Hey there! When you think about guest WiFi, do you just picture a password scribbled on a whiteboard? If so, it's definitely time for an upgrade. Setting up a proper guest network is all about creating a secure, separate network that’s completely walled off from your sensitive business data. The great news is that modern systems like Cisco Meraki make this incredibly simple and powerful to do.
Why Modern Guest WiFi Is More Than Just a Password
Let's be honest, offering internet access to visitors is table stakes these days. But a truly effective guest network does so much more than just get people online. It becomes a secure, branded, and insightful experience that can genuinely benefit your organization.
This isn’t a one-size-fits-all situation, either. The needs of a retail store are vastly different from those of a university in the education sector or a corporate headquarters managing a BYOD policy.
This guide is designed to take you beyond the basic settings on your router. We're going to dig into building a professional-grade guest network using powerful tools from partners like Cisco. I'll walk you through how to design a welcoming Captive Portal and weigh the pros and cons of different modern Authentication Solutions, including cool tech like IPSK and EasyPSK.
A Strategic Asset for Every Sector
The demand for solid connectivity isn't just growing; it's exploding. The global Guest Wi-Fi market was pegged at around $2.5 billion in 2025, and it’s projected to grow at a 15% compound annual growth rate (CAGR) through 2033. This isn't surprising when you consider how attached we all are to our smartphones. Good WiFi is no longer a perk; it's a key part of the customer and visitor experience.
When done right, a guest network can be a real strategic asset.
- Retail: It’s a direct line to your customers for marketing and a goldmine for understanding foot traffic and behavior.
- Education: It’s essential for managing the flood of student devices (BYOD) in a controlled and secure way.
- Corporate Offices: It provides a safe "on-ramp" for visitors, partners, and even employees' personal devices, all without ever touching your core network.
Balancing Security and Simplicity
The classic struggle with guest access has always been making it easy for users while keeping it locked down tight for security. This is where newer Authentication Solutions have really changed the game. Technologies like IPSK (Identity Pre-Shared Key)—and even more user-friendly spins like EasyPSK—are a massive leap forward.
These systems let you issue a unique key for each person or device. This gives you incredibly detailed control without the headache and complexity of old-school enterprise setups.
A great guest WiFi experience should feel effortless for the user but be incredibly secure behind the scenes. This is the new standard for businesses, schools, and public venues.
Consider this guide your blueprint. It's about turning a simple amenity into a tool that protects your data while seriously impressing your guests.
Building Your Network Foundation with Cisco Meraki
A truly great guest WiFi experience doesn't start with the splash page or the password. It starts with the hardware. And for that, we have to talk about Cisco Meraki. Their platform is our go-to for a reason—it provides a powerful, cloud-managed foundation that’s surprisingly easy to work with, whether you're a small shop or a sprawling campus.
What makes Cisco Meraki so effective is its central nervous system: the Meraki dashboard. Forget command-line interfaces or clunky on-premise controllers. Everything from configuration to troubleshooting happens in one clean, web-based portal. This is a lifesaver for organizations that don't have a massive IT team, from busy corporate offices to bustling campuses in the education sector.
Planning Your Physical Layout
Before you ever log into that dashboard, you need to think about the physical world. Where you place your access points (APs) is one of the most common—and critical—things people get wrong. You can't just bolt them to the ceiling and hope for the best.
-
Retail Spaces: Think like your customers. Where do they walk? You'll want APs covering entrances, checkout areas, and key product aisles to ensure a seamless connection and to gather better foot traffic data.
-
Multi-Floor Offices: Don't stack your APs directly on top of each other. Stagger them between floors to minimize signal interference and provide consistent coverage in meeting rooms, open-plan spaces, and private offices.
-
Educational Campuses: Schools are a whole different beast. You have high-density zones like libraries, cafeterias, and auditoriums. Your AP placement has to be deliberate to handle hundreds of BYOD (Bring Your Own Device) connections hitting the network all at once.
A well-planned AP layout is the invisible hero of a great WiFi experience. It eliminates dead zones and ensures that from the front door to the back office, the connection is solid and reliable. Get this right, and everything else—from Captive Portals to advanced security—just works better.
The Most Important First Step: Creating a Guest SSID
Alright, let's get into the dashboard. The single most important thing you will do is create a separate network just for your guests. This is your SSID (Service Set Identifier), the name people will see on their phones, like "MyCafe_Guest."
This isn't just for convenience; it's a fundamental security measure. By creating a dedicated guest SSID, you're building a digital wall between your visitors and your internal, trusted network. All guest traffic is firewalled off, meaning they have zero access to your point-of-sale systems, company servers, or private files. It's non-negotiable.
