At its core, an office visitor management system is a smart, digital tool that takes the old-fashioned, messy paper sign-in sheet and completely overhauls it for the modern workplace. Think of it as a friendly digital concierge for your lobby. It automates how you welcome guests, strengthens security, and ensures every visitor gets a polished, professional first impression.
Reinventing the Welcome Mat With Visitor Management
Let's be honest, the days of that flimsy, spiral-bound logbook sitting on the reception desk are over. A modern visitor management system is far more than just a digital check-in; it’s the central nervous system for your front desk, creating a more efficient and secure environment.
This shift is crucial for all kinds of places, from busy corporate headquarters and sprawling university campuses to high-traffic retail stores. They all share the same challenge: managing a constant flow of visitors without friction, especially now that everyone brings their own devices (the BYOD culture).
The Shift from Paper to Pixels
The goal here is simple: make the arrival process smooth and effortless. Instead of visitors squinting at smudged handwriting and struggling to find a working pen, they interact with a clean, simple digital interface. It seems like a small change, but it makes a huge difference in both efficiency and how people perceive your organization from the moment they walk in.
This quick table shows just how big the leap is.
Comparing Old vs New Visitor Management
Here’s a quick look at the key differences between a traditional paper log and a modern office visitor management system.
| Feature | Traditional Paper Log | Modern Visitor System |
|---|---|---|
| Check-in Process | Manual, slow, often messy | Automated, fast, self-service |
| Security | Minimal, easily faked, no verification | High, with photo capture and ID scans |
| Host Notification | Manual call or email from reception | Instant, automatic notifications |
| Data & Reporting | None, impossible to analyze | Real-time dashboards and detailed reports |
| Compliance | Hard to enforce and track NDAs | Digital document signing and tracking |
| First Impression | Outdated and unprofessional | Modern, tech-savvy, and professional |
As you can see, the modern system isn't just a replacement; it's a complete upgrade that touches every part of the visitor experience.
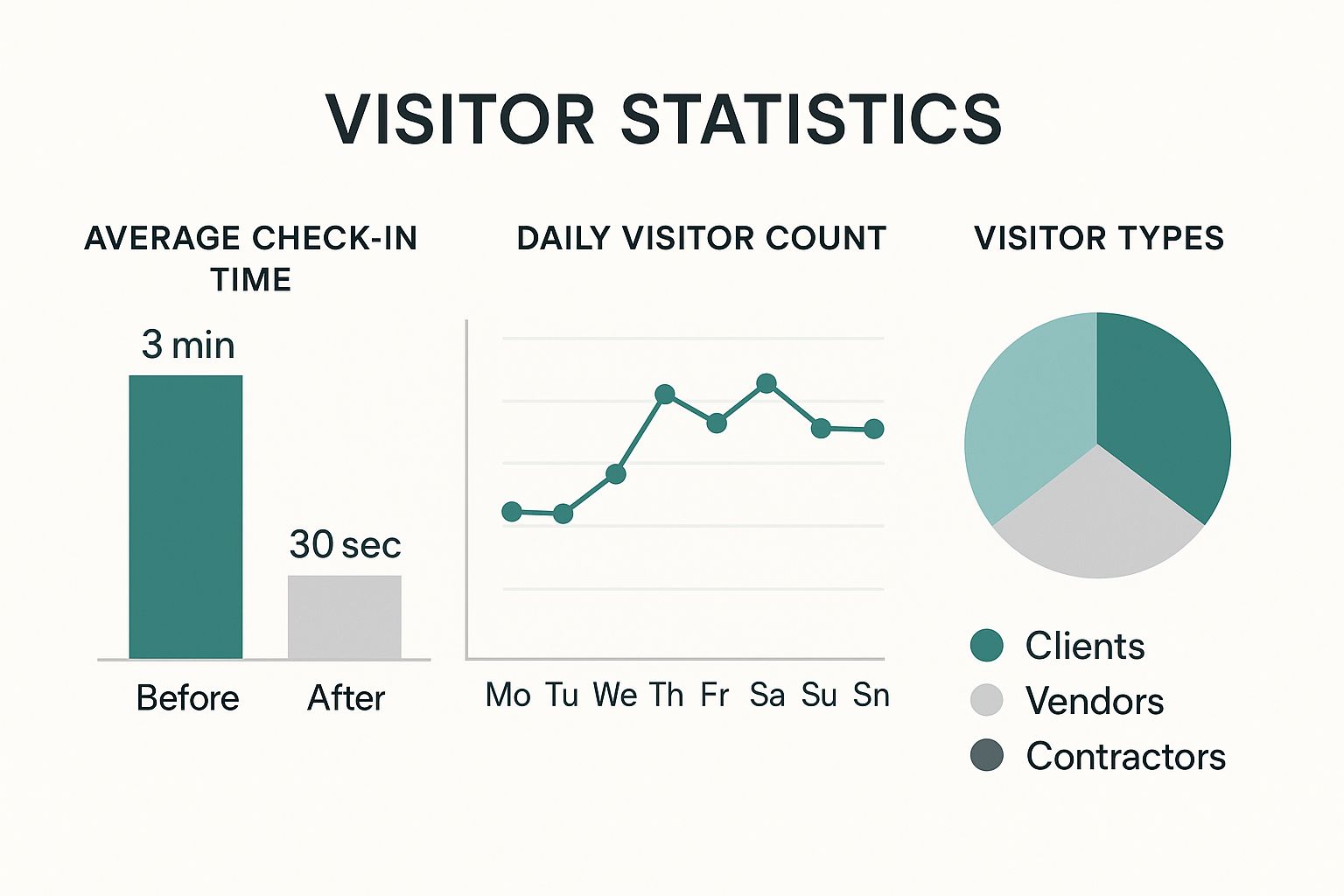
This infographic really drives the point home, breaking down how a digital system drastically improves everything from check-in times to how you manage and categorize visitor traffic.
