Ever feel like managing your business's tech is a huge headache? You're not alone! That's where Cisco Meraki comes in. Think of it not just as a box of networking gear, but as a super-smart, cloud-managed IT solution designed to make powerful technology ridiculously simple. The big idea is to take all the complicated network controls off-site and put them into one friendly web dashboard. This means everything—from your Wi-Fi access points to your security cameras—is managed from a single place. How cool is that?
Understanding The Cisco Meraki Ecosystem
At its heart, Cisco Meraki is all about stripping the complexity out of enterprise-grade networking. Let's make it relatable: instead of juggling a half-dozen different remote controls for your TV, soundbar, and streaming box, imagine having one universal remote that does it all. That's the Meraki dashboard—the central nervous system for every piece of Meraki gear on your network.
This friendly approach has been a total game-changer for places like schools in the Education sector, busy Retail stores, and Corporate offices that need to manage secure Wi-Fi for tons of different people and devices. It's especially handy in the modern world of BYOD (Bring Your Own Device) policies.
This cloud-first vision actually started as a research project at MIT. Founded back in 2006, the company’s goal was to simplify networking through the cloud—a pretty revolutionary idea at the time. Tech giant Cisco saw the genius in it and acquired Meraki for a cool $1.2 billion in 2012, bringing that streamlined management style to its global customer base.
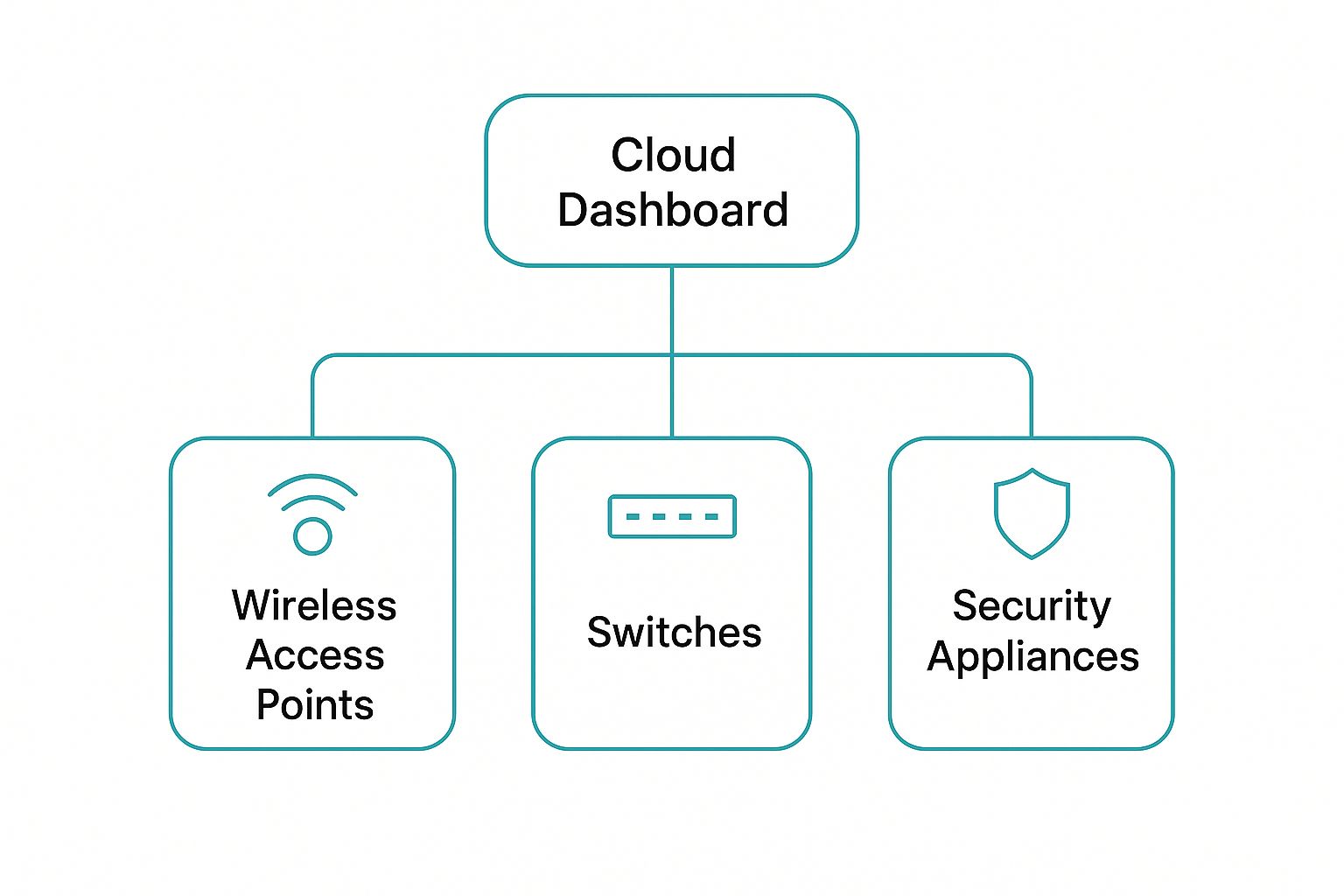
The diagram below gives you a great visual of how all the different Cisco Meraki products tie back into that central cloud dashboard.