This network segmentation allows you to be hospitable without being reckless. Later on, we’ll layer on sophisticated Authentication Solutions like IPSK or EasyPSK to this network. But for now, creating that separate SSID is the first, essential move you must make. Think of it as giving guests their own secure entrance, keeping your private operations completely untouched.
Designing a Branded Welcome with a Captive Portal
With the technical groundwork laid, let's shift to what your guests will actually see first: the welcome screen. This is your moment to make a great first impression. We're talking about the Captive Portal—that splash page that appears right after someone selects your guest Wi-Fi network.
Don't settle for a generic login box. Treat this as your digital handshake. By integrating a platform like Splash Access with your Cisco Meraki network, you can completely transform this page. Add your logo, use your brand colors, and craft a personalized welcome message.
This one step immediately elevates the experience, turning a basic utility into a polished, professional touchpoint. A consistent look and feel are crucial here. If you need help, you can learn how to create effective brand guidelines to keep everything aligned. That consistency reinforces who you are from the moment a guest connects.
More Than Just a Pretty Face
A well-designed Captive Portal does much more than just look good. It's a critical control point and a cornerstone of any secure guest Wi-Fi setup. This is where you lay down the rules of the road for your network.
For virtually any organization, requiring guests to accept an Acceptable Use Policy (AUP) is non-negotiable. It's a simple checkbox, but it provides a significant layer of legal protection by ensuring users agree to your terms before they get online. It clearly defines what is and isn't permitted on your network.
This becomes especially powerful in different environments:
- Education: A Captive Portal is the perfect spot to display CIPA compliance notices or reinforce the school's digital citizenship policies before anyone connects.
- Corporate BYOD: In an office, it ensures that employees or visitors connecting personal devices first acknowledge the company's security rules for the guest network.
- Retail & Hospitality: It’s a prime opportunity to communicate promotions, store hours, or events. You can explore more on this with our deep dive into https://splashaccess.com/hotel-wifi-solutions/.
The Portal as Your Authentication Hub
Your Captive Portal is also the public-facing front door for whatever Authentication Solutions you've put in place. It’s the user interface for the login method you’ve chosen for your environment.
Will users simply click through after accepting your terms? Will they log in using a social media profile? Or will they need to enter a unique password, perhaps through a secure method like IPSK or EasyPSK? The portal is what makes this interaction happen smoothly.
The Captive Portal is where user experience and network security meet. It’s the bridge between your brand and your security policy, creating a controlled and seamless onboarding for every guest.
For instance, a retail shop might opt for a social login to gather valuable marketing insights. A corporate headquarters, on the other hand, will likely present a clean, professional portal that asks for an EasyPSK credential, putting security first for its BYOD users.
Ultimately, designing your Captive Portal is about turning a technical step into a strategic asset. It's your chance to welcome guests properly, communicate important policies, and maintain tight control over who gets on your network—and how.
Choosing the Right Guest Authentication Method
So, you’ve got a sharp-looking Captive Portal ready to go. Now for the big question: how are people actually going to log in? This isn't just a technical footnote—it's a critical decision that dictates your network's security and shapes the entire guest experience. The Authentication Solution you land on is the handshake between your network and your visitors.
The right choice really depends on who you are and what you need. A small coffee shop's goals are miles apart from a corporate headquarters juggling a BYOD policy. Let's walk through the most common Authentication Solutions to find the perfect fit for your setup.
H3: Simple and Swift Access Methods
For many businesses in retail or hospitality, the name of the game is getting people online with zero hassle. When friction is the enemy, a couple of straightforward methods really shine.
- Click-Through Access: This is as simple as it gets. A guest sees your branded Captive Portal, clicks a button to accept your terms, and they're online. It’s fast, painless, and perfect for places where instant access is the priority.
- Social Media Login: Here, users log in with their existing social accounts like Facebook or Google. It’s still incredibly easy for them, but it gives you a treasure trove of aggregated demographic data, helping you understand your customers on a deeper level.
These methods are fantastic for creating a low barrier to entry, but they offer minimal security. You don't really know who is on your network, just that someone clicked "I Agree." That's perfectly fine for a cafe, but it's a non-starter for environments handling sensitive data.
H3: Stepping Up Security with Verified Access
When you need a bit more control and want to know who's connecting, asking for an email address or phone number is a solid next step.
With this approach, a user types their contact info into the portal. The system can then fire off a verification link or a code via email or SMS. Once they click the link or enter the code, they're granted access. This gives you a verifiable contact point for every user on the network—a great middle ground for venues that want to build a marketing list while adding a light layer of accountability.