The numbers don't lie. Automating the process not only makes things faster but also gives you a treasure trove of data about who is coming and going from your building.
Connecting Guests Securely
A huge part of welcoming visitors today is offering them reliable and secure Wi-Fi. This is where a great visitor management system really shines, especially when it works hand-in-hand with powerful networking hardware from companies like Cisco and Meraki.
Instead of a receptionist handing out a generic password scribbled on a sticky note—a huge security risk—the system can automatically grant temporary, secure network access as soon as a guest checks in. This is usually done through a Captive Portal, which acts like a secure digital lobby for your Wi-Fi network. You can dive deeper into how a WiFi captive portal works to keep your network safe.
The real magic happens when you integrate visitor identity with network access. By linking a guest's check-in details to their device, you create a secure, auditable trail that protects your internal network.
This integrated security is a must for any organization today. It’s no wonder the market for these systems is expected to balloon to around USD 6.9 billion by 2035, reflecting a worldwide push for smarter, safer offices.
Technologies like IPSK (Identity Pre-Shared Key) and EasyPSK take security to the next level. They assign a unique, personal "key" to each visitor's device. This means that even on a guest network, every single user is individually identified and accounted for—a perfect security layer for corporate environments where everyone brings their own laptops and phones.
The Core Features That Actually Make a Difference
When you boil it down, a modern visitor management system is designed to do two things: make the check-in process smooth and keep your workplace secure. Forget the messy paper logbooks and chaotic lobbies. Let's get into the specific features that make this happen behind the scenes.
Picture this: a key client is on their way for a meeting. Instead of making them wait at the front desk, you’ve already pre-registered them. The system automatically sends a welcome email with directions, parking info, and a QR code for a quick, touchless check-in. It’s a small touch that makes a big first impression.
The moment they scan that code, their host gets a notification—maybe on Slack or a quick email—saying their guest has arrived. No more awkward waiting. No more frantic calls from reception. It’s just a simple, seamless handoff that looks incredibly professional.
