Hey there! Ever walked into a school, a busy retail store, or a bustling corporate office and wondered how their Wi-Fi network stays up and running without a hitch, especially with so many people connecting? The unsung hero behind that stability is a technology called the Spanning Tree Protocol, or STP. It's the essential traffic cop for your wired network, preventing the kinds of digital traffic jams that can bring everything to a halt.
Your Network's Silent Guardian

Think about the physical switches that make up your network. To make the network reliable, you'd naturally want to connect them with multiple cables, creating redundant paths. If one link fails, traffic can just take another route. Simple, right?
The problem is, without a system to manage those extra paths, you create a recipe for disaster. It’s like a city road system with circular routes but no traffic lights—cars would just drive in circles forever, causing total gridlock. STP is that intelligent traffic controller, making sure data has a clear, loop-free path to its destination.
This protocol is the bedrock that makes our modern Wi-Fi experiences possible. A stable wired backbone is non-negotiable; without it, the advanced features we now take for granted just won't work. This is especially true in environments like schools, stores, and offices in the Education, Retail, and BYOD Corporate sectors that rely heavily on everyone bringing their own devices.
The Problem STP Solves
So what exactly happens when that network "gridlock" I mentioned occurs? You get something called a broadcast storm. A single piece of data gets trapped in a physical loop, bouncing between switches over and over again. It multiplies exponentially, hogging every bit of available bandwidth until the network grinds to a halt. The result is a complete network meltdown.
This is the exact problem STP was designed to prevent. It intelligently creates a single, logical, loop-free path through the network. Radia Perlman invented the original Spanning Tree Protocol back in 1985 while at Digital Equipment Corporation (DEC). Her brilliant solution addressed the critical challenge of broadcast storms by selectively blocking redundant links to ensure there was only one active path at any given time. If you're curious, you can discover more insights about this foundational protocol's history and impact.
Why It Matters for Modern Wi-Fi
You might be thinking, "This all sounds like a wired network issue. How does it affect my Wi-Fi?" The answer is: in a huge way. Your Wi-Fi access points, including powerful devices from vendors like Cisco and Cisco Meraki, are plugged directly into that wired infrastructure.
A broadcast storm on the wired side will absolutely cripple your wireless network. It can stop devices from getting IP addresses and block them from reaching authentication servers, effectively shutting down your Wi-Fi.
This has a direct and frustrating impact on the services your users depend on every day:
- Captive Portals: In a store or a school library, the splash page a user needs to sign in through might never load because the network is choked.
- Authentication Solutions: Secure sign-on methods like IPSK and EasyPSK need to talk to a central server. A broadcast storm severs that connection, leaving users unable to get online at all.
Ultimately, understanding what Spanning Tree Protocol is and making sure it's configured correctly is the first and most important step in building a reliable, high-performing network that can handle the demands of any modern environment.
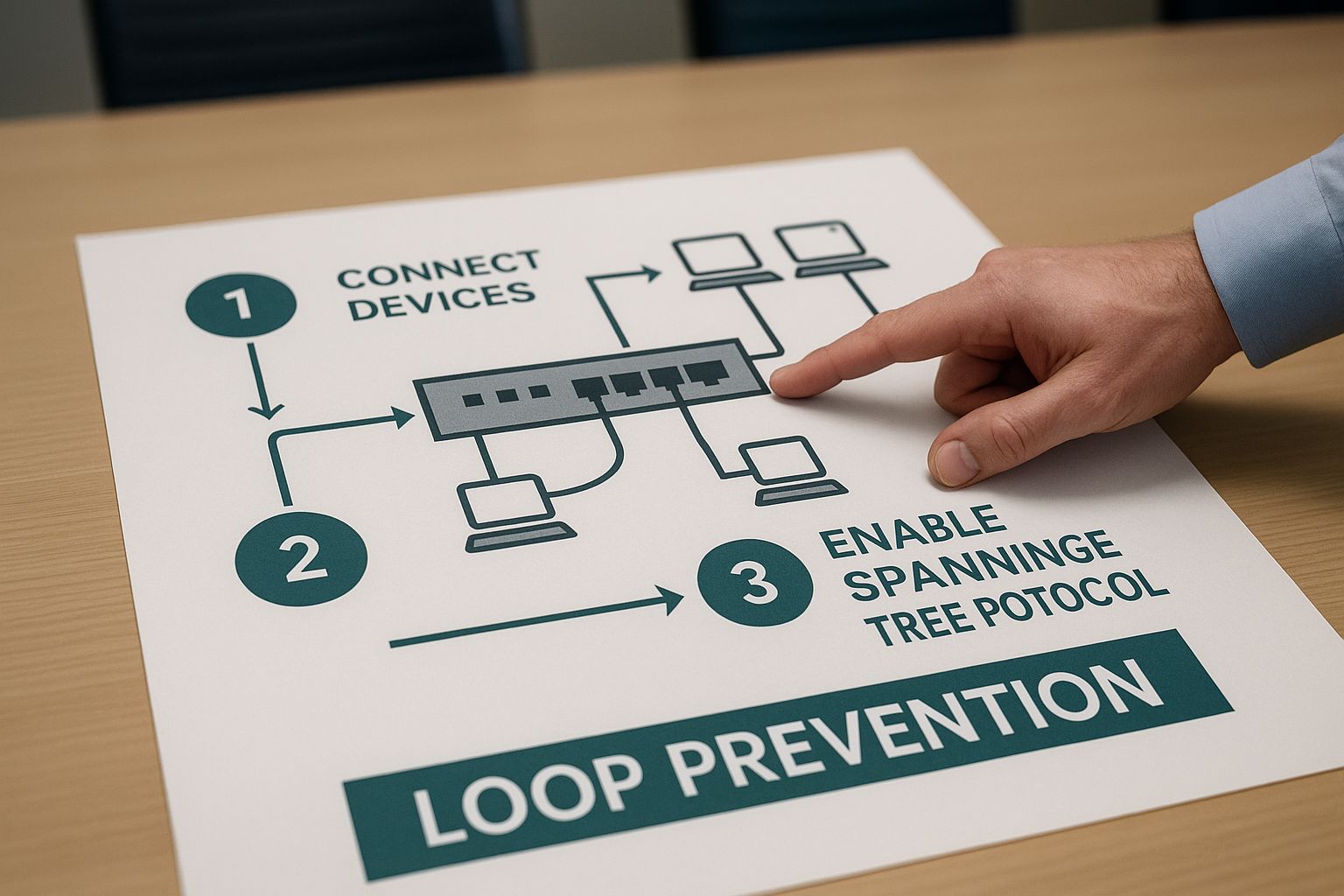
How STP Creates a Loop-Free Network
So, how does the Spanning Tree Protocol actually prevent a network meltdown? It's all about creating a single, stable, logical path for data, even when you have multiple physical cables connecting your switches. Think of it like this: you've built redundant roads between cities for reliability, but STP establishes a clear set of "main highways" and puts "road closed" signs on the alternate routes to prevent traffic from circling endlessly.
This all happens through a fascinating, automated process that’s a bit like an election.
The Election of a Leader: The Root Bridge
First things first, the switches need a leader. STP handles this by electing one switch to be the Root Bridge. You can think of it as the network's command center or central reference point.
Every switch on the network starts out by sending special messages called Bridge Protocol Data Units (BPDUs). These BPDUs are like campaign flyers, containing key information like the switch's unique ID. The switch with the most attractive (lowest) ID wins the election and is crowned the Root Bridge.
Finding the Best Path Home
Once the leader is chosen, every other switch in the network has a single mission: find the absolute best, most direct path back to the Root Bridge. This single, most efficient connection on each switch is designated as its Root Port. It's the on-ramp to the main highway leading back to the network's core.
This diagram shows how a network engineer might visualize this process, mapping out the active and blocked paths to ensure a clean, stable topology.
As you can see, STP's primary job is to intelligently manage these connections, creating a single, reliable path that prevents the broadcast storms that can bring a network to its knees.
Putting Redundant Links on Standby
Here's where the real magic happens. What about all those other connections—the redundant links you installed for backup? STP doesn't just ignore them; it puts them to work by placing them on standby.
Any port that isn't a Root Port or a Designated Port (a primary port on a network segment) is put into a blocking state. A blocked port is still alive and listening but doesn't forward any data. It’s waiting in the wings. If the main route ever fails—say, a cable gets unplugged—STP immediately springs into action, recalculates the best path, and unblocks the backup port to restore connectivity, often in just a few seconds.
