Hey there! Ever connected to the Wi-Fi at a coffee shop, airport, or hotel and found yourself on a special login page before you could get online? If so, you've met a captive portal Wi-Fi network.
Think of it as a friendly digital doorman for your network. It "captures" you on a specific webpage before handing over the keys to the internet. But it's so much more than a security checkpoint; it’s the very first hello between a business and its on-site visitors.
What Exactly Is Captive Portal WiFi?
A captive portal is a web gateway that greets a new user's device. The first time they try to visit any website, they're automatically redirected to a special landing page. This is the screen that might ask you to agree to terms, watch a quick ad, or log in with a social media account.
Technically speaking, when your device connects, network hardware like a Cisco or Meraki access point reroutes all your HTTP requests to this dedicated login page. Only after you complete the required action—whatever that may be—is the block lifted and full internet access granted. It's a surprisingly simple idea with some incredibly powerful applications.
Turning a Connection into an Asset
For any business, this technology is a real game-changer. It transforms guest Wi-Fi from a simple amenity—and an operational cost—into a powerful tool for marketing, security, and data collection.
Here’s a peek at how different sectors put it to work:
- Retail: A clothing store can welcome customers with a branded splash page that shows off the latest sale or offers a coupon in exchange for an email address.
- Education: A university can use a captive portal to seamlessly and securely onboard thousands of students to the network, while keeping a separate, more limited guest network for visitors.
- Corporate (BYOD): Companies can streamline their "Bring Your Own Device" policies, allowing employees to securely connect personal phones and laptops to the network with minimal friction, keeping corporate data safe.
To help you see the possibilities, this table breaks down the main advantages of using a captive portal.
Key Benefits of Captive Portal WiFi at a Glance
| Benefit Category | Description | Primary Sector |
|---|---|---|
| Marketing & Branding | Presents a branded splash page to every user, perfect for promotions, announcements, and reinforcing brand identity. | Retail, Hospitality |
| Data Collection | Gathers valuable user data like emails or demographics (with consent) for targeted marketing and analytics. | All Sectors |
| Enhanced Security | Controls who accesses the network, enforces terms of service, and can integrate with advanced authentication methods. | Corporate, Education |
| User Segmentation | Creates different access tiers, offering varied bandwidth or time limits for different user groups (e.g., guests vs. staff). | Hospitality, Events |
| Monetization | Turns free Wi-Fi into a revenue stream through paid access tiers, advertising, or sponsored content. | Venues, Transport |
As you can see, a captive portal is way more than just a login screen; it's a super versatile platform that adapts to all sorts of business goals.
Advanced Authentication for Modern Needs
Today’s captive portals have evolved far beyond a simple shared password. They now integrate with sophisticated Authentication Solutions to dramatically boost security and make life easier for everyone.
A brilliant example is IPSK (Identity Pre-Shared Key). Instead of one password for everyone, IPSK technology assigns a unique, personal "password" to every single user or device on the network. This is a massive leap forward in security, especially in crowded environments like a corporate BYOD setup or an Education campus.
Newer systems, sometimes called EasyPSK, are designed to simplify the management of thousands of these individual keys. This makes high-security solutions practical for large-scale deployments.
The market reflects this growing importance. The global captive portal market was valued at USD 1.95 billion and is projected to expand significantly, proving just how vital this technology has become for modern network management.
These advanced systems offer a secure, scalable, and user-friendly way to manage network access. You can explore the full captive portal for WiFi breakdown to see exactly how these systems are designed and implemented in the real world.
Unlocking the Business Value of Your Guest WiFi
Let's start thinking of your guest WiFi as more than just a courtesy—it's a powerful business tool just waiting to be switched on. A captive portal WiFi system is what flips that switch, transforming your network from a simple cost center into a real strategic asset. It acts as the digital front door to your business, giving you a rare chance to engage with every single person who connects.
Instead of users connecting anonymously and disappearing into the digital ether, the portal creates a moment of interaction. This valuable touchpoint can be used for everything from marketing and security to gathering genuine insights about your visitors. It’s no longer just a technical necessity; it’s a conversation starter.