Layering Your Security
Beyond creating a great visitor experience, these systems are fundamentally about security. They add layers of protection that a clipboard and pen could never provide. This is a core part of a bigger strategy like enterprise access control, where every entry point is managed and monitored.
Here’s how they build that digital fortress, one feature at a time:
- On-Demand Badge Printing: The system can instantly print a professional, custom visitor badge. It typically includes their photo, name, and who they're visiting, making it easy for your team to see who belongs and who doesn't at a glance.
- Watchlist Screening: As a visitor checks in, the system can automatically and discreetly cross-reference their name against internal or external watchlists. This flags potential security risks before they ever set foot past the lobby.
- Digital Document Signing: If you need visitors to sign an NDA, a health screening, or a safety waiver, it can all be done on the spot. The platform captures their digital signature and stores a time-stamped record, which is perfect for compliance and audits.
These aren't just "nice-to-have" features; they're essential in many environments. In an Education setting like a school, it means every contractor is properly vetted. In a Retail warehouse, it helps ensure only authorized vendors are in restricted areas. In a BYOD Corporate office, it’s the first line of defense.
The real goal is to turn your reception area from a simple doorway into an intelligent security checkpoint that works quietly in the background.
Bridging the Physical and Digital Worlds
Truly great systems don't just track who is physically in your building; they also manage what those guests can access on your network. This is where integrations with hardware from companies like Cisco and Meraki come into play.
When a guest checks in, the system can automatically provision temporary, secure Wi-Fi access for them. It’s not just about convenience—it’s a huge security upgrade.
By using tools like Captive Portals and sophisticated Authentication Solutions like IPSK or EasyPSK, you can keep guest traffic completely separate from your core business network. Every visitor gets their own unique "key" to the Wi-Fi that automatically expires when they check out. This eliminates the massive risk that comes with a shared, static Wi-Fi password. Better yet, it creates a full audit trail, connecting a person's physical identity to their digital footprint on your network.
Integrating Secure Guest Wi-Fi for Visitors
Offering visitors Wi-Fi has gone from a nice-to-have gesture to a core business expectation. But just scribbling a password on a sticky note for everyone to share is like leaving the front door key under the mat—it’s a massive security hole waiting to be exploited. This is where a modern office visitor management system really proves its worth, transforming a potential security nightmare into a smooth, secure process.
Tightly integrating your visitor check-in process with your network hardware is a game-changer. It’s not just about making life easier for guests; it's about adding a critical layer of security, especially for businesses running on robust infrastructure from providers like Cisco and Meraki. When these systems talk to each other, you build a smart, secure bridge between a person's physical arrival and their digital access.
The Captive Portal: Your Digital Lobby
Ever connected to the Wi-Fi at an airport or coffee shop? That branded login page you see before you can browse is a Captive Portal. Instead of thinking of it as a technical hurdle, see it as a secure "digital lobby" for your network.
Rather than leaving your network wide open, a Captive Portal acts as a friendly gatekeeper. It’s the point where your visitor management system steps in, automatically granting access only after a visitor has successfully signed in. This simple step ensures every device on your guest network is tied to a known, registered individual who is physically present in your building. You can learn more by exploring our guide on how to set up guest WiFi securely.
This intelligent approach is absolutely essential in a few key environments:
- Education: Makes sure only registered guests, parents, or approved vendors can get on the campus network, keeping student data and internal systems safe.
- Retail: Gives secure Wi-Fi to contractors and suppliers in back-of-house areas without ever exposing sensitive point-of-sale or inventory networks.
- BYOD Corporate: Helps manage the daily flood of personal devices—laptops, tablets, and phones—that visitors bring into the office.
Moving Beyond the Shared Password
The single biggest flaw with a traditional guest network is the shared password. Once that password is out there, you have no idea who is using it. Revoking it is a pain, requiring you to update every person and every device. This is where modern Authentication Solutions like IPSK and EasyPSK completely change the game.