This constant process of electing a leader, finding the best paths, and blocking redundant ones is what creates a loop-free "tree" structure—and that’s exactly where the Spanning Tree Protocol gets its name.
The table below breaks down these core concepts, showing the role each port plays and the states it moves through.
Understanding STP Port Roles and States
| Concept | Role or State | What It Means for Your Network |
|---|---|---|
| Leadership | Root Bridge | The central switch that acts as the reference point for the entire network. All other switches calculate their best path back to this bridge. |
| Best Path | Root Port | The single port on a non-root switch that has the most efficient path back to the Root Bridge. This is the primary "on-ramp." |
| Segment Control | Designated Port | The port on a network segment (link between switches) that is chosen to forward traffic for that segment. Only one designated port is active per segment. |
| Backup Path | Blocked Port | A port that is intentionally disabled from forwarding traffic to prevent a loop. It remains on standby, ready to become active if a primary path fails. |
| Initial State | Listening | The port is processing BPDUs to determine the network topology but is not yet forwarding user data. |
| Preparation State | Learning | The port is still not forwarding user data, but it is learning MAC addresses to build its forwarding table. |
| Active State | Forwarding | The port is fully operational, sending and receiving all user data traffic. |
Ultimately, this intelligent system of roles and states is what allows STP to build a reliable, loop-free network foundation.
Why This Matters in the Real World
This might sound a bit technical, but its impact is huge. In a school, a broadcast storm during online testing could be a disaster. For a retail store, a network loop means the point-of-sale systems crash and guest Wi-Fi stops working. And in modern corporate environments where employees bring their own devices (BYOD), a stable network isn't a luxury; it's a basic requirement.
The real beauty of STP is that it operates silently in the background, providing the robust wired backbone needed for today's demanding wireless services. When a student in a dorm or an employee in an office connects to Wi-Fi, they just expect it to work. STP is a huge part of why it does.
This underlying stability is also what allows advanced authentication to work smoothly. Think about a user trying to connect with IPSK or EasyPSK. These methods require constant, clear communication between the access point and a central server. A network loop kills that conversation, leaving the user stuck. The same goes for Captive Portals—if the network is flapping, the login page will never load.
Ensuring secure access also means choosing the right security framework. You can read more about this in our deep dive on WPA2 Personal vs. Enterprise. By guaranteeing a clean, loop-free path, STP ensures that all these critical services, often managed through a Cisco Meraki dashboard, have the reliable foundation they need to run without a hitch.
The Evolution from STP to Modern RSTP
While the original Spanning Tree Protocol was a brilliant solution in its day, it had one major flaw that just doesn't fly in our modern world: it was slow. Really slow. If a network path failed, the classic STP could take up to 50 seconds to figure out a new route and get traffic flowing again. In today’s always-on environments, 50 seconds of downtime is an eternity.
Just think about it. Imagine a busy retail store where the payment system freezes for nearly a minute, or a classroom in the middle of a critical online exam where every student loses their connection. Those scenarios are more than just inconvenient; they're completely unacceptable. This urgent need for speed is what drove the development of a much faster, more intelligent successor.
Introducing Rapid Spanning Tree Protocol (RSTP)
Enter the Rapid Spanning Tree Protocol (RSTP), or IEEE 802.1w. It does exactly what its name implies: it works fast. Instead of the painfully slow listening and learning process of the original STP, RSTP streamlines everything. The result? Network recovery time plummets from nearly a minute down to just a few seconds, or even milliseconds in some configurations.
This massive performance jump is why RSTP is now the default standard on virtually all modern networking equipment, from switches by industry giants like Cisco to the powerful cloud-managed gear from Cisco Meraki. For any BYOD corporate network, school, or retail store, this near-instant recovery isn't just a nice feature—it's absolutely essential for keeping the lights on.
At its core, RSTP is so effective because it proactively identifies alternate paths and can switch to them almost instantly. It transforms Spanning Tree from a slow, methodical safety net into a nimble, high-speed recovery mechanism.
The Need for Speed in Modern Networks
So, why is this speed so critical? Because every second of downtime has a real, tangible cost. In any business that depends on constant connectivity, a slow network recovery can bring operations to a grinding halt.
