A bring your own devices policy is basically the set of ground rules for letting your team use their own phones, laptops, and tablets for work. The whole point is to find that sweet spot between the convenience of using a device you know and love, and the absolute necessity of keeping company data locked down. It’s all about enabling flexibility without opening the door to security nightmares.
Why a Solid BYOD Policy Is Non-Negotiable

Let's be real—your team is already checking emails and jumping on Slack with their personal phones, whether you have a formal policy or not. The question isn't if you should allow it, but how you're going to manage it safely. A well-thought-out bring your own devices policy isn't just a "nice-to-have" anymore; it's the bedrock of any modern, secure, and productive workplace.
We see this everywhere. In education, a BYOD policy means students and staff can connect to resources from anywhere on campus. For a retail business, it puts real-time inventory data in the hands of sales associates on the floor. And in any corporate setting, it’s a huge factor in keeping employees happy and operations running smoothly.
Balancing Freedom with Control
The best BYOD policies aren't about saying "no." They're about creating a framework that gives employees the freedom they want while giving your IT team the control they need. This is where a modern network setup makes all the difference.
For example, solutions from providers like Cisco Meraki are designed to create a secure bubble where personal and work data can live on the same device without mixing. This is all done through smart security protocols that work behind the scenes, so your team doesn't even notice them.
The core idea is simple: you're creating separate, secure lanes for personal and company traffic on your network. An employee's weekend photos shouldn't be on the same digital highway as your confidential financial reports.
The Power of Smart Authentication
A huge piece of the security puzzle is controlling who gets onto your network in the first place. This is where solid Authentication Solutions come into play. Forget handing out a single Wi-Fi password that everyone shares (and that inevitably gets compromised).
Smarter methods are the way to go:
- Captive Portals: This is your network’s front door. When someone tries to connect, they land on a branded splash page where they have to agree to your terms before getting access.
- IPSK and EasyPSK: Think of Identity Pre-Shared Keys (IPSK) or EasyPSK as a unique, personal Wi-Fi password for every single user. When an employee leaves, you just turn off their key. No need to change the password for the entire company.
The data backs this up. Research shows that while 95% of organizations allow personal devices to connect to their networks, a startlingly low 39% actually have a formal policy in place to manage them. That gap is a massive security risk waiting to happen. With the global BYOD market projected to hit USD 157.3 billion due to the demand for work flexibility, getting a policy in place has never been more important. Discover more insights about BYOD trends.
The Building Blocks of an Effective Policy
Crafting a bring your own devices policy that actually works is about more than just filling out a template. It's about creating a practical framework that sets clear boundaries for acceptable use, spells out who owns what data, and establishes non-negotiable security standards right from the start. Getting this foundation right ensures everyone is on the same page.
The explosive growth of the BYOD market really underscores why this is so critical. The global market has already hit around USD 487.24 billion and is on track to blow past USD 571.68 billion very soon. This isn't just a fleeting trend; it's a fundamental shift in how we work, fueled by the demand for flexibility and powerful mobile tech. As more businesses make this move, a solid policy becomes absolutely essential. You can explore the expanding global BYOD market to see just how it’s reshaping IT strategies everywhere.