Turning Connectivity into Opportunity
Imagine the possibilities. For a Retail store, the moment a shopper logs on, you can greet them with a branded splash page featuring a special discount or an invitation to your loyalty program. Suddenly, your WiFi is actively driving sales and building customer loyalty.
In Education, a captive portal is fundamental for managing network access. Universities can securely authenticate thousands of students with their existing credentials, all while offering a separate, more restricted network for campus visitors. This keeps the primary network fast and secure for actual academic work.
Then there’s the Corporate world, where "Bring Your Own Device" (BYOD) policies are now standard practice. A captive portal simplifies how employee-owned devices get onto the network. It acts as a gatekeeper, making sure only authorized users and secure devices can access sensitive company data, often by integrating with advanced Authentication Solutions.
A crucial part of offering a great guest WiFi experience is proving it’s trustworthy. Implementing top enterprise network security solutions is non-negotiable for protecting both your network and your users' data.
This power to control and customize the connection experience is exactly why the market for captive portals is booming. Projections show the market is set to grow from USD 1.15 billion to roughly USD 2.20 billion, fueled by the dual demand for WiFi monetization and tighter network control.
From Cost Center to Revenue Driver
A well-designed captive portal, especially one integrated with a platform like Cisco Meraki, doesn't just manage access—it generates real business value. By making your network an interactive platform, you can directly influence visitor behavior and improve your bottom line.
Here’s a quick look at how a captive portal pays for itself:
- Enhanced Marketing: Use the login page to run targeted campaigns, show video ads, or even run quick surveys to get to know your audience.
- Data-Driven Insights: Collect valuable, opt-in data like email addresses or basic demographics. This information can sharpen your business strategy and fuel future marketing.
- Improved Security: Move beyond a simple, shared password. Modern methods like IPSK (Identity Pre-Shared Key) or EasyPSK give each user a unique key, drastically strengthening your network's defenses.
- Better Customer Experience: A seamless, branded login process makes a professional first impression. Offering clear instructions and a bit of value (like a coupon) turns the login from a chore into a perk.
Putting these features to work directly shapes how people see your brand. A smooth, secure, and valuable connection is a vital part of the modern customer journey. To learn more, see our guide on how to improve customer experience.
Ultimately, a captive portal empowers you to make your WiFi work for you, creating a smarter, more secure, and more profitable environment for everyone.
Choosing the Right WiFi Authentication Method
How a user logs into your WiFi network is a critical decision. It’s a constant balancing act between making access simple for them and keeping your network secure for you. The right authentication method for your captive portal WiFi system really sets the tone for the entire user experience and defines just how strong your digital defenses are.
Think of it like choosing the right lock for a door. A simple latch is easy for anyone to use, but a deadbolt offers far better protection. In the same way, different Authentication Solutions offer their own mix of convenience and security. The best choice depends entirely on your environment—whether it's a bustling Retail store, a sprawling Education campus, or a security-first Corporate office.
The Spectrum of Authentication Options
On one end, you have incredibly simple, low-friction methods. A "click-to-connect" portal where users just agree to your terms is the easiest possible option. Next up are social media logins, where people can connect using their existing Facebook or Google accounts. These are fantastic for marketing but don't offer much in the way of security.
As you move toward stronger security, you'll find methods that require more direct verification:
- SMS/Email Verification: Users provide a phone number or email and get a one-time code. This confirms they have access to that account, at least for the session.
- Voucher Codes: You can hand out pre-generated codes, which is perfect for controlling access duration at places like hotels or conference centers.
- Credential-Based Logins: This is your classic username and password login, often tied into an existing database like a school or company directory.
For many organizations, especially those using robust hardware from providers like Cisco, the real goal is to find a solution that delivers the best of both worlds: serious security that doesn't feel like a chore for the user.