- Authentication Solutions: A slow failover can cause authentication requests to time out. This means users trying to log in with secure methods like IPSK or EasyPSK will be rejected, locking them out of the network.
- Captive Portals: In a hotel or cafe, if a guest tries to connect while the network is re-calculating its paths, the captive portal or splash page simply won't load. That leads to frustrated users and missed opportunities for engagement.
The switch to RSTP was a monumental step forward for network reliability. While traditional STP took its time, RSTP slashed convergence times, making networks far more resilient. This performance boost is managed far more easily on modern platforms. For instance, Cisco Meraki enables RSTP by default to ensure its customers have the most stable network possible, right out of the box.
This dashboard-driven approach lets you see at a glance that your network is protected by the faster protocol, which is a must-have for any business. The type of hardware you use also affects how these protocols are managed, which is why understanding the difference between managed vs unmanaged switches is so important.
A Glimpse at MSTP for Complex Networks
For the largest and most complex enterprise environments, there's another flavor of Spanning Tree: Multiple Spanning Tree Protocol (MSTP). While RSTP is all about fast recovery, MSTP introduces an extra layer of efficiency by enabling load balancing across different Virtual LANs (VLANs).
Essentially, MSTP allows you to draw different spanning tree "maps" for different groups of traffic. This means a link that’s blocked for one VLAN can be actively used by another, which is a much smarter way to use all your available bandwidth. While RSTP is more than enough for most networks, MSTP is a powerful tool when you're operating at a massive scale.
Why a Stable Wired Network Matters for Wi-Fi
You might be asking yourself, "Why are we so focused on a wired protocol when Wi-Fi runs the world?" That's a fair question, and the answer cuts right to the core of how modern networks are actually built. A stable wired backbone isn't just a nice-to-have for your wireless network; it's the absolute foundation it stands on.
Think of it this way: your Wi-Fi access points (APs) are like high-performance race cars. They can be incredibly fast and packed with the latest tech. But if the racetrack they're on is riddled with potholes and debris, they're not going to win any races. The Spanning Tree Protocol is what keeps that racetrack—your wired network—smooth, clear, and ready for high-speed performance.
Without a protocol like the fast Rapid Spanning Tree Protocol (RSTP) we've discussed, your wired network is just one accidental cable connection away from a loop. When a loop happens, it unleashes a broadcast storm, and that's the moment your Wi-Fi experience grinds to a halt.
The Ripple Effect of a Broadcast Storm
A broadcast storm is pure network chaos. It’s a digital tsunami of junk traffic that floods every single connection, completely overwhelming your switches and, more importantly, your Wi-Fi access points. Even the most powerful Cisco Meraki APs will be brought to their knees.
This storm of digital noise essentially severs the connection between your APs and the rest of the network. As a result, critical services that depend on that connection start to fail. Your users don't know what a broadcast storm is; they just know their Wi-Fi is broken, and the help desk tickets start rolling in.
When Authentication Solutions Fail
Modern networks, especially in demanding environments like Education, Retail, and BYOD Corporate offices, rely on sophisticated security and easy onboarding. This is where advanced authentication solutions come in, but they are extremely sensitive to the kind of instability a network loop creates.
Think about these everyday situations:
- Identity-Based Pre-Shared Keys (IPSK): This popular method, often called EasyPSK, gives each user or device a unique key. When a student in their dorm or an employee at their desk tries to connect, their device has to talk to an authentication server to get the green light. A broadcast storm cuts that line of communication, causing the authentication to time out and fail. The user is locked out, even with the right password.
- 802.1X Authentication: In high-security environments, 802.1X offers powerful, certificate-based security. Just like IPSK, it needs constant, clear communication with a central server to work. A network loop makes that impossible, effectively locking everyone out of the Wi-Fi.
When STP fails, your entire security posture is compromised. It doesn't matter how strong your Wi-Fi encryption is if users can't even complete the first step of getting onto the network.
This stability is also a prerequisite for adopting the latest security standards. To understand how wireless security has evolved, you can learn more about what WPA3 is and why it's the new benchmark. A healthy network is essential to deploy these stronger protections effectively.