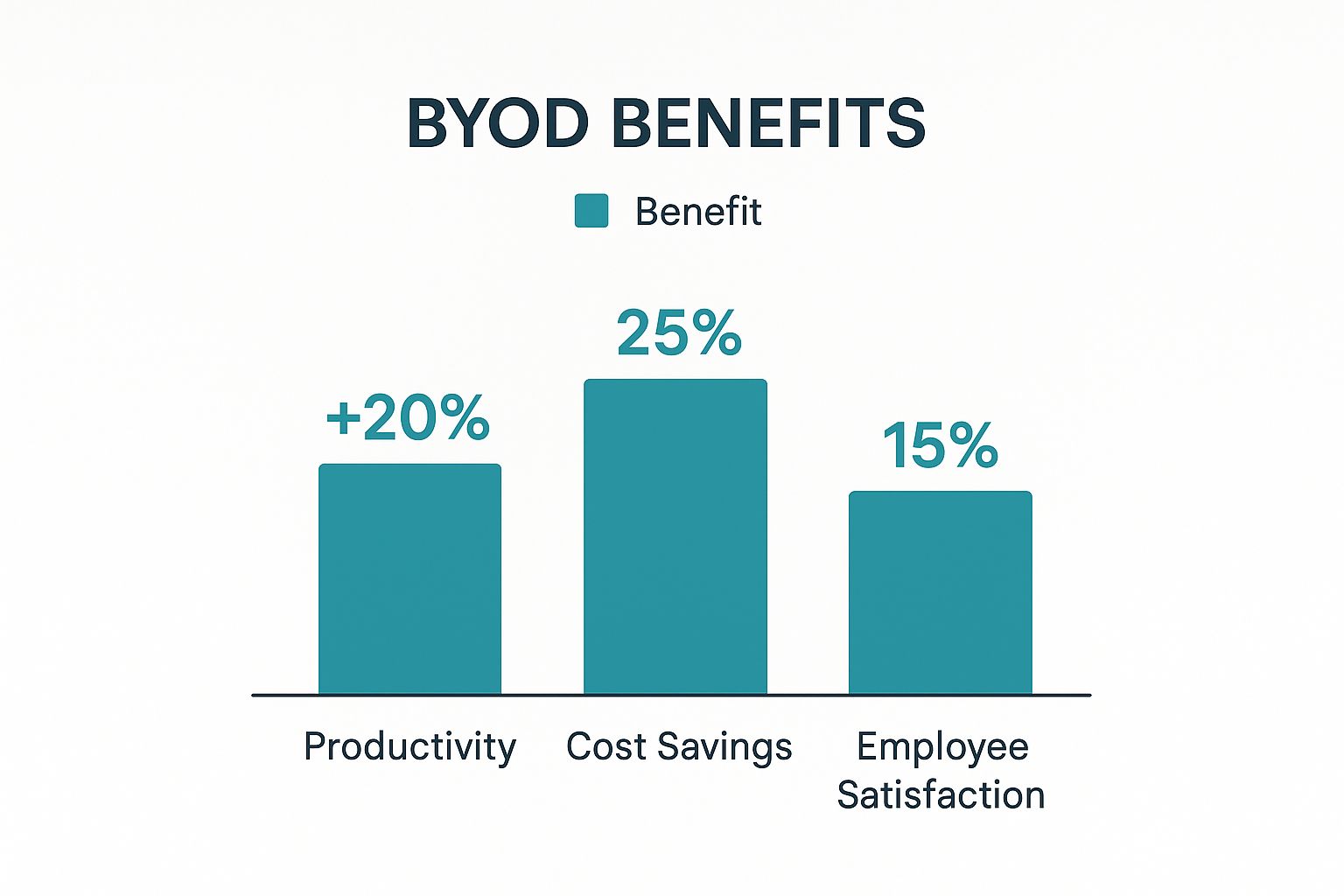
This infographic lays out some of the powerful benefits driving this shift, from major productivity gains to real cost savings and happier employees.
As you can see, the numbers tell a compelling story. A well-run BYOD program is a clear win-win for both the company and its people.
Defining Acceptable Use and Devices
First things first: you need to decide which devices get a green light on your network and what they can actually be used for. A one-size-fits-all approach is a recipe for disaster because every industry faces its own unique security and operational challenges.
Think about it. A corporate office might allow laptops and smartphones to tap into sensitive company servers. But in an education setting, you'd likely want to restrict student devices to a heavily filtered guest network. Meanwhile, a retail business must lock down its network to ensure personal devices on the sales floor can never touch the payment processing systems.
Your policy needs to spell out the following specifics:
- Approved Devices: Get granular. List the types of devices (smartphones, tablets, laptops) and the operating systems (iOS, Android, Windows) you’re prepared to support.