A Smarter Password: IPSK and EasyPSK
This is where more advanced methods like IPSK (Identity Pre-Shared Key) make a huge difference. It’s a brilliant solution that plugs a massive security hole found in traditional WiFi networks. Instead of having one password that everyone shares (and that inevitably gets written on a whiteboard), IPSK gives every single user or device its own unique password for the exact same WiFi network.
Imagine giving every employee a unique key to the office instead of a single master key. If one key is lost or an employee leaves, you only need to deactivate that single key, not change the lock for the entire building. That’s the power of IPSK for your network.
This approach is a massive security upgrade. If one device is compromised, you can instantly kick it off the network without disrupting anyone else. It's the perfect setup for corporate BYOD ("Bring Your Own Device") policies where personal phones and laptops need secure access.
The main challenge, of course, is that managing thousands of unique keys sounds like an administrative nightmare. That’s where technologies like EasyPSK step in. These platforms automate the creation, distribution, and management of all those individual keys, making a high-security system practical and scalable. An IT team in an Education setting can onboard thousands of new students without manually typing a single password.
For a deeper look at the practical steps involved, check out our guide on how to set up guest WiFi with these modern tools. At the end of the day, picking the right authentication method is all about matching the login experience to your specific goals for security, user convenience, and data collection.
Captive Portals in Action Across Different Industries
It’s one thing to talk about the mechanics of a captive portal WiFi system, but it's another thing entirely to see it come to life. Let’s shift from theory to reality and look at how these smart login pages actually work out in the wild across different sectors. The real beauty of a captive portal is its flexibility; it can be molded to fit the specific goals of just about any environment.
Whether we're talking about a busy Retail storefront, a sprawling Education campus, or a secure Corporate office, the right portal setup transforms a simple internet connection into a purposeful, valuable interaction. These real-world stories show the practical power of a well-executed captive portal.
The Retail Experience: A Personalized Welcome
Let's start with the Retail world. Picture a customer, Sarah, walking into her favorite clothing boutique. She pulls out her phone and taps on the store's free WiFi network. Instead of a generic password box, her screen fills with a beautifully branded splash page that perfectly matches the store's chic aesthetic.
The page doesn't just ask her to log in; it makes an offer: "Get 15% off your purchase today when you join our Style Insider club!" Intrigued, Sarah pops in her email address, and instantly, a coupon code appears on her screen. She's not only online but has also been welcomed into the brand's community with a tangible reward.
This simple exchange is a huge win. The store gets a new marketing contact, Sarah gets a discount, and the whole experience feels personal and valuable. It’s a perfect example of turning a standard amenity into a direct sales and loyalty driver. These kinds of tailored captive portal solutions are designed to create exactly these sorts of positive interactions.
The Education Campus: Seamless and Secure Access
Now, let's jump over to an Education setting, like a large university campus running on Cisco Meraki hardware. The challenge here is immense: provide fast, reliable WiFi to thousands of students, faculty, and staff, while also offering simple access for campus visitors.
A single, unified captive portal can handle this beautifully. When a student connects their laptop in the library, the portal prompts them to log in with their existing university credentials. The process is seamless and secure, instantly granting them access to the full-speed student network and all the academic resources they need.
At the same time, when a prospective student and their family visit for a campus tour, they can connect to a separate guest network through the very same portal. Their login experience is different—maybe just a simple click-through agreement or a temporary access voucher. This smart segmentation keeps visitor traffic isolated, ensuring the main academic network stays secure and uncongested.
