Hey there! If you've ever logged into the Wi-Fi at a coffee shop, hotel, or airport, you’ve almost certainly run into a special login page before you could start browsing. That's a captive portal for WiFi in action. Think of it as the digital doorman for a wireless network—it’s both a gatekeeper for security and a friendly welcome mat for guests.
What Is a WiFi Captive Portal Really?
At its heart, a captive portal is a web page that anyone new to a Wi-Fi network has to view and interact with before they get full internet access. It essentially "captures" your device's first attempt to go online and redirects you to this custom page. It might look like a simple login screen, but for a business, it's a remarkably powerful tool.
This is why top-tier network hardware from companies like Cisco and Meraki is built to integrate seamlessly with them. They help turn a basic connection into a secure, branded, and valuable interaction. This is where modern authentication solutions come in, giving businesses fine-grained control over who gets on their network and how.
How It Welcomes and Protects
Imagine your Wi-Fi network is an exclusive club. The captive portal acts as the friendly bouncer at the door, checking IDs and making sure everyone understands the house rules. This check-in can be as straightforward as clicking an "Accept Terms" button or as involved as requiring a specific username and password.
This functionality is incredibly useful across all sorts of industries:
- Retail: A shop can use its splash page to show off today’s specials right before granting access, turning a simple Wi-Fi connection into a direct marketing channel.
- Education: A university campus can make sure only students and faculty get online, using secure authentication to manage thousands of personal devices safely.
- Corporate BYOD: For companies with Bring Your Own Device policies, a portal can require employees to agree to security terms or authenticate their identity before connecting their personal phones or laptops to the corporate network.
A captive portal transforms your Wi-Fi from a simple utility into a strategic asset. It’s the first point of contact with a user, offering a chance to set expectations, reinforce your brand, and ensure a secure environment.
More Than Just a Password
Modern authentication takes security far beyond a simple shared password. Methods like IPSK (Identity Pre-Shared Key) and EasyPSK offer a much more secure way to manage access, which is especially important in crowded places like a school or a large office. Instead of one password that can be easily shared (and compromised), each user or device can be assigned its own unique key, dramatically improving network security.
As technology keeps moving forward, the latest captive portal solutions, like the new SplashAccess V3, offer even more advanced features and integrations to meet very specific business needs. This simple but effective technology is the bridge between offering free Wi-Fi and doing it in a smart, secure, and beneficial way.
How a Captive Portal Actually Works
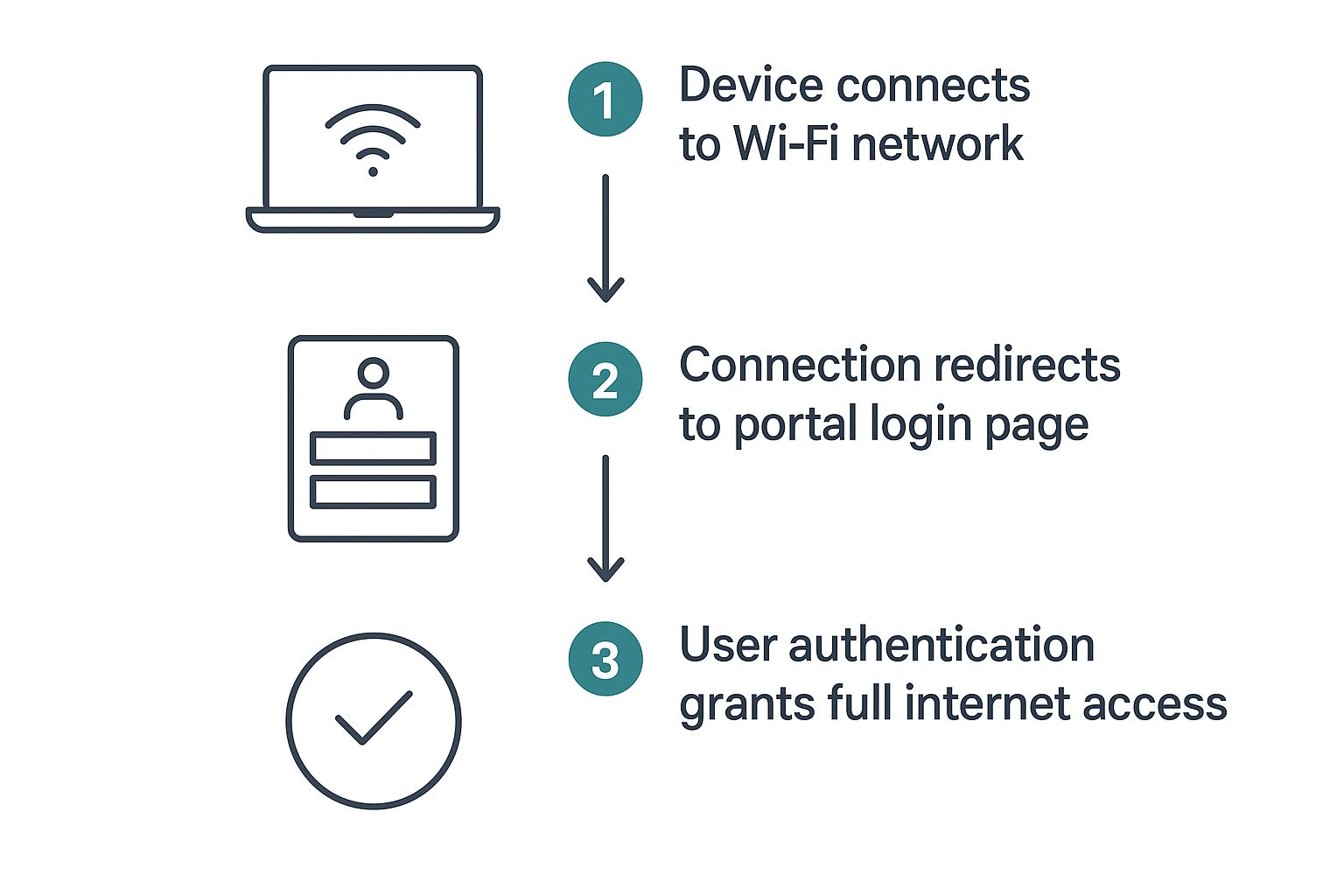
So, you’ve connected to a guest Wi-Fi network. What happens next? Let's pull back the curtain on the behind-the-scenes process that takes you from "connected" to actually browsing the web. It's a surprisingly simple sequence that keeps both you and the network safe, especially when managed with robust hardware from companies like Cisco and Meraki.
The moment your phone or laptop connects to the Wi-Fi signal, it's placed in a kind of digital waiting room. The network hardware essentially acts as a gatekeeper. When you open your browser and try to visit a website, the network intercepts that request. Instead of taking you to your homepage, it reroutes you to the captive portal login page.