As you can see, whether it's wireless APs, switches, or security appliances, the dashboard is your single pane of glass for managing the entire network.
The Cisco Meraki Cloud Ecosystem at a Glance
The Meraki portfolio is built around a few core hardware categories that all play nicely together. This table breaks down the main players in the ecosystem.
| Product Category | Primary Function | Core Benefit |
|---|---|---|
| Wireless (MR Series) | Provides high-performance Wi-Fi access | Easy deployment and management of wireless networks for guests and staff. |
| Switching (MS Series) | Connects wired devices to the network | Centralized port management and visibility across all wired connections. |
| Security/SD-WAN (MX Series) | Secures the network perimeter and manages connections | All-in-one firewall, VPN, and threat protection managed from the cloud. |
| Endpoint Management (Systems Manager) | Manages and secures user devices (laptops, phones) | Pushes security policies and software to all connected endpoints. |
| Smart Cameras (MV Series) | Provides cloud-managed video surveillance | Simplifies security camera deployment and provides intelligent analytics. |
Each of these components plays a crucial role, but their real power comes from how seamlessly they integrate and operate from that one central dashboard.
Key Components of Meraki
So, what are the building blocks of this platform? Meraki’s hardware is designed for simplicity and power, with a few key product lines forming the foundation.
-
Wireless Access Points (MR series): These are the workhorses that deliver fast, reliable Wi-Fi. They’re perfect for everything from deploying a robust guest network in a coffee shop to supporting hundreds of student laptops on a university campus.
-
Security Appliances (MX series): Think of these as the digital gatekeepers for your network. They provide the essential firewall, VPN, and threat management features you need to keep your data safe from intruders.
-
Switches (MS series): These form the backbone of your wired network. MS switches connect all your devices with high-speed performance and, like everything else, are managed entirely from the cloud dashboard.
These components are especially critical when you're setting up modern Authentication Solutions. For example, you can use Meraki hardware to create secure, branded login pages for your guest Wi-Fi. If you want to dive deeper into that, our guide on what a captive portal is explains how this technology works perfectly with the Cisco Meraki stack. The system also handles advanced security protocols like IPSK and EasyPSK, which give each user a unique key for an extra layer of protection.
Exploring the Meraki Cloud Dashboard
The real secret sauce of Cisco Meraki isn't just the sleek hardware—it's the cloud dashboard. This is where the magic happens.
Think about it. You need to configure the Wi-Fi at a new Retail store, troubleshoot a student's spotty connection in their dorm, or check security footage from a warehouse halfway across the country. Instead of juggling different systems or physically driving to the site, you can do it all from one clean, intuitive web page.
This is what we in the IT world call a "single pane of glass." It’s a huge departure from the old way of doing things, which usually meant wrestling with complex command-line interfaces. For any busy IT team, whether in Education, Retail, or a fast-moving Corporate office, this kind of centralized control is a total game-changer.