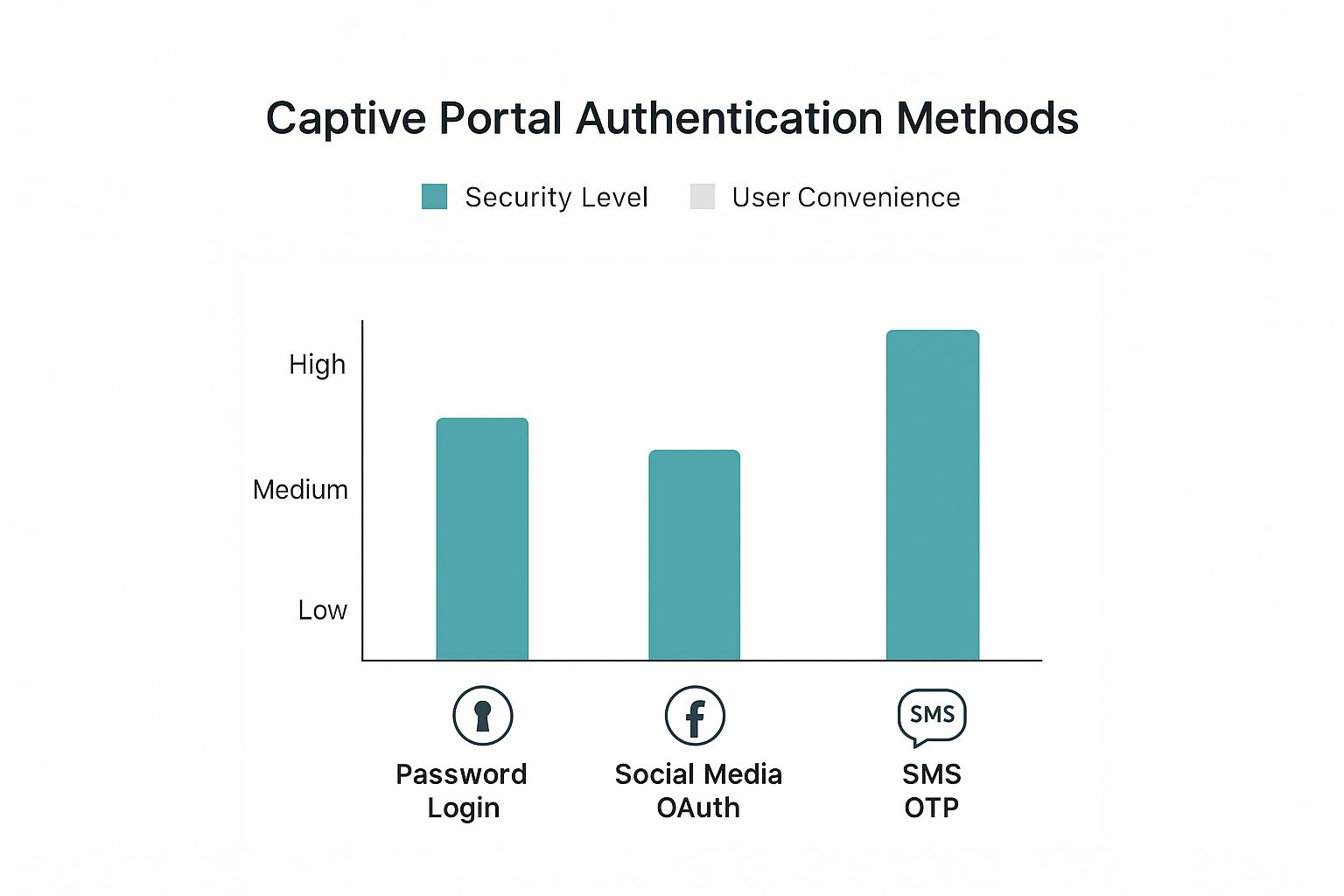
The image below compares a few common authentication methods, showing the trade-off between user convenience and overall security—a balance every IT administrator has to consider.
As you can see, as the security level increases (moving from a simple password to more robust methods), the effort required from the user also tends to go up.
The Corporate Office: Mastering BYOD
Finally, let's look at a modern Corporate office with a "Bring Your Own Device" (BYOD) policy. An employee, Mark, gets a new smartphone and needs to connect it to the company WiFi. The company has to grant him access to necessary resources, like email and shared calendars, without opening up the core internal network to potential threats.
Here, the captive portal is all about security. Mark connects to the "BYOD-WiFi" network and is immediately directed to a login page. This is where more advanced Authentication Solutions come into play. The company uses an IPSK system—often managed through a platform like EasyPSK—to give every single employee device its own unique key.