IPSK (Identity Pre-Shared Key), often called EasyPSK, is a method that generates a unique, personal password for every single visitor’s Wi-Fi access. Think of it like a hotel room key—each guest gets a key that only opens their door, not a master key that opens every door in the building.
The security advantage here is enormous. As soon as a visitor checks out, their personal Wi-Fi key is automatically and instantly deactivated. Their access vanishes without disrupting any other guests who are still connected.
The Power of Automated Authentication
Picture this: a consultant arrives at your office for a week-long project. As they complete their digital check-in, the visitor management system talks directly to your Cisco Meraki network. In an instant, it generates a unique IPSK for the consultant. This key is valid only for their registered devices and only for the duration of their visit.
This simple, automated workflow solves several problems at once:
- Eliminates Password Sharing: The risk of a shared password being leaked or misused is completely gone.
- Creates a Clear Audit Trail: You now have a precise record of who was on your network, what devices they used, and exactly when they were connected.
- Provides a Frictionless Experience: The visitor gets online quickly and securely without ever having to ask a receptionist or bother your IT team for a password.
The growing need for this kind of integrated security is a huge reason why the visitor management system market is expanding so quickly. Projections show the market, valued near USD 1.66 billion in 2024, is on track to hit an estimated USD 7.26 billion by 2034. This surge is fueled by a global focus on making offices smarter and more secure.
How Visitor Management Works in Different Industries
A visitor management system isn't a one-size-fits-all product. Think of it more like a versatile toolkit that can be adapted to solve the unique problems of different workplaces. While the core goals—better security and smoother operations—are pretty much universal, how you get there looks a lot different in an Education environment than it does in a BYOD Corporate skyscraper.
Let's break down how these systems are put to work in a few key sectors. You'll see just how flexible this technology can be when tailored to specific, real-world needs.
Corporate Offices and the BYOD Challenge
In any modern BYOD Corporate setting, one of the biggest headaches is dealing with the sheer volume of personal devices. Every guest, contractor, and interviewee walks through the door with a laptop, smartphone, or tablet. This creates a huge security blind spot if you're not careful.
This is where a good visitor management system really shines. When a guest signs in, the system does more than just print a name badge; it can kickstart a secure network onboarding process. By integrating with network hardware from companies like Cisco and Meraki, it automates guest Wi-Fi access without compromising security.
How does it work? Usually through a Captive Portal—that familiar login page you see at airports and cafes. Instead of handing out a generic, easily-shared password, the system uses robust Authentication Solutions like IPSK (Identity Pre-Shared Key) to generate a unique, temporary Wi-Fi key for each and every visitor. That key is tied directly to them and automatically deactivates the moment they check out. Your internal network stays completely walled off and secure.
Keeping Students Safe in Education
For schools, colleges, and university campuses in the Education sector, visitor management boils down to one critical mission: student safety. The number one priority is knowing exactly who is on the grounds at all times, whether it's a parent, a volunteer, or a third-party contractor. An effective visitor system acts as a smart, reliable gatekeeper.
Upon arrival, every visitor has to check in, often by simply scanning a government-issued ID. The system can instantly and discreetly cross-reference their information against internal watchlists or even official registered sex offender databases. Any potential red flags are raised immediately, before that person gains access.
On the network side, an integration with something like Cisco Meraki ensures that while a guest can get online, they are firewalled from any sensitive student or administrative data. Using a Captive Portal with IPSK keeps guest traffic completely separate from the networks that run the school.
The system creates a detailed, time-stamped log of every single person who comes and goes. For administrators, this provides not only incredible peace of mind but also a critical record in case of an emergency.
Boosting Efficiency in Retail Operations
The Retail world lives and dies by speed and efficiency. Think about the back-of-house areas, loading docks, and warehouses—they see a constant parade of vendors, delivery drivers, and service technicians. Managing this flow without slowing down store operations or creating security holes is a massive logistical puzzle.