It's no surprise that the market for these kinds of platforms is booming. Valued at roughly USD 1.7 billion in 2023, the guest Wi-Fi platform market is projected to reach USD 4.1 billion by 2032. This surge is fueled by the growing need for secure, manageable connectivity everywhere.
H3: The Gold Standard for Secure Access: IPSK and EasyPSK
For corporate and education environments, security isn't just a feature—it's a non-negotiable requirement. This is where click-through access simply doesn't cut it. You need something more robust, and that's where Identity Pre-Shared Keys (IPSK) come in, a technology that delivers serious security with surprising simplicity, especially when managed through a Cisco Meraki network.
Think about a traditional Wi-Fi password. Now, imagine giving every single user or device its very own unique password. That's the power of IPSK.
IPSK transforms guest Wi-Fi from a shared, anonymous key to a system of individual, trackable credentials. It’s like giving everyone their own key to the building instead of leaving the front door unlocked.
Modern takes on this, like EasyPSK, make managing thousands of unique keys shockingly simple. You get the same level of security and accountability as complex enterprise setups (like 802.1X) but with a much more user-friendly admin experience. To really get into the weeds, you can explore various user authentication techniques.
This granular control is a game-changer for a few key scenarios:
- Corporate BYOD: When an employee brings their personal phone or laptop, you can issue a unique EasyPSK just for that device. If they leave the company, you just revoke their key without impacting anyone else.
- Education Campuses: Schools can assign an IPSK to each student for the academic year, providing full accountability and making it easy to manage access for thousands of BYOD devices.
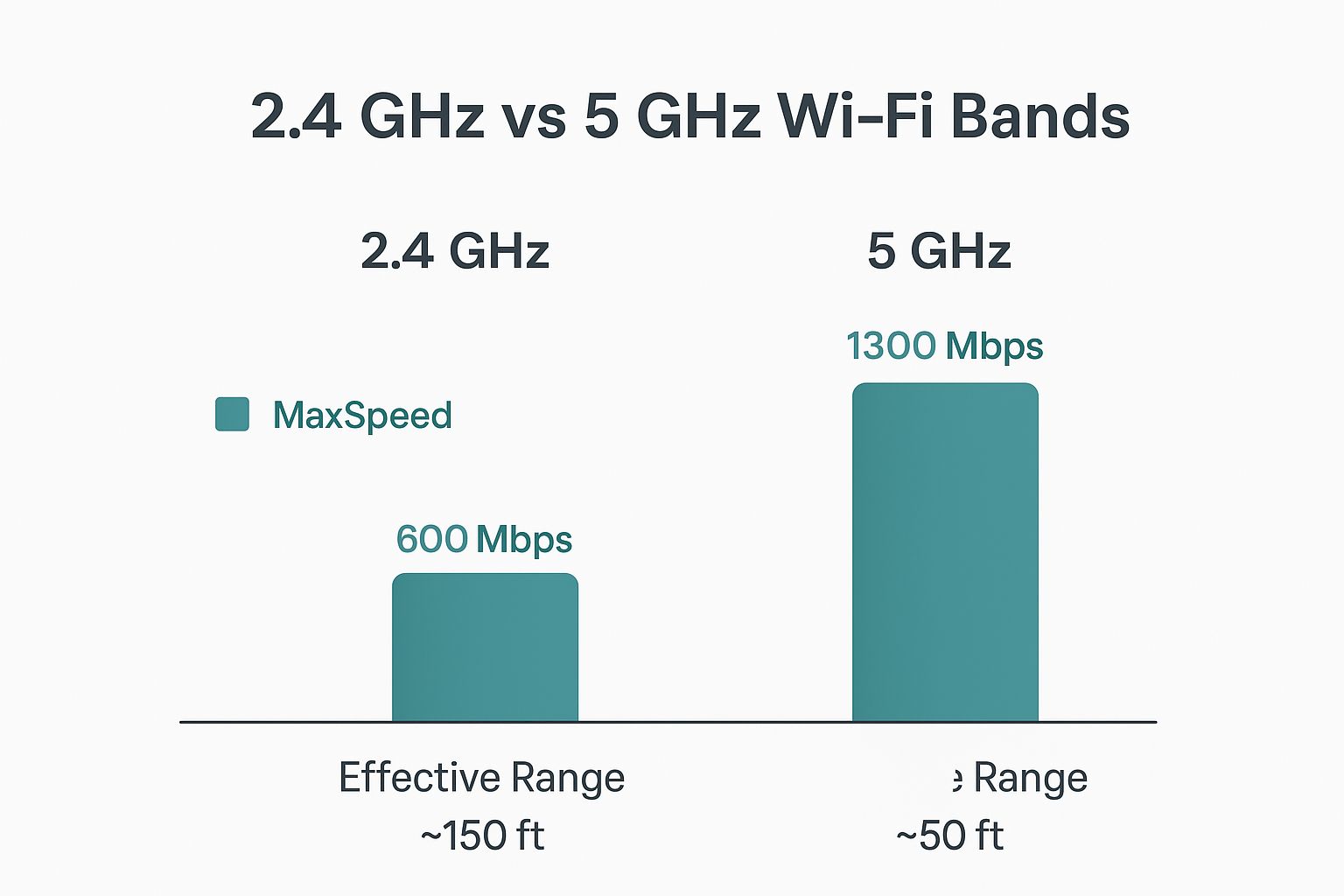
The image below breaks down the differences between Wi-Fi bands, which can influence where you need stronger authentication.
