like IPSK ensures that a personal phone can access email but can't touch confidential R&D files. This segmentation, managed centrally on hardware like Cisco Meraki, makes BYOD both productive and secure.
A Few Common Questions About Zero Trust
Now that we've walked through what zero trust security is and how it works, let's clear up some of the questions we hear most often. Getting these details straight will help you feel more confident as you think about what this modern security approach could mean for your organization.
Is Zero Trust a Product I Can Buy or a Broader Strategy?
This is a great question. Zero trust is a security strategy, not a single product you can just pull off the shelf. Think of it as a fundamental shift in your security mindset, built on the simple but powerful idea: "never trust, always verify."
To put this strategy into action, you'll use a combination of different technologies that all work together. This often includes things like multi-factor authentication, identity management, and network segmentation tools from providers like Cisco Meraki. These solutions are the building blocks you use to enforce continuous verification and give users only the minimum access they need to do their jobs.
At its heart, zero trust is a philosophy. The technology is simply the toolset you use to bring that philosophy to life, protecting data first and treating every access request with a healthy dose of suspicion.
Can I Start Using Zero Trust With My Existing Network?
Yes, absolutely! You definitely don't need to rip out your entire network and start from scratch. In fact, taking a phased approach is almost always the best way to begin your zero trust journey.
You can start by taking advantage of the features already built into your modern infrastructure. For example, the current generation of Cisco Meraki Wi-Fi access points comes ready to support the advanced authentication policies that are the bedrock of a zero trust model.
The journey often starts by tightening up identity verification. This could be something as straightforward as setting up a Captive Portal for your guest Wi-Fi, or it could be more advanced, like using IPSK or EasyPSK for employee devices. From that starting point, you can gradually layer on more controls, improving your security posture piece by piece instead of trying a disruptive, all-at-once overhaul.
How Does Zero Trust Help Secure BYOD Environments?
Zero trust is practically tailor-made for managing the chaos of BYOD (Bring Your Own Device) environments, which are everywhere in sectors like Education, Retail, and Corporate offices. The model works so well because it automatically assumes every single device is a potential threat—even if it's already sitting on your internal Wi-Fi network.
By using powerful Authentication Solutions, you can confirm the identity of both the user and their device before letting them connect to anything. This lets you build incredibly specific rules. For instance, a student's personal laptop in a dorm can get to the internet but is completely walled off from the sensitive faculty network. It's this kind of fine-grained control that makes it possible to secure a diverse and unpredictable fleet of personal devices.
Ready to bring a zero trust approach to your Wi-Fi network? Splash Access makes it simple. We offer instantly deployable captive portals and advanced authentication solutions like IPSK that work perfectly with your existing Cisco Meraki hardware. Explore our solutions to secure your network and unlock valuable insights today.