A visitor management system automates that entire dance. A pre-registered vendor, for instance, might get a QR code sent to their phone ahead of time. When they arrive, they just scan it at a kiosk, print their own badge, and get to work. This kind of self-service frees up your staff to stay on the sales floor helping customers.
Even guest Wi-Fi, a retail staple, follows the same security principles. Providing great connectivity is a proven way to improve the customer experience, and you can see how this is applied in similar guest-centric environments like modern hotel WiFi solutions.
This automation also handles compliance beautifully. The system can require contractors to digitally sign safety waivers or acknowledge company policies before it will grant them access to certain areas. It creates a seamless, secure, and fully documented process that keeps the retail machine humming. These same principles are becoming essential in the world of hybrid event production, where managing both in-person and online attendees demands a secure, frictionless experience for everyone involved.
The following table breaks down these sector-specific needs at a glance, showing how the core technology adapts to different environments.
Sector-Specific Visitor Management Needs
| Sector | Primary Challenge | Key VMS Solution Feature |
|---|---|---|
| BYOD Corporate | Securing the network from a high volume of personal devices | Automated, secure Wi-Fi onboarding with unique, temporary credentials (IPSK/EasyPSK) |
| Education | Ensuring student safety by vetting and tracking all non-staff personnel | Real-time watchlist and background checks with detailed, auditable visitor logs |
| Retail | Managing high-traffic, non-customer areas without disrupting operations | Self-service check-in kiosks (e.g., QR codes) and automated compliance workflows |
As you can see, the "best" visitor management setup isn't about the technology itself, but about how intelligently it's applied to solve the most pressing problems for a particular industry.
Choosing and Implementing Your System
So, you're ready to upgrade your front desk? Honestly, moving to a modern office visitor management system is one of the smartest investments you can make for both security and efficiency. But let's be real—with so many options out there, figuring out where to even start can feel overwhelming.
Let's walk through the key decisions to help you pick the right platform and get it running without a hitch.
The first big fork in the road is deciding between a cloud-based or an on-premise solution. While on-premise systems put you in direct control of all the hardware, they often come with the headache of maintenance and can be a real pain to scale up later.
Cloud-based systems, on the other hand, have become the standard for a reason. They offer incredible flexibility. You can manage multiple locations from a single dashboard, which is a lifesaver for any business with more than one office. The market trend is crystal clear on this: forecasts show that by 2034, cloud solutions will likely make up about 63.5% of the market. Why? Because they're just easier to scale and use.
The Power of Smart Integrations
A great visitor management system doesn't live on an island. Its true value shines when it talks to the tools you're already using every day. These seamless integrations are what elevate a simple check-in app into the central hub for your entire office's security and guest experience.
Think about your network. Your system needs to play nicely with hardware from big names like Cisco and Meraki. This is how you automate secure guest Wi-Fi access the second a visitor checks in—a non-negotiable for any modern BYOD Corporate environment.
This kind of integration is the secret to unlocking serious security features. It allows you to use Captive Portals as a secure front door to your network. Instead of handing out the same old shared password, powerful Authentication Solutions like IPSK (also known as EasyPSK) can automatically create a unique, temporary Wi-Fi key for every single guest. This is a total game-changer, especially in Education and Retail, where managing network access for a constant stream of temporary visitors is a top priority. You can learn more about how this works in our detailed guide to captive portal solutions.
Your Roadmap to a Smooth Rollout
Once you've landed on a system that fits your business, a solid implementation plan is what separates a smooth launch from a frustrating one. This is about more than just plugging in a tablet; it’s about introducing a new, better process to your team and your visitors.
Here’s a simple roadmap to get you there:
-
Plan and Configure: Start with your goals. What visitor info do you absolutely need? Do you require NDAs or safety waivers signed on the spot? Take the time to configure the check-in flow, customize the welcome screen with your company's branding, and set up how you want hosts to be notified (Slack, email, or text).