Simplifying Complex Network Management
Let's ground this in a real-world scenario. Imagine you're the IT manager for a Retail chain with 50 different stores. Your next project is to roll out a secure guest Wi-Fi network across every single location. Traditionally, this would be a nightmare project, potentially taking weeks of manual, on-site configurations.
With the Cisco Meraki dashboard, that entire process is condensed. You can create a single network template with all your required settings, including a branded Captive Portal for guests to log in, and then push that template out to all 50 stores with just a few clicks. That’s the kind of efficiency Meraki is built on.
Here’s a look at what you see when you log in—it’s all about presenting complex data in a way that’s easy to understand.
This dashboard gives you immediate, at-a-glance insights into your network's health and what users are doing, making troubleshooting faster and far more intuitive.
Powering Modern Authentication and BYOD
The dashboard is much more than a simple setup tool; it's also your command center for modern security and authentication solutions. In any Corporate environment with a BYOD (Bring Your Own Device) policy, making sure every personal phone, tablet, and laptop is secure is a massive challenge.
The Meraki dashboard makes deploying advanced security protocols surprisingly straightforward. It allows IT teams to move beyond a single, easily compromised password and implement much stronger authentication methods right from the web interface.
This is where features like IPSK (Identity Pre-Shared Key) or EasyPSK become incredibly valuable. These clever tools let you assign a unique password to every single user or device, which dramatically improves security without making things complicated for the end-user. And you can manage all of these keys from one central spot in the cloud.
For organizations wanting to take security and user convenience a step further, you can learn more about Passpoint secure Wi-Fi and how it can completely automate the login process for a seamless connection.
Ultimately, whether you're managing a handful of access points or a network spanning thousands of devices, the Cisco Meraki dashboard gives you the visibility and control to do it simply and securely.
Securing Connections with Meraki Wi-Fi
Great Wi-Fi is the lifeblood of just about any modern business or school, but just having a strong signal isn't the whole story. In places like busy Retail stores, crowded school campuses, or offices full of personal devices (BYOD), that connection has to be rock-solid and secure. This is where Cisco Meraki's wireless solutions really shine, mixing high-speed performance with security that’s surprisingly easy to manage.
Leading the charge are Meraki's Wi-Fi 6 access points, which are built specifically for the kinds of high-density spaces we see everywhere now. Picture a university lecture hall packed with students streaming video, or a retail floor where dozens of customer phones and point-of-sale systems are all fighting for airtime. Wi-Fi 6 technology makes sure everyone gets a fast, stable connection without the lag.
Wireless LAN has always been central to Meraki’s identity. The latest access points—like the popular MR36, MR46, and MR56 models—are all-in on the Wi-Fi 6 standard, delivering a noticeable boost in speed, efficiency, and security. As you’d expect from a leader in cloud-managed Wi-Fi, these devices are certified for top-tier performance. You can read more about these new Meraki access points and what they bring to the table.
Crafting the Perfect Welcome with Captive Portals
One of the most powerful and visible tools in Meraki’s security toolbox is the Captive Portal. You’ve definitely seen one of these before—it’s that branded login screen that pops up when you connect to the Wi-Fi at a hotel, coffee shop, or airport. It's your digital welcome mat!
For a Retail business, a Captive Portal is a golden opportunity. It’s the very first digital handshake a customer has with your brand inside the store. Instead of just asking for a password, you can greet them with a login page showing off your logo, a special promotion, or a prompt to follow you on social media.
In Education, schools use Captive Portals to get students and guests to agree to an acceptable use policy before they jump online. It’s a simple but effective step that makes sure everyone knows the rules, helping to create a much safer digital environment across campus.
Solving the BYOD Puzzle with Smart Authentication
The era of writing the Wi-Fi password on a whiteboard is thankfully over. In any modern Corporate or Education environment, "Bring Your Own Device" (BYOD) is the new normal, but it brings a huge security challenge. How do you manage hundreds of personal laptops, tablets, and phones without giving your IT team a massive headache?
This is where advanced authentication solutions make all the difference.