- Prohibited Activities: Be explicit about what’s off-limits. This includes things like installing unapproved software or accessing illegal content while connected to the company network.
- Data Access Limits: Clearly define which company applications and data sets are accessible to different user roles when they’re on their personal devices.
Setting Crystal-Clear Security Expectations
This is where your policy gets its teeth. Without robust security rules, you’re essentially leaving the front door wide open. Modern Authentication Solutions and dependable network hardware, like the systems offered by Cisco Meraki, are instrumental in making sure these rules are actually enforced.
At a minimum, your policy must include these security requirements:
- Password Protection: Mandate strong, unique passwords and auto-screen locks on every single device. No exceptions.
- Software Updates: Require users to keep their operating systems and applications up-to-date. This is your first line of defense against known security holes.
- Secure WiFi Connection: Insist that employees connect only through secure, approved Wi-Fi networks. This often means using unique credentials like IPSK or EasyPSK, which are far more secure than a single shared password for everyone.
Your policy must make it non-negotiable: any device connecting to your network has to meet these minimum security standards. A Captive Portal is a fantastic tool for this, as it can automatically check a device for compliance before it grants any network access.
Clarifying Data Ownership and Privacy
Navigating the line between company and personal data is one of the trickiest parts of any BYOD policy. You need your team to trust that their personal privacy is respected, but the company also needs assurance that its intellectual property is safe.
Your policy must state, in no uncertain terms, that the company has the right to manage and—if necessary—remotely wipe corporate data from a personal device. At the same time, it should reassure employees that their personal photos, messages, and files will remain untouched. Striking this balance is key to building trust and encouraging people to opt into the program.
If you’re curious about the nuts and bolts of how network traffic is managed and protected, learning what a stateful firewall is and how it works offers some great insights.
Key Policy Components for Different Sectors
To help you tailor your policy, the table below breaks down the key components with specific considerations for different environments. What's crucial for a school is different from what a retail store or a large corporation needs.
| Policy Component | Education Sector Focus | Retail Sector Focus | Corporate Sector Focus |
|---|---|---|---|
| Acceptable Use | Focus on preventing access to inappropriate content and protecting minors. | Restrict access to POS systems and payment card data. | Define access to sensitive intellectual property and client data. |
| Device Security | Mandate basic screen locks and up-to-date antivirus. | Require strong passwords and prohibit rooted/jailbroken devices. | Enforce multi-factor authentication (MFA) and encryption. |
| Data Ownership | Clearly separate school-related work from personal student data. | Ensure customer data is never stored on personal devices. | Assert company ownership over all work-related data and files. |
| Network Access | Use content filtering and bandwidth limits on a guest network. | Segment network to isolate POS terminals from general Wi-Fi. | Require VPN for remote access to internal resources. |
| Enforcement | Use a captive portal for policy acceptance before network access. | Implement Mobile Device Management (MDM) for security compliance. | Use MDM for remote wipe capabilities and app management. |
This breakdown should give you a solid starting point for drafting a policy that is not only comprehensive but also perfectly suited to your organization's unique operational needs and risk profile.
Securing Your Network for BYOD Success
A perfectly worded bring your own devices policy is a fantastic start, but let's be honest—it's only half the battle. Without the right tech to back it up, your policy is just a well-intentioned document collecting dust.
This is where you move from theory to practice. You need to prepare your network to handle the unique security challenges that personal devices bring to the table. The goal is to turn your rules into automated, enforceable actions that genuinely keep your data safe.
The core idea is simple: create a secure environment where personal and company data can coexist on the same device without ever crossing paths. Think of it like a digital highway. You wouldn’t want trucks carrying sensitive cargo stuck in the same traffic jam as personal cars on a weekend joyride. You need dedicated, secure lanes for different types of traffic.
The Power of Network Segmentation
One of the most effective strategies I’ve seen for securing a BYOD environment is network segmentation. In plain English, this just means carving up your network into smaller, isolated sections. It ensures that a personal device connecting to your Wi-Fi can't accidentally wander into sensitive areas like your financial servers or customer databases.