-
Integrate Your Tools: This is where the magic happens. Connect the visitor system to your Cisco Meraki dashboard to get that automated guest Wi-Fi working. Link it to your employee directory so hosts can be found and notified in an instant.
-
Train Your Team: A tool is only as good as the people using it. Get your front desk team, office managers, and anyone else involved up to speed. Show them how to pre-register guests, navigate the dashboard, and handle any little hiccups that might pop up.
-
Launch and Communicate: It's go-time! Place your check-in kiosk somewhere obvious and accessible. But most importantly, tell your employees what's happening. A quick email explaining the new, easier way their guests will be welcomed goes a long way.
Answering Your Top Questions About Visitor Management
As you start thinking about modernizing your front desk, a few key questions always come up. It's smart to have these answers before you make a move, so let's walk through the most common ones. We'll get into the nitty-gritty of security and how these systems plug into your existing network.
How Does This System Actually Make My Office More Secure?
This is usually the first question people ask, and for good reason. The answer is twofold, covering both physical and digital security.
First, on the physical side, you get a digital, time-stamped log of every single person who walks through your door, often complete with their photo. This gets rid of the old, messy paper logbook and stops anonymous entries in their tracks. It also means you can discreetly check visitors against internal watchlists as they sign in.
Just as important is the digital security. When the system is connected to your network gear from companies like Cisco and Meraki, it completely automates secure Wi-Fi access for guests. It routes them through a Captive Portal, which walls them off from your private company network and all your sensitive data.
What Exactly Is a Captive Portal?
Think of a Captive Portal as the secure, digital front desk for your Wi-Fi. It’s that branded login page you see at a hotel or coffee shop when you first try to connect to their network. Instead of a simple password field, it’s a controlled entry point that verifies who is trying to get online.
A smart visitor management system uses this portal to grant access automatically. As soon as a guest finishes checking in on the kiosk, the system gives their device a green light through the portal. This simple step connects their real-world identity to their online activity, giving you a complete, airtight security record.
The real power of a modern visitor system is how it blends physical security with network protection. It makes sure every person in your building is accounted for, both in the lobby and on your Wi-Fi.
Can We Use This System Across All Our Office Locations?
Yes, and this is where modern cloud-based platforms really shine. A single, central dashboard gives you a bird's-eye view of all your locations, whether you have two offices or two hundred.
This centralized approach makes life much easier. You can:
- Set Consistent Rules: Make sure every office, no matter where it is, follows the exact same security and sign-in process.
- See the Big Picture: Pull unified reports to analyze visitor traffic and patterns across your entire company from one screen.
- Maintain Your Brand: Give every guest the same professional, polished welcome experience, no matter which location they're visiting.
For any business with multiple locations, this approach massively simplifies day-to-day management and helps ensure everyone is following company policy.
What Is IPSK and How Is It a Step Up?
IPSK, which stands for Identity Pre-Shared Key (and is sometimes called EasyPSK), is a much smarter way to handle Wi-Fi passwords. It's a powerful Authentication Solution that gives each user their own unique, private password for the same Wi-Fi network. Forget having one shared "Guest-WiFi-123" password for the whole building; this is like giving every visitor their own personal key.
Why does that matter? A standard shared password, if it ever gets out, puts your entire guest network at risk. With IPSK, each key is tied to a specific person. If a contractor's project ends, you just revoke their individual password, and it doesn't disrupt anyone else. This is a huge security improvement for any BYOD Corporate, Education, or Retail setting because it stops password sharing dead and creates a perfect audit trail.
To see this in action, you can learn more about how to streamline visitor management with IPSK QR Codes and keep your network safe.
Ready to transform your front desk into a secure, efficient, and welcoming experience? Splash Access provides a complete solution that integrates seamlessly with your Cisco Meraki network to automate guest Wi-Fi, enhance security with IPSK, and deliver a polished first impression every time. Learn more about how Splash Access can work for you.