The Captive Portal Problem
The damage is just as bad for guest networks that rely on Captive Portals. Picture a customer walking into a Retail shop or a visitor arriving at a corporate office. The first thing they do is try to join the guest Wi-Fi, expecting a branded splash page where they can log in or accept the terms.
If a network loop is raging behind the scenes, that Captive Portal will never load. The user's device gets stuck in its own frustrating loop: trying to connect, failing to see the login page, and eventually timing out. For a retail business, that's a missed chance to engage a customer. For a corporation, it's a poor first impression and a headache for the front desk.
The reliability of these portals, often managed right from a Cisco Meraki dashboard, is directly tied to the health of the wired network they operate on. By stopping loops before they start, STP ensures these vital, user-facing services are always online. The image below of a user seamlessly connecting is exactly the experience that a stable, STP-protected network delivers.

Ultimately, knowing what is the spanning tree protocol is about more than just technical loop prevention. It’s about understanding that a resilient wired infrastructure, governed by a smart protocol like RSTP, is the non-negotiable price of admission for a reliable, secure, and user-friendly wireless experience.
Practical STP Configuration and Troubleshooting
Let's be real—theory is one thing, but getting the Spanning Tree Protocol to work for you in the real world is what really counts. When configured correctly, STP isn't just a quiet background process; it becomes a powerful tool that makes your entire network more stable and reliable.
By being proactive, you can ensure your network—whether it’s in a bustling Retail store, a sprawling Education campus, or a demanding BYOD Corporate office—runs exactly as it should. The last thing you want is to let your switches decide the network hierarchy on their own. Leaving the Root Bridge election to chance often means a less capable, poorly-placed switch takes on this vital role, creating sluggish and inefficient traffic paths.
Taking Control of Your Network Topology
The single most important thing you can do is manually select your Root Bridge. You always want your most powerful, centrally located switch to be in charge—typically a core or aggregation switch from a vendor like Cisco. By setting its STP priority to the lowest value, you guarantee it will win the election every time.
This one simple action forces all network traffic to flow toward the heart of your network in the most direct way possible, which cuts down on latency and boosts overall performance. In a Cisco Meraki environment, you can manage this right from their cloud dashboard, giving you a crystal-clear view and direct control over your network's logical design.
Next, you need to secure your network's edges. Think about all those ports facing your users—in classrooms, on the sales floor, or in open office spaces. These are the weak spots where someone could plug in a small, unmanaged switch and accidentally create a broadcast storm.
This is where a feature like BPDU Guard is your best friend. When you enable it on a port, it instantly shuts the port down if it receives an STP BPDU packet. Since those packets should only come from other managed switches, this feature stops a rogue device from taking down your network cold.
Recognizing and Resolving STP Issues
Even with a perfect setup, problems can pop up. Knowing the warning signs is half the battle. If you start seeing slow or spotty connectivity, especially across entire segments of your network, STP could be the cause. A network that feels "flaky," with devices dropping off and reconnecting at random, is often a symptom of rapid, unwanted topology changes.
When trouble hits, your first move should be to check your network management platform. The Cisco Meraki dashboard, for instance, has fantastic tools for this. You can see the STP status for every switch and port, quickly identifying which switch is the Root Bridge and which ports are currently in a blocking state.
Here are a few initial troubleshooting steps:
- Check for an Unexpected Root Bridge: Is a small edge switch somehow acting as the Root? If it is, you'll need to adjust its priority so a core switch can rightfully take over.
- Look for Flapping Ports: Are ports bouncing between forwarding and blocking states? This often points to a bad cable, a faulty SFP, or some other physical layer problem.
- Review Event Logs: Network dashboards keep detailed logs that can show you exactly when a topology change happened, helping you connect it to other events.
As you get comfortable with STP, it helps to understand the broader context of how to troubleshoot common business network issues. A wider perspective will make you a much more effective network administrator.
Ultimately, a stable STP configuration is the foundation for everything else you build on top of it. Without it, Authentication Solutions like IPSK and EasyPSK can fail, and the Captive Portals for your guest network might not even load. If you’re trying to set up a great guest experience, our guide on how to set up guest Wi-Fi can show you the way—but just remember, it all starts with a rock-solid wired network. When you master STP, you gain the confidence to build a network that just works.