Mark logs into the portal once with his corporate credentials, and the system automatically generates a unique, private key just for his new phone. This key is tied directly to his identity, giving the IT team full visibility and control over that device.
If Mark ever loses his phone or leaves the company, IT can revoke that single key instantly without affecting anyone else. This granular control is absolutely essential for protecting sensitive data. The captive portal acts as a secure onboarding ramp, ensuring every personal device is properly authenticated and authorized before it ever touches the network, making BYOD both practical and safe.
Captive Portal Features by Industry Sector
The examples above show how different businesses adapt captive portals for their own needs. It's not a one-size-fits-all tool. The features you prioritize will depend entirely on your goals, whether that's marketing, security, or user experience.
This table breaks down how specific captive portal features are typically applied across Retail, Education, and Corporate environments.
| Feature | Retail Application | Education Application | Corporate (BYOD) Application |
|---|---|---|---|
| Social Media Login | Gather demographic data & encourage social shares for marketing. | Offer quick, convenient access for guests and event attendees. | Rarely used; security requires verified corporate identities. |
| Email/Form Capture | Build marketing lists & send promotional offers like discounts. | Register visitors or provide access to short-term users. | Used for guest registration or contractor access portals. |
| Tiered Access Levels | Offer faster speeds for paying customers or loyalty members. | Create separate networks for students, faculty, and guests. | Differentiate access between employees, contractors, and guests. |
| Usage Analytics | Track foot traffic, dwell times, and repeat visits to optimize store layout. | Monitor network load and identify high-demand areas on campus. | Track device types and data usage for capacity planning. |
| Identity-Based Keys (IPSK) | Not typically used; overkill for public guest access. | Securely connect institution-owned devices or staff BYOD. | The core of a secure BYOD strategy for every employee device. |
As you can see, the same underlying technology serves very different purposes. A retailer's portal is a marketing engine, a university's is a complex access manager, and a corporation's is a digital gatekeeper. It all comes down to aligning the portal's capabilities with your strategic objectives.
How to Set Up Your Captive Portal with Cisco Meraki
So, you're ready to build your own captive portal WiFi network? Let's walk through how it’s done. We'll use the popular and surprisingly user-friendly Cisco Meraki platform as our example, but the core ideas apply almost anywhere.
The great news is that you don't need a network engineering degree to launch a professional-grade captive portal. Modern platforms have made it incredibly straightforward. From a single dashboard, you can design a custom splash page, pick the right Authentication Solutions, and set clear rules for who gets on your network and how.
Designing Your Branded Splash Page
Think of your splash page as your digital handshake—it’s the very first interaction someone has with your brand upon connecting. A great one is clean, reflects your brand, and tells people exactly what to do next. With a Cisco Meraki compatible system, you have full creative control.
Here are the key pieces to get right:
- Branding: This is non-negotiable. Upload your logo, use your brand's color palette, and select fonts that feel like you. This instantly reinforces your identity.
- Welcome Message: Keep it simple and friendly. A quick "Welcome!" and a clear call to action, like "Get Online," is often all you need.
- Login Options: Make it obvious how people can connect. Whether it's a simple click-through, a social media button, or a form, the options should be front and center.
And remember, it absolutely must be mobile-responsive. The overwhelming majority of your visitors will see this page on their phones, so it needs to look fantastic and work flawlessly on a small screen.
Think of your splash page as prime digital real estate. If you run a Retail store, this is a golden opportunity to flash a current promotion. In an Education setting, you could display important campus announcements. The secret is to make it relevant to the user standing right there, in that moment.
Selecting the Right Authentication Method
Once the page looks good, you have to decide how people actually log in. This choice is a balancing act between user convenience and network security. For a corporate BYOD network, security is everything. For a local coffee shop in the Retail sector, getting customers online fast is probably the bigger priority.
You can offer a mix of authentication methods, including:
- Click-Through: The path of least resistance. Users simply agree to your terms and are connected.
- Social Login: Lets people log in with their existing social media accounts. This is a fantastic way to gather marketing insights with user consent.