While 5GHz offers faster speeds, its shorter range often means you need more access points in a dense office environment. This makes a scalable Authentication Solution like IPSK even more critical to manage everything effectively.
Guest WiFi Authentication Methods Compared
Choosing your login method isn't just a technical checkbox; it's a strategic decision. The right approach can improve security, simplify management, and enhance the user experience. The wrong one can create headaches for both you and your guests. This table breaks down the most common methods to help you decide.
| Authentication Method | Best For | Security Level | User Experience |
|---|---|---|---|
| Click-Through | Retail, Cafes, Public Spaces | Low | Excellent – fast and frictionless. |
| Social Login | Hospitality, Venues, Retail | Low | Very Good – easy login, provides marketing data. |
| Email/SMS Verification | Malls, Events, Businesses | Medium | Good – requires an extra step but adds accountability. |
| IPSK/EasyPSK | Corporate, Education, Healthcare | High | Excellent – seamless after one-time setup. |
Ultimately, the best Authentication Solution aligns with your organization's specific needs. For public-facing businesses, simplicity is king. For environments where security and accountability are paramount, a more robust solution like IPSK is the clear winner. By understanding these trade-offs, you can build a guest Wi-Fi network that's both powerful and perfectly suited to your users.
Turning Your Guest Wi-Fi into a Business Intelligence Powerhouse
So, you’ve got your secure, branded guest network up and running. It’s a smooth machine. But if you think that’s where the story ends, you're leaving huge potential on the table. It's time to make that network work for you—transforming it from a simple cost center into a powerful business intelligence tool. This is where your investment really starts to pay dividends.
Platforms like Cisco Meraki are designed for more than just pushing out a Wi-Fi signal; they are data collection engines. The analytics baked right into the Meraki dashboard can give you a crystal-clear picture of how people move and interact within your physical space, offering insights that used to be incredibly difficult and expensive to get.
From Foot Traffic to Real-World Strategy
For anyone in the retail world, this is a total game-changer. Imagine seeing beyond your final sales figures to understand the why behind them. Meraki's location analytics can show you:
- Visitor Foot Traffic: How many people actually walk through your doors daily, weekly, or monthly?
- Peak Usage Hours: When are you slammed? This data directly informs your staffing schedules, so you have the right people on the floor when it matters most.
- Dwell Times: How long are people sticking around? Are they just grabbing one item and leaving, or are they browsing? This can help you fine-tune your store layout and product placement.
By digging into this data, a retailer can optimize everything from promotional displays to employee breaks. It's like having a digital consultant constantly observing your store's rhythm. Of course, collecting the data is just the first step; the real value comes when you turn data into actionable insights that inform your strategy.
Justifying Upgrades and Planning for Growth
This isn't just a retail play. For large corporate headquarters or sprawling education campuses, these same analytics serve a different but equally critical purpose. Network administrators can finally answer key questions with hard data, not guesswork.
Instead of estimating, IT teams can pinpoint which areas of a building have the highest device density. They can track network usage patterns to identify bottlenecks before they become major problems. This information is gold when you need to justify infrastructure upgrades, plan for future capacity, or ensure a seamless experience in high-demand BYOD environments.
Your guest Wi-Fi network is constantly generating a rich stream of data about your physical environment. By tapping into it, you're not just managing a network; you're gaining a strategic advantage.
Connecting Your Captive Portal to Your Marketing Engine
Now, here's where the real magic happens: integrating your Captive Portal with your other business systems. That branded welcome screen we set up? It can do a lot more than just look pretty and handle Authentication Solutions like IPSK. It can become an active part of your marketing and customer engagement strategy.