It’s an essential practice for any modern business.
- In Education, it keeps student devices on a separate network from faculty and administrative systems.
- For Retail businesses, it isolates point-of-sale (POS) terminals from the free guest Wi-Fi you offer shoppers.
- In a BYOD Corporate setting, it protects intellectual property by limiting personal device access to only the necessary applications.
Fortunately, you don't need to be a network guru to pull this off. Modern solutions from providers like Cisco Meraki are designed to simplify this process, letting you create and manage these separate zones with just a few clicks from a central dashboard.
Demystifying Mobile Device Management
Another term you'll hear thrown around is Mobile Device Management (MDM). Don't let the technical name intimidate you; its purpose is incredibly practical. MDM software gives your IT team the ability to manage and secure devices enrolled in your BYOD program, no matter where they are.
Think of MDM as your central command center for device security. It allows you to:
- Enforce security policies automatically (like requiring strong passcodes).
- Push necessary apps and configurations to devices.
- Selectively wipe only corporate data if a device is lost or stolen, leaving personal photos and files completely untouched.
That last point is crucial for getting employee buy-in. It shows you're serious about protecting company assets without overstepping into their personal privacy. It's a delicate balance, but a good MDM makes it achievable.
The investment in this space is exploding. The BYOD security market was recently valued at USD 73.0 billion and is projected to skyrocket to USD 210.4 billion. This surge is directly tied to the rise of remote work and the urgent need to protect company data on personal devices.
Your First Line of Defense: Authentication
Before any device gets a green light, it needs to be properly identified. This is where strong Authentication Solutions become your best friend. Relying on a single, shared Wi-Fi password for everyone is a major security hole just waiting to be exploited.
Instead, modern authentication methods create a much more secure and user-friendly experience. A Captive Portal, for instance, acts as a digital welcome mat. It’s the first thing users see when they connect, requiring them to accept your terms of use before getting online.
For even tighter security, technologies like IPSK (Identity Pre-Shared Key) or EasyPSK are game-changers. Instead of one password for the whole company, each user or device gets its own unique security key. If an employee leaves or a device goes missing, you just revoke that one key without disrupting anyone else. These individual keys offer a huge leap in security.
Of course, these BYOD-specific measures are part of a bigger security picture. For a broader look at keeping your organization safe, it's worth exploring these DevOps security best practices. By combining network segmentation, MDM, and smart authentication, you build a layered defense that transforms your BYOD policy from a document into a dynamic, secure reality.
Mastering Access with Smart Authentication
So, you've segmented your network and your policy is taking shape. Great. Now for the million-dollar question: how do you actually control who gets on your network and what they can do once they're there? This is where your bring your own devices policy goes from being just a document to a living, breathing system. It all comes down to smart authentication.
Let's be honest, the days of scribbling a single Wi-Fi password on a whiteboard are over. That's a huge security risk, especially in a busy corporate, retail, or education setting. Modern Authentication Solutions offer a much smarter, safer, and more user-friendly way to handle things.
The Friendly Digital Front Desk
Think of a Captive Portal as the digital doorman for your Wi-Fi network. The moment someone tries to connect with their personal phone or laptop, they land on a branded page. This page isn't just for show; it's your first layer of control.
Before getting online, users have to accept your terms and conditions—the very rules you just laid out in your BYOD policy. It's a simple but critical step that ensures everyone has acknowledged their responsibilities. For IT teams, platforms like Cisco Meraki make setting up these portals surprisingly easy, letting you create a professional and secure onboarding experience without a team of developers.
Moving Beyond the Single Password
The real game-changer for BYOD security is getting rid of the shared password for good. This is where technologies like IPSK (Identity Pre-Shared Key) and EasyPSK come in, and they are brilliant.
Imagine giving every single user their own unique, private key to the Wi-Fi. That's exactly what IPSK does.
- For Students: Each student gets a personal key that grants access to the campus learning portal but keeps them out of administrative systems.
- For Retail Staff: An employee’s key connects them to inventory apps but locks them out of sensitive payment processing networks.