This infographic lays out the simple, three-step flow of getting online through a captive portal.
As you can see, the journey is designed to be a quick but controlled checkpoint, ensuring every user is properly authenticated before getting full access.
Choosing Your Path to Authentication
Once you land on that portal page, you’ll see one or more ways to get online. This is where different authentication solutions come into play. The options can be tailored to fit the environment, whether it's a retail shop, a university campus for education, or a corporate BYOD (Bring Your Own Device) network.
Here are some common authentication methods you’ve probably seen:
- Simple Click-Through: The easiest path. You just have to agree to the Terms and Conditions to get online.
- Social Media Login: Using your Facebook or Google account for access. This is a popular option for businesses that want to understand their audience a bit better.
- Email or Form Fill: You’re asked to enter your email, name, or other details. It’s a fantastic way for venues to build marketing lists.
- Voucher or Code: Often used in hotels, where guests are given a unique code that grants them access for the duration of their stay.
This isn’t just about logging in; it’s a critical security and user verification step. The global captive portal market, valued at USD 1.06 billion, is expected to skyrocket to around USD 3.50 billion as more industries realize its power. If you're interested, you can discover more insights about the captive portal market growth and how it’s shaking up various sectors.
Advanced Security for Modern Needs
In places where security is a top priority, like in Education or Corporate BYOD settings, you need something more robust than a simple click-through. This is where advanced technologies like IPSK (Identity Pre-Shared Key) and solutions like EasyPSK really make a difference.
Instead of one shared password that everyone knows (and that can be easily compromised), IPSK gives each individual user or device a unique, personal password. Think of it as a personal keycard for the Wi-Fi network.
This method dramatically strengthens security for BYOD policies by making sure only authorized people can connect their personal devices. Once a user authenticates—whether with a simple click or a secure key—the portal grants their device full, unrestricted internet access. This seamless but tightly controlled process is what makes a captive portal for WiFi such an incredibly powerful and flexible tool.
Securing Your Network with IPSK Authentication
When you're setting up a captive portal for WiFi, not all login methods offer the same level of security. A simple, shared password might feel like the easy route, but it often opens the door to major security headaches. This is particularly true in busy BYOD Corporate settings or sprawling campuses in the Education sector, where a single password can be passed around, forgotten, or compromised, leaving your entire network exposed.
That’s why modern networks need a smarter, more secure approach to authentication. Enter Identity Pre-Shared Key, or IPSK.
Think of a standard WiFi password as a single master key to an apartment building. If one tenant shares it or loses it, the security for every resident is suddenly at risk. IPSK, on the other hand, is like giving every single resident their own unique key.
The Power of Unique Keys
The core idea behind IPSK is brilliantly simple: every user, or even every device, gets its own unique password to connect to the network. Solutions like EasyPSK make this incredibly easy to implement, especially on powerful networks built with Cisco Meraki equipment.