Think of it this way: instead of one master key for every door, you give each person a unique key that only works for them. That’s the core idea behind Identity Pre-Shared Key (IPSK), and it completely changes how we secure Wi-Fi networks.
Solutions like IPSK and EasyPSK get rid of the risk that comes with a shared password. When an employee leaves the company or a student graduates, you just revoke their individual "key," and nobody else is affected. This level of granular control is crucial for protecting sensitive information in a BYOD world. For IT admins, managing all these unique keys right from the Meraki dashboard is dead simple, turning a once-painful security task into a few clicks.
How Industries Use Cisco Meraki
Theory is one thing, but the real test of any tech is how it performs out in the wild. When you ask, "what is Cisco Meraki?" the best answer isn't a technical definition. It's found in the way it solves everyday problems for real organizations—from bustling school hallways to sleek corporate offices.
The platform's adaptability is a huge part of its success story. Think about this: by May 2017, Cisco Meraki was already powering over one million active networks across the globe. That ranges from tiny single-access-point setups to massive, sprawling enterprise deployments. That kind of scale tells you just how versatile this system really is.
Boosting Digital Learning in Education
The Education sector has been completely transformed by technology. These days, reliable Wi-Fi is just as critical as textbooks. Schools need a network that doesn't buckle when hundreds of students are all streaming videos, taking online tests, and collaborating on digital projects at the same time. Cisco Meraki's wireless access points deliver that kind of robust connectivity, keeping modern classrooms running smoothly.
But it’s not just about providing a connection. Meraki gives schools the tools to create a safe online space. From the dashboard, an IT admin can easily filter content, block inappropriate websites, and make sure students stay focused and protected. They often use Captive Portals to have students and guests agree to an acceptable use policy before getting online, which adds a simple but effective layer of accountability.
Enhancing the Retail Customer Experience
For the Retail industry, guest Wi-Fi has evolved from a simple courtesy into a powerful tool for engagement and business intelligence. When a shopper connects to your store's network, it's a golden opportunity to make a great first impression. With a Captive Portal, you can greet them with a branded login page that shows off special offers, highlights new arrivals, or invites them to join a loyalty program.
That initial login is more than just a gateway to the internet; it’s a data goldmine. Retailers can start to understand foot traffic patterns, how long people stay in certain areas, and how often they return. This information is invaluable for making smarter decisions about store layout and marketing campaigns. These strategies are all about building a better shopping environment, and you can dive deeper into how to improve customer experience in our dedicated guide.
Simplifying BYOD in the Corporate World
In any modern Corporate office, the "Bring Your Own Device" (BYOD) trend is a fact of life. But it also creates a massive security headache. How do you let employees connect their personal laptops, tablets, and phones to the company network without swinging the door wide open to security threats?
This is where Meraki really shines, thanks to its advanced authentication solutions. Forget relying on a single, shared password that can be easily compromised. Instead, companies can use features like IPSK (Identity Pre-Shared Key) and EasyPSK. These systems give a unique, individual key to each person or device, which dramatically strengthens security. If an employee leaves the company, their access can be instantly shut off without disrupting anyone else.
For a broader perspective on how different industries handle their digital infrastructure, you might find some useful insights in these general tech and cybersecurity strategies for businesses.
Turning Guest Wi-Fi into an Asset
So, you have a powerful Cisco Meraki network. Think of it as the plumbing for your business—it's fast, reliable, and secure. But what if you could do more than just provide a connection? What if you could turn that connection into a genuine business tool? This is precisely where specialized integrations, like what we do at Splash Access, come into the picture.
Here's a good way to look at it: Meraki lays down the foundational connection, and solutions like ours add a layer of intelligence and branding on top. Instead of a bland password box, you can roll out a fully branded welcome mat for your visitors. You're transforming a simple login into a valuable interaction.
More Than Just a Password: Advanced Captive Portals
A basic guest network is fine—it gets people online. But an advanced Captive Portal turns your Wi-Fi into a marketing and engagement engine. This is a game-changer in places like Retail and Education, where that first digital touchpoint can make a real difference.
Instead of a generic login screen, imagine a portal that offers so much more:
- Social Media Logins: Let guests connect using their Facebook or Google accounts. It’s easier for them and gives you valuable, aggregated demographic insights.