- For Corporate Teams: Different departments get keys with tailored access, ensuring the finance team's devices can't wander onto engineering servers.
This completely changes your security posture. If an employee leaves or a student loses their device, you don't have to trigger a network-wide password change. You just revoke that one person's key. The threat is neutralized instantly.
This level of granular control is a massive step up for any bring your own devices policy. It blends serious security with the kind of straightforward management that IT departments dream about. For a deeper look, our guide on various user authentication techniques breaks down how these different methods stack up.
Integrating with Your Existing Systems
The best authentication tools don't work in isolation; they plug right into the systems you already rely on. To really nail down who gets access and what they can do, you should look into advanced authentication and provisioning solutions. This approach lets you sync your network access controls directly with your main user directory, whether that's Azure AD, G Suite, or something else.
This kind of integration means access management becomes almost automatic. Add a new employee to your directory, and a network key can be created for them. When they leave, their access is cut off everywhere, all at once. It saves a ton of administrative time and, more importantly, closes the security gaps that come from human error.
Why Smart Authentication Is Non-Negotiable
Relying on old-school security is just too risky. We know that 81% of organizations have been hit by attacks aimed at users, like phishing and malware. A single compromised shared password can give an attacker the keys to the entire kingdom.
By using a layered approach with Captive Portals and unique keys like IPSK, you build a powerful defense that's both effective and easy to manage. This isn't just a "best practice"—it's an essential ingredient for any successful and secure BYOD Corporate policy. It makes sure the right people get the right access on the right devices, every single time.
Rolling Out Your New BYOD Policy
You’ve put in the hard work. The policy is drafted, your network is secure, and the right Authentication Solutions are in place. Now for the most critical part: introducing the new bring your own devices policy to your team.
A successful launch is much more than just sending a company-wide email. You have to sell it. Think of it as an internal marketing campaign. If your team sees this as just another set of restrictive rules, they'll look for workarounds. But if they understand the "why" behind it—more flexibility, better security for everyone—they’ll get on board willingly.
Announce It With a Positive Spin
The initial announcement sets the tone for everything that follows. Ditch the dry, legal-sounding jargon. Instead, frame the policy around the benefits it offers to the people who will be using it every day.
Keep the focus on the upsides:
- More Flexibility: Emphasize their newfound freedom to work from anywhere on the devices they already love.
- Increased Productivity: Point out how using familiar tech can make their jobs easier and more efficient.
- Shared Responsibility: Frame security as a team sport where everyone plays a part in protecting company and personal data.
A positive message turns what could be a tense transition into a genuine workplace upgrade. This approach is effective everywhere, from a bustling Retail environment to a sprawling Education campus or a fast-moving BYOD Corporate setting.
The goal is to make employees feel like partners in this shift. This isn't something being done to them; it's a new framework being built with them for a better, more modern way of working.
Run Q&A Sessions to Build Trust
No matter how well you write the policy, people will have questions. An email just can’t cover every "what if" scenario, which is why live Q&A sessions (in-person or virtual) are non-negotiable. This is your chance to tackle concerns head-on, clear up confusion, and prove you're listening.
Be ready for the tough questions about privacy, data usage, and what happens if a device is lost or stolen. Transparency here is huge. It builds trust and dismantles resistance before it can even start. These sessions are also a great time to give a quick, non-technical overview of how security tools like Captive Portals or unique Wi-Fi keys (IPSK and EasyPSK) actually make their lives simpler and their connections safer.
Create Simple, Visual User Guides
When it comes to the technical side of things, an IT manual won't cut it. You need simple, step-by-step guides for getting devices enrolled. Make them visual, easy to skim, and create separate versions for different operating systems like iOS and Android.
A great user guide should feel effortless and include things like:
- A friendly intro explaining why they're enrolling their device.
- Clear screenshots pointing to exactly where to tap and what to enter.
- A quick "how-to" for getting onto the new secure Wi-Fi network.