Think about these real-world scenarios:
- A hotel guest logs into the Wi-Fi and is greeted with a splash page offering a 15% off voucher for the on-site restaurant.
- A shopper in a retail store connects to the guest network and sees a notification about a flash sale happening in the next aisle.
- A student on a campus in the education sector logs in and gets an alert about an upcoming career fair.
Suddenly, that simple internet connection becomes a dynamic, targeted communication channel. And this isn't a niche idea; it's a massive growth area. In 2024, the guest Wi-Fi providers market was valued at about USD 5.1 billion and is projected to hit USD 12.9 billion by 2033. Hotels and retail stores are leading the charge, using these platforms for targeted advertising and loyalty programs based on real user data.
By linking your guest network to your marketing tools, you close the loop between the digital and physical worlds. The insights you gain don't just sit in a dashboard; they actively help you https://splashaccess.com/how-to-improve-customer-experience/ and drive tangible business results. Your guest Wi-Fi is no longer just an amenity—it's a core component of your operational and marketing intelligence.
Common Questions About Guest WiFi Setup
As you start mapping out your new network, questions are bound to come up. That’s perfectly normal. Nailing the details of your guest WiFi setup is a big deal for both security and giving your visitors a great experience. Let's walk through some of the most common questions we get from organizations just like yours.
Is It Safe to Offer Guest WiFi on My Main Business Network?
Let's be crystal clear on this: absolutely not. This is probably the single most important security principle to get right. You should never, ever let guest traffic touch the same network that your critical business systems live on. It's like giving every visitor to your office a key to the server room.
The right way to do this is with network segmentation. Thankfully, modern systems like Cisco Meraki make this surprisingly simple. You can create a completely separate Guest SSID (the network name your visitors will see), which is firewalled off from your internal, private network. This creates a digital wall, making it impossible for anyone on the guest network to even see, let alone access, corporate servers, point-of-sale terminals, or employee computers. This is the bedrock of a secure guest WiFi setup.
What Is the Difference Between a Captive Portal and IPSK?
That's a fantastic question because these two things work together but do very different jobs. I like to think of it as the security for a high-tech building.
-
The Captive Portal is the lobby. It’s the user-facing splash page that greets your visitors. This is where you put your branding, display your terms of service, and show people how they can get online. It's what people see.
-
Authentication Solutions like IPSK (or EasyPSK) are the keycard and the lock on the door. This is the secure method you use to actually grant access. IPSK is a powerful method where each user or device gets its own unique password or "key."
A great, secure user journey looks like this: a guest connects to the WiFi, sees your beautifully branded Captive Portal, and then enters their unique IPSK key to get on the network. The portal is the door; the authentication is the key.
The best systems blend these two elements seamlessly. A user interacts with a beautiful, branded portal and, behind the scenes, a powerful authentication method like EasyPSK ensures the connection is secure and accountable.
Can I Use Guest WiFi to Gather Marketing Information?
Yes, and when it's done responsibly, it can be a phenomenal tool, especially in the retail world. By using Authentication Solutions that ask for an email address or allow for social media logins right on your Captive Portal, you can collect valuable, aggregated data.
This isn't about being invasive; it's about being smart. You can build mailing lists, get a better picture of customer demographics, and even measure visitor loyalty. The key, however, is transparency. Your Captive Portal's terms and conditions must be upfront about what information you're collecting and how you'll use it. This not only builds trust but also keeps you compliant with privacy laws. When done right, your WiFi stops being a simple cost and becomes a real marketing asset.
How Does This Approach Support a BYOD Policy?
A professional setup like this is perfect for managing a Bring Your Own Device (BYOD) policy, whether you're in a corporate office or an education setting. The secret sauce is a robust Authentication Solution like IPSK. By giving a unique credential to each employee's or student's personal device, you get incredibly detailed control and visibility.
You know exactly who is connected at all times. If a device is lost or an employee moves on, you can instantly revoke access for that one device without disrupting anyone else. To see where this technology is heading, you can learn more about seamless, secure connections in our guide on what is Passpoint WiFi, which is the next evolution in this space.
When you pair a secure method like EasyPSK with a Captive Portal that requires users to accept your BYOD policy, you've created the perfect system. It makes sure every personal device connects securely, follows company rules, and stays completely separate from your core network.
Ready to turn your guest WiFi from a simple password into a secure, insightful, and branded experience? Splash Access works directly with your Cisco Meraki hardware to deliver a world-class captive portal and advanced Authentication Solutions. Take control of your network and start delighting your guests today. Visit us at Splash Access to learn more.