- Branded User Experience: Customize the login page with your logo, brand colors, and current promotions. It creates a seamless, professional feel right from the start.
- User Surveys and Feedback: Want to know what your customers think? Ask a quick question when they log in to gather immediate feedback on your services.
- Payment Gateways: If you offer tiered or premium Wi-Fi access, you can build payment options right into the login flow.
Features like these elevate your guest network from a cost center to an active part of your customer experience strategy. If you're curious about the mechanics, our guide on how to set up guest Wi-Fi is a great place to start.
Turning Connectivity into Insight
The second major benefit is digging deeper with analytics. The Cisco Meraki dashboard gives you fantastic network-level data, but integrated platforms can tell you about the people using your Wi-Fi. This is where you get real business intelligence.
By layering an advanced analytics platform over your Meraki network, you move from simply managing traffic to truly understanding visitor behavior.
For a Retail store, that could mean analyzing foot traffic to see which aisles or displays draw the most attention. In a large Corporate campus, it could help you understand how visitors move between buildings or which meeting rooms are most popular. It’s all about using anonymized data to make smarter decisions about how you manage your physical space.
Ultimately, it's this combination that works so well. Cisco provides the robust hardware and cloud management, while specialized authentication solutions open up a world of customization and insight, turning every connection into a meaningful business interaction.
Answering Your Cisco Meraki Questions
After diving into everything the Cisco Meraki platform can do, from its slick cloud dashboard to sophisticated authentication methods, you probably have some practical questions buzzing around. Let's tackle a few of the most common ones we hear from folks in Education, Retail, and Corporate offices as they get to grips with Cisco Meraki.
Does Cisco Meraki Require a License to Work?
Yes, absolutely. Every piece of Cisco Meraki hardware needs an active license to function and be managed through the cloud. It’s best to think of this not as an extra fee, but as the subscription that keeps the whole system humming.
This license is your ticket to the dashboard, firmware updates, and 24/7 technical support—all crucial for keeping your network secure and performing at its best. If a license lapses, you won't be able to manage the device, and after a short grace period, it will eventually stop passing traffic. It really is the key that keeps the engine running.
Is Cisco Meraki Right for My Small Business?
Without a doubt. One of the biggest advantages of the platform is how beautifully it scales. The same simplicity and power that serve a massive Corporate campus with thousands of users also make it a perfect fit for a small coffee shop with just one Wi-Fi access point.
For small businesses that often lack a dedicated IT department, the cloud dashboard is a game-changer. It delivers enterprise-level features and security—like Captive Portals and robust authentication solutions—without needing a network engineer on staff to configure everything.
Meraki was built from the ground up to make powerful networking simple, no matter how big or small your organization is. It effectively levels the playing field, giving smaller businesses access to the kind of secure, reliable network that used to be reserved for large enterprises.
How Secure Is a Cloud-Managed Network?
This is a big one, and the answer is: very secure. Security is baked into the DNA of Cisco and Meraki. A common misunderstanding is that "cloud-managed" means your sensitive data is being sent up to the cloud, but that’s not how it works.
Here’s a quick breakdown:
- Encrypted Management: All the management traffic between your Meraki hardware and the cloud dashboard is fully encrypted.
- Local User Traffic: This is the critical part—your actual user data, like the websites people visit or the files they download, stays right there on your local network. It never travels through the Meraki cloud.
- Built-in Security: The devices themselves come loaded with security tools, including a stateful firewall, content filtering, and malware protection.
- Advanced Wi-Fi Security: For securing Wi-Fi in tricky BYOD environments, Meraki supports the latest standards like WPA3 and advanced authentication like IPSK and EasyPSK, which can give every single device its own unique, secure connection.
If you have more questions on your mind, you can always find more answers in our detailed Cisco Meraki FAQ section.
Ready to unlock the full potential of your Cisco Meraki network? Splash Access enhances your guest Wi-Fi with advanced captive portals, powerful analytics, and seamless authentication solutions. Visit us at Splash Access to learn more and turn your network into a powerful business asset.