- Credential-Based Login: Requires a username and password. This is common for schools or companies that need to connect logins to an existing user directory.
- IPSK and EasyPSK: For top-tier security, technologies like IPSK (Identity Pre-Shared Key) assign a unique key to every single user or device. Platforms like EasyPSK make managing thousands of these individual keys surprisingly simple, which is why it's a go-to for large deployments in Corporate or Education environments.
Configuring Access Rules and Compliance
The final piece of the puzzle is setting the rules of the road for your network. You get to decide how long people can stay connected, how much bandwidth they can use, and even which websites are off-limits.
This level of control is incredibly powerful. You could create different tiers of access—for instance, a free, slower connection for casual guests and a paid, high-speed option for power users. It also ensures that guest traffic is kept separate and can't interfere with your critical business systems.
This is also where legal compliance comes into play. Your portal must be transparent about what data you collect. Always include a clear link to your privacy policy and get explicit consent before a user connects. This isn't just about protecting your business legally; it’s about building trust.
In fact, the need for these kinds of compliant and secure access solutions is a major reason the captive portal market grew from USD 1.01 billion to USD 1.17 billion in just one year. You can read the full research on captive portal market trends to see just how fast this space is moving.
By following these steps, you can build a secure, effective, and user-friendly captive portal WiFi experience that works for both you and your visitors.
Common Questions About Captive Portal WiFi
Even after you get the big picture of what a captive portal WiFi system can do, a few practical questions almost always come up. Let's walk through the most common ones. Think of this as the final piece of the puzzle, clearing up any lingering doubts so you can feel confident about your next steps.
Can I Limit Internet Speed for Guest Users?
Yes, you absolutely can! In fact, this is one of the most valuable features of a professionally managed network.
Using a platform from a vendor like Cisco, you can easily set up "traffic shaping" rules. This means you control the bandwidth. You could offer a free tier with enough speed for basic browsing and a paid, high-speed option for guests who need more power. This is a game-changer for busy Retail or Corporate spaces, as it guarantees your guest WiFi won't ever bog down your essential business systems.
How Is a Captive Portal Different from a Standard WiFi Password?
That’s a great question because it cuts right to the core of what makes this technology so useful. A typical WiFi password (the technical term is a Pre-Shared Key, or PSK) is like having one key that you just keep copying for everyone. It's a single, simple security barrier, but it’s clumsy and not very secure.
A captive portal, on the other hand, acts as an intelligent gateway. It pulls users to a custom webpage where you can ask them to agree to terms, show them a promotion, or securely verify their identity. Modern Authentication Solutions push this even further. Methods like IPSK give each user their own unique credential, which offers far more security and individual tracking than a shared password ever could.
How Can I Make My Captive Portal Compliant with Privacy Laws?
Staying compliant isn't just a good idea; it's a must. Your captive portal login page has to be crystal clear about what data you're collecting and what you're doing with it.
Here are a few non-negotiable best practices:
- A Clear Privacy Policy: Your splash page must include an easy-to-find link to your privacy policy.
- Explicit Consent: Don't assume consent. Use a checkbox that requires users to actively agree before they connect.
- Opt-Out Options: Provide a simple way for users to say "no thanks" to marketing messages.
- Secure Data Handling: Any data you collect must be stored and managed securely.
Thankfully, most leading captive portal platforms are built from the ground up with features that make meeting these legal requirements much more straightforward.
A captive portal's security really comes down to how it's set up. The login page itself must use HTTPS to encrypt the connection. For the highest level of security—especially in Education or BYOD Corporate environments—strong authentication methods like IPSK (often managed with EasyPSK systems) or integration with secure identity providers are worlds better than a simple click-through page.
When you do it right, a captive portal becomes a secure, controlled, and fully compliant front door to your network. To get deeper into the technical side, you can explore our guide on modern user authentication techniques and see how they lock down network security.
Ready to transform your guest WiFi from a simple utility into a powerful business asset? At Splash Access, we specialize in creating seamless, secure, and engaging captive portal experiences on the Cisco Meraki platform. Discover how our solutions can work for you.