This one-to-one relationship between a key and a user delivers some serious advantages:
- Enhanced Security: If a key is ever compromised, you can instantly revoke access for that one user. There's no need to change the password for the entire company and deal with the fallout.
- Clear Accountability: Since every connection is tied to a specific identity, you have a crystal-clear picture of who is on your network at all times.
- Effortless Scalability: Managing thousands of unique keys is surprisingly simple with the right platform. This makes it a perfect solution for a university with 20,000 students or a fast-growing company.
With IPSK, you're not just granting blanket access; you're creating a secure, individual connection for every single person. It’s the new standard for managing network access in a world filled with personal devices.
IPSK in Action Across Sectors
In a Retail environment, you could use IPSK to give staff secure access for their devices, while customers connect through a separate guest login. But for Corporate BYOD offices and Education campuses, this level of control is essential. It's the best way to ensure only authorized students, faculty, or employees can connect their personal devices to the internal network.
When you integrate IPSK through a captive portal for WiFi, you get the best of both worlds: a user-friendly onboarding process combined with the rock-solid security of individual credentials. For organizations already using RADIUS servers, you can dive deeper into how IPSK with RADIUS authentication can create an even more robust and centralized security system, giving administrators unmatched control and making WiFi management simpler and safer.
Driving Business Value with Your WiFi Network
Let’s be honest, for a long time, guest WiFi was just an expense—a box to check. But what if that network could do more than just provide a connection? What if it could become a powerful engine for your business?
When you use a captive portal strategically, that’s exactly what happens. It stops being a simple security checkpoint and starts becoming a real asset that delivers measurable results. This is especially true when you're running on solid hardware from providers like Cisco and Meraki, which are built to handle these kinds of smart integrations.
The trick is to rethink that login screen. It isn't a barrier; it's your first digital handshake with every visitor who walks through your door. It’s a golden opportunity to shape their experience, show them what your brand is all about, and move your business goals forward.
Turning Connections into Customers
For Retail, the payoff is immediate. Imagine a shopper connects to your WiFi and is instantly greeted with a custom splash page showing a special offer or a digital coupon. By asking for an email to get online, you can build your marketing lists and grow your loyalty programs without lifting a finger. That direct line of communication is priceless. We dive deeper into this in our guide on how retailers can make the most of their wireless deployments.
In corporate offices, managing all the personal devices under BYOD policies can be a headache. A captive portal cleans things up. Before an employee connects their personal phone or laptop, you can require them to accept your company's terms of service. This simple step handles legal compliance and boosts network security. For an even tighter ship, advanced authentication solutions like IPSK or EasyPSK can assign unique keys to each device.
A captive portal allows you to transform your Wi-Fi from a passive amenity into an active engagement tool. It’s your chance to start a conversation with every user who connects.
Industry-Wide Growth and Opportunity
This shift from basic WiFi to strategic WiFi is happening across the board. The global captive portal market is booming, projected to grow at a compound annual growth rate (CAGR) of 13.9% and reach an estimated USD 6.20 billion.
What's fueling this growth? Think about all the places that need controlled, secure public WiFi: hotels, airports, and even schools. Industries like hospitality, Education, and transportation are all jumping on board. You can read the full research about the expanding captive portal market to see the trends behind this massive adoption.
At the end of the day, a well-designed captive portal for WiFi is a win-win. Your visitors get the easy, secure internet they expect, and your business opens up a brand-new channel for engagement and growth.
Captive Portals in the Real World
It’s one thing to talk about captive portals in theory, but where the rubber really meets the road is in how they perform out in the wild. This technology comes to life when you see it applied in different industries, solving unique problems and creating new opportunities.
The demand for these systems is exploding. The global market is on track to reach USD 2.20 billion in the near future, growing at a rate of nearly 13.9% each year. This isn't just a niche tool; major networking players like Cisco are implementing these authentication solutions everywhere, from airports to hospitals.
Secure Access in Education
Picture a sprawling university campus running on a Meraki network. Thousands of students, faculty, and staff are constantly trying to connect with their own laptops, tablets, and phones. A single, shared password for everyone? That’s a recipe for a security disaster.
This is where a captive portal for WiFi using IPSK (Identity Pre-Shared Key) becomes a game-changer. When a student registers for the semester, an automated system like EasyPSK gives them a unique key tied to their student ID. This key works for all their personal devices.
The result is a network where every single connection is secure and individually accounted for. When a student graduates or leaves, their access is cut off instantly without disrupting anyone else. It's a clean, safe, and manageable approach that fosters a perfect learning environment.
By assigning a unique digital key to each person, educational institutions can confidently embrace BYOD policies, knowing their network is protected from unauthorized access while providing a simple connection experience for users.