Building a Foundation for Network Success
So, we've unpacked the Spanning Tree Protocol, and it’s clear this is far more than just another technical acronym. It’s about laying the groundwork for a network you can truly count on. Think of it as the unsung hero working behind the scenes, keeping your network stable and responsive, which is absolutely essential for modern Wi-Fi services.
At its core, STP is your first and best line of defense against the kind of network loops that can bring everything to a grinding halt. In today's fast-paced environments, you can't afford downtime. That’s why modern versions like RSTP—which comes standard on equipment from manufacturers like Cisco and Cisco Meraki—are so crucial. They provide the rapid recovery needed in demanding sectors like Retail, Education, and BYOD Corporate environments. Getting this configuration right is what allows advanced authentication solutions to secure your users without a hitch.
A resilient wired backbone is the non-negotiable foundation for every wireless service. Without it, even the best Wi-Fi setup will fail under pressure.
When your wired network is solid, everything else just works better. Captive Portals load instantly. Secure logins using IPSK or EasyPSK are seamless. By setting up STP correctly, you're not just preventing problems; you're building a resilient, high-performing network that’s ready for anything you throw at it. This proactive mindset is a cornerstone of strong network security for small businesses and large enterprises alike.
With this knowledge, you’re now equipped to make sure your network’s foundation is solid, stable, and ready to deliver the flawless user experience everyone has come to expect.
Your Spanning Tree Questions, Answered
Getting into the weeds with network protocols always sparks a few questions. Let's tackle some of the most common things network admins and engineers ask about the Spanning Tree Protocol and how it really works in the wild.
Can I Just Turn STP Off If My Network Is Small?
I get why you'd ask this. In a tidy little network, it can feel like overkill. But here's the thing: you should almost never disable STP. The most common cause of a full-blown network outage isn't some complex attack; it's an accidental loop.
It happens all the time. Someone innocently plugs both ends of a cable into two different wall jacks, or they bring in a cheap unmanaged switch from home to get more ports. Without STP, that simple mistake creates a broadcast storm that can bring your entire network to its knees. Think of STP as your essential safety net—especially in dynamic places like Education campuses, Retail shops, or any office with a BYOD policy. The risk is just too high to go without it.
What’s the Real Difference Between Standard STP and Cisco’s PVST+?
The original STP standard (802.1D) was a bit of a blunt instrument. It ran a single Spanning Tree instance across the whole network, regardless of how many VLANs you had. If a link had to be blocked to prevent a loop, it was blocked for all traffic.
To get around this, Cisco introduced its Per-VLAN Spanning Tree Plus (PVST+). It was a game-changer because it runs a completely separate STP instance for each individual VLAN. This gives you much more granular control and even lets you do some basic load balancing. For example, a link could be blocked for your staff VLAN but remain active and forwarding for your guest VLAN. Modern switches, including those from Cisco Meraki, have taken this a step further by using Rapid STP (RSTP) on a per-VLAN basis, giving you the best of both worlds: fast convergence and precise control.
A stable, loop-free network managed by STP is the essential foundation for any reliable Wi-Fi authentication solution to function correctly. This is why it’s a non-negotiable part of modern network design.
How Does STP Actually Impact Wi-Fi Authentication?
At first glance, the link isn't obvious, but it's critical. STP is what guarantees the stability of the wired backbone that all your wireless Access Points are plugged into. If a loop happens, the resulting broadcast storm doesn't just slow things down—it creates total chaos that can overwhelm your APs and switches.
When that happens, wireless clients can't get an IP address from your DHCP server. They can't reach your authentication solutions, whether you're using RADIUS for 802.1X or a pre-shared key system like IPSK. The Captive Portal for your guest network will time out and fail to load. In short, your slick EasyPSK or guest login process breaks because the AP is effectively cut off from the servers it needs to talk to.
A healthy, loop-free wired network isn't just a "nice to have"; it's the absolute bedrock on which reliable Wi-Fi authentication is built.

At Splash Access, we focus on building powerful and engaging guest Wi-Fi experiences that rely on the solid foundation of a well-configured network. Our platform integrates perfectly with Cisco Meraki, letting you deploy secure, branded captive portals and innovative authentication methods like IPSK.
Learn how Splash Access can transform your guest Wi-Fi today!