The process should feel less like a chore and more like a quick setup. The same principles that make for a great guest Wi-Fi experience apply here—keep it simple. For some ideas on creating a frictionless connection process, check out our guide on how to set up guest WiFi.
By blending positive communication with open dialogue and practical help, you ensure your bring your own devices policy isn't just launched—it's embraced. This thoughtful approach builds a culture of shared security and empowers your team to be your greatest asset.
Answering Your Top BYOD Policy Questions
Even the most carefully planned bring your own devices policy will spark questions. It’s a natural part of the process. I've worked with countless organizations in Education, Retail, and the corporate world, and a few key questions always come up. Let's get them answered.
What's the Biggest Mistake Companies Make with a BYOD Policy?
Honestly, the most common pitfall I see is creating a beautiful policy on paper and then just… stopping. They fail to back it up with the right technology to actually enforce it. A policy is just a document until you implement the technical controls to make it real. If you can’t automatically enforce your security rules, you're just hoping people follow them, and hope is never a solid security strategy.
Another huge mistake is making the policy so complicated or restrictive that it drives users crazy. When people get frustrated, they find workarounds—and those workarounds are almost always insecure. You have to find that sweet spot: a policy that delivers robust security but feels effortless for the user. This usually comes down to smart Authentication Solutions that do the heavy lifting in the background.
The best BYOD policies are practically invisible to the end-user. They lean on tools like MDM and automated network access controls, often from vendors like Cisco and Meraki, to enforce the rules without creating friction.
How Do Captive Portals and IPSK Actually Improve Security?
These two work hand-in-hand to create a secure onboarding experience that’s also incredibly simple for the user.
Think of a Captive Portal as the friendly digital front desk for your network. It’s the first thing a new device sees, asking the user to accept your terms before connecting to the Wi-Fi. It’s a simple but powerful first step to make sure everyone is on the same page from the get-go.
Once they've agreed, something like IPSK (Identity Pre-Shared Key) or EasyPSK takes over. Instead of giving everyone the same Wi-Fi password—a huge security risk—you assign a unique, private password to each individual user or even each specific device.
This approach is a massive security upgrade. If an employee leaves or a phone gets lost, you can instantly revoke that one key without disrupting anyone else on the network. No more "everyone change the password" fire drills. For a deeper dive, understanding the technical differences between WPA2-Personal vs. Enterprise security can really clarify why this method is superior.
What Happens If an Employee Loses a Personal Device?
This is a scenario your bring your own devices policy absolutely must cover. A good policy lays out a clear, simple incident response plan that everyone knows ahead of time.
The process should be straightforward:
- Report It Immediately: The employee needs to know to alert the IT department the moment they realize a device is lost or stolen. Time is critical.
- Trigger a Selective Wipe: Using a Mobile Device Management (MDM) tool, your IT team can then remotely wipe only the corporate data—the work apps, company email, and sensitive files.
This selective wipe capability is a cornerstone of any modern BYOD program. It protects the company's information while respecting the employee’s privacy by leaving their personal photos, messages, and data completely untouched.
Should BYOD Rules Be Different for Education vs. Retail?
Absolutely. A one-size-fits-all policy just doesn't work because every industry has its own unique risks and operational needs. You have to tailor the policy to your specific environment.
For instance, in Education, the policy needs to create different levels of access for students, faculty, and guests. You'll likely need strong content filtering, especially for younger users.
In Retail, the top priority is locking down the point-of-sale network to protect customer payment data. You need to ensure an employee's personal phone on the shop floor can't touch those critical systems. A corporate setting, on the other hand, will be far more focused on protecting intellectual property and confidential client data.
A successful bring your own devices policy isn't a one-and-done project; it’s an ongoing process. By building a solid framework, communicating clearly, and using the right tech, you can create a secure and productive environment that works for everyone.
Ready to implement a seamless and secure Wi-Fi experience? Splash Access integrates with Cisco Meraki to deliver powerful captive portals and advanced authentication solutions like IPSK, making your BYOD policy simple to manage and enforce. Explore how Splash Access can transform your network today.