Boosting Engagement in Retail
Now, imagine you're walking into your favorite retail store. You see they offer free guest WiFi and connect your phone. Instead of just a password field, a beautifully designed splash page pops up, showcasing the store's latest promotions.
To get online, you simply enter your email. In doing so, you've also just joined their loyalty program. A moment later, a digital coupon for 15% off your purchase today appears right on your screen. You find what you need, use the coupon, and walk out with a great deal. The store made a sale and gained a direct way to keep you informed about future offers. That’s the magic of smart authentication solutions in Retail.
Streamlining Corporate BYOD
Let's shift to a modern company that embraces a BYOD Corporate policy. A new hire needs to connect their personal smartphone to the secure company network on their first day. The company’s captive portal acts as a secure onboarding checkpoint.
Before gaining full access, the employee is guided to a login page where they must read and accept the company's IT security policies. Once they agree, their device is authenticated, sometimes even scanned to ensure it meets basic security requirements. This simple step automates a critical security process, saving the IT team a headache and protecting the entire organization. If you want to dive deeper into these setups, feel free to explore our guide on the different captive portal solutions available.
Captive Portal Features by Industry Sector
Captive portals are not one-size-fits-all. Different industries tailor them to meet very specific objectives, from security and compliance to marketing and customer experience.
The following table breaks down how key sectors prioritize different features to achieve their primary goals.
| Industry Sector | Primary Goal | Key Feature Used | Example Application |
|---|---|---|---|
| Retail & Hospitality | Boost Sales & Loyalty | Social Login & Vouchers | Offering a 10% discount for a Facebook check-in. |
| Education (K-12/Uni) | Secure Network Access | Identity Pre-Shared Key (IPSK) | Assigning unique WiFi keys to students for BYOD. |
| Healthcare | Patient/Guest Experience | Tiered Access & ToS | Providing free basic internet for guests after they accept terms. |
| Corporate/Enterprise | Enforce Security Policies | BYOD Onboarding & RADIUS | Requiring employees to accept an AUP before connecting a personal device. |
| Public Venues | Data Collection & Ads | Email/Form Fill & Ads | A city park asking for an email address in exchange for WiFi access. |
| Transportation Hubs | User Management | Time/Bandwidth Limits | An airport offering 30 minutes of free high-speed WiFi per user. |
As you can see, the true value of a captive portal lies in its adaptability. By focusing on the right features, any organization can turn its guest WiFi from a simple utility into a powerful strategic asset.
Answering Your Top Captive Portal Questions
It's completely normal to have questions about how captive portals work, even though they're a powerful tool. Let's break down some of the most common queries with clear, practical answers so you feel confident about how this technology works.
Whether you're trying to connect at a Retail store, on a university Education campus, or in a BYOD Corporate setting, getting a handle on the basics makes all the difference.
Is Using a Public WiFi Captive Portal Safe?
This is a big one, and the honest answer is: it depends. The portal itself is designed as a security measure, but your personal safety also comes down to smart browsing habits.
A professionally set up captive portal, especially on robust hardware from brands like Cisco or Meraki, adds a solid layer of security by gatekeeping who can access the network. To take it a step further, many businesses implement advanced authentication solutions like IPSK or EasyPSK, which make sure every single user is properly verified before they can connect.
As a user, however, you should always stay vigilant on any public WiFi. Make it a habit to look for the little padlock icon (HTTPS) in your browser’s address bar. This confirms your connection to that specific site is encrypted. The portal secures the front door to the network, but you still need to be mindful of your own actions online.
Can a Captive Portal Slow Down My Internet?
Not really—this is a very common misconception. The captive portal is simply the digital doorway you walk through to get online. It isn't a constant filter that inspects or throttles your connection once you're authenticated.
Think of it like the front desk at a conference. You pause for a moment to show your badge and get checked in. Once you're past the desk and into the main hall, you're free to move about at your own pace. The front desk staff isn't following you around. Similarly, after you log in through the portal, your internet speed is dictated by the network’s overall capacity, not the login page you saw at the start.
How Do I Set Up a Captive Portal?
Putting together a professional captive portal for wifi requires a few key pieces to work in harmony. It starts with having the right network hardware. Modern routers and access points, like those from Cisco Meraki, are built with the necessary features to automatically redirect new users to a login page.
Then comes the software. This is where you design the look and feel of your splash page, decide on your authentication solutions (like social media logins, email capture, or even IPSK), and connect it to other marketing or operational tools. It’s the combination of capable hardware and intelligent software that creates the complete experience.
If you want to dive deeper into the nitty-gritty, our guide on how to set up guest WiFi walks you through the entire process from start to finish.
Ready to transform your guest WiFi from a simple utility into a powerful business asset? The team at Splash Access can help you create a secure, branded, and engaging captive portal experience on your Cisco Meraki network. Get started with